Similar User

@fbpierazzi

@CySecClub_UPM

@Secure_ICS_OT

@NawaF_Aloufi

@maurapintor

@_Sagar_Samtani

@MHMDQi

@ShreeJananiS

@mhd_raef

@ita7min

@ICS_AMS

@mshehris

@wairimu1maina

@rlfbrt

@m3atta
To the world who turned a cold shoulder, Gazan people burned alive in their tents tonight.
LLMs rely on adversarial testing or "AI red teaming," but what does it involve? Who should do it? Join our #CSCW2024 with experts including RT leads (@_lamaahma and @ram_ssk), @marylgray, and @bshestakofsky Apply to join: bit.ly/airedteam Paper: arxiv.org/abs/2407.07786
Oxford surgeon Professor Nick Maynard on what he saw in Gaza:

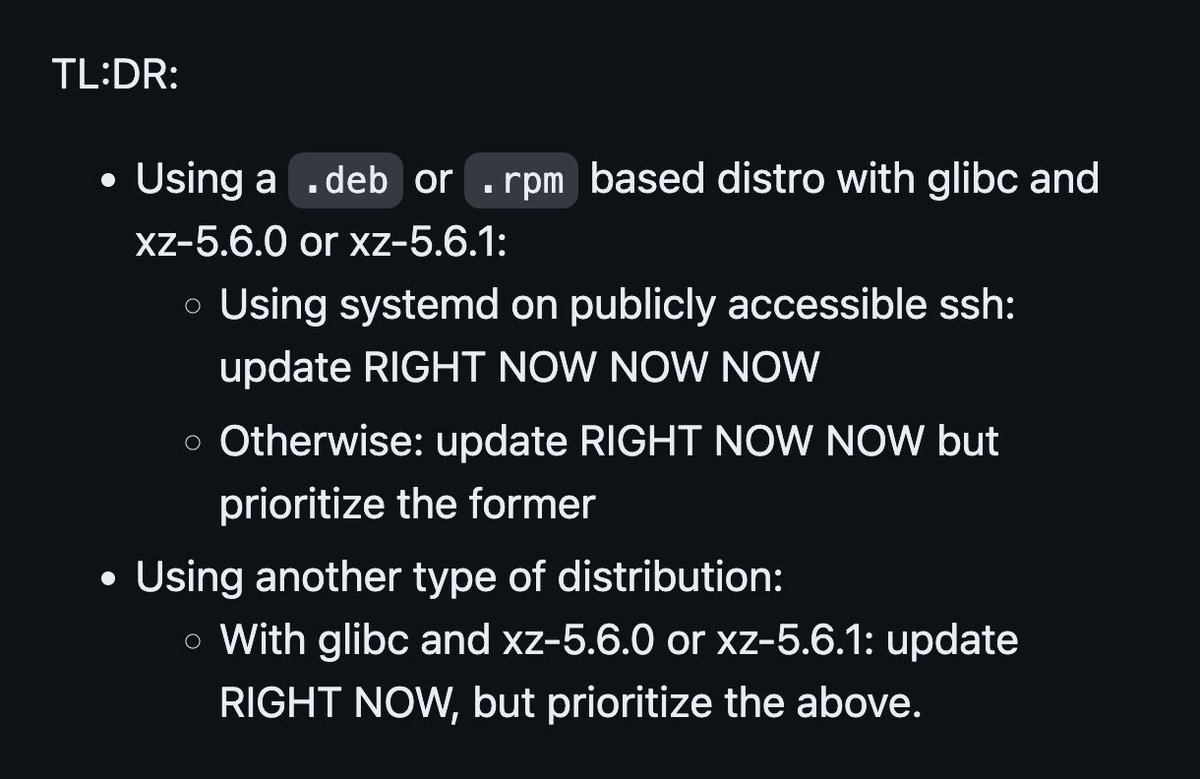
FAQ on the xz-utils backdoor | by Sam James gist.github.com/thesamesam/223… #XZ #XZutil
cocomelonc.github.io/persistence/20… Ramadan Mubarak! Next post on my blog #hacking #cybersecurity #infosecurity #malware #malwaredev #malwareanalysis #redteam #blueteam #purpleteam #cyberwarfare #apt #cybercrime #persistence #winapi #windows #research
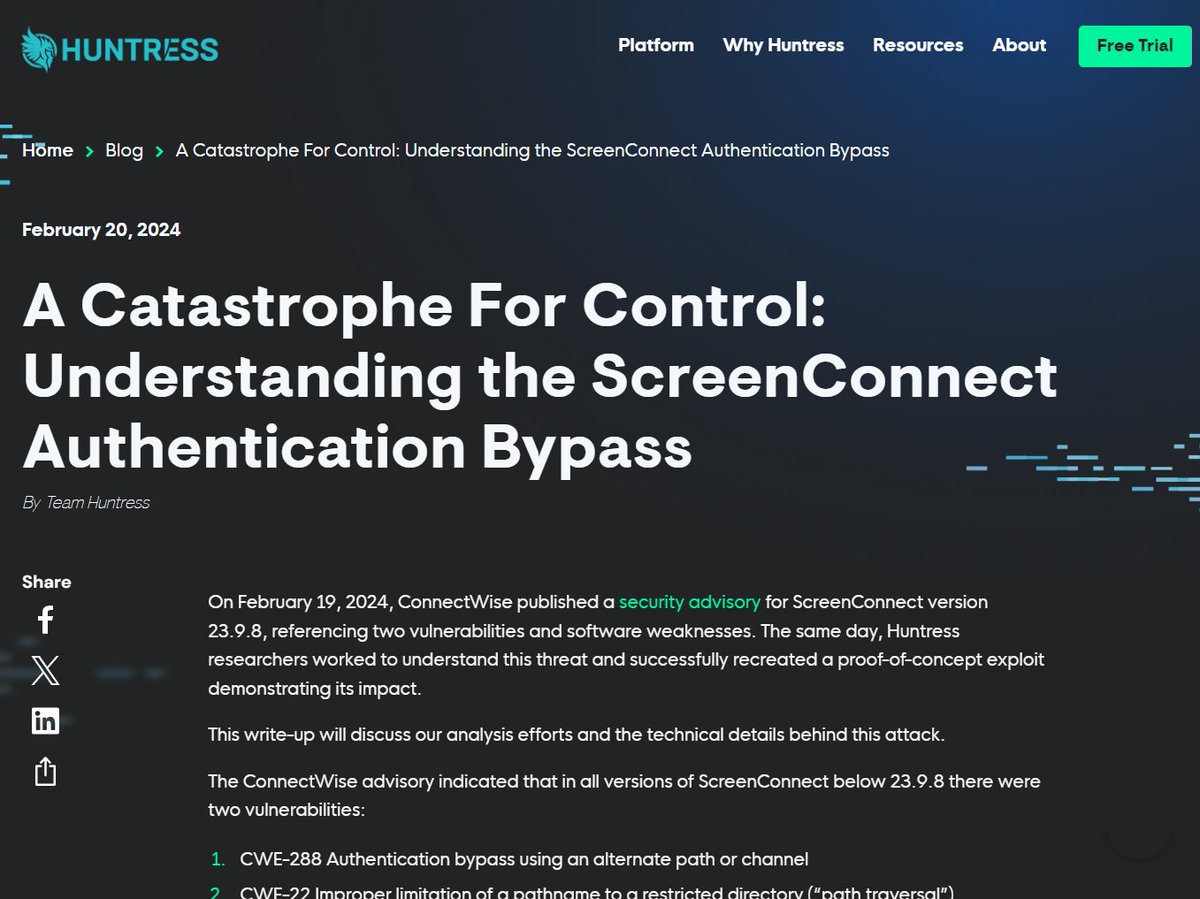
Lotta chatter around #ScreenConnect vulnerabilities now as folks are getting spun up. Fellow @HuntressLabs researchers and I were up all night to recreate the auth bypass and RCE exploit. I'm not a huge fan of giving a PoC to threat actors, but I do dig snazzy video demos 😜
Well, now that other firms have publicly shared the proof-of-concept, and in-the-wild exploitation is already happening... we feel we aren't adding any risk and are comfortable sharing our analysis. @HuntressLabs writeup on #ScreenConnect vulnerabilities: huntress.com/blog/a-catastr…
Our deep-dive for the recent #ConnectWise #SecureConnect authentication bypass vulnerability: horizon3.ai/attack-researc…
ConnectWise has shared publicly that there are users affected by the recent #ScreenConnect vulnerabilities (authentication bypass->remote code execution), confirming in-the-wild exploitation. They share 3 observed IPs exploiting & installing persistence: connectwise.com/company/trust/…

#ESETresearch has documented a growing series of OilRig downloaders using legitimate cloud service providers for C&C communication, all deployed against a small group of especially interesting, repeatedly victimized targets in Israel. welivesecurity.com/en/eset-resear… @zuzana_hromcova 1/7
cocomelonc.github.io/book/2023/12/1… Alhamdulillah, I finished writing this book today. The proceeds from the sale of this book will be used to treat childs. #cybersec #cybersecurity #cybercrime #malware #malwareanalysis #ransomware #hacking #purpleteam #research #threatintelligence #APT
A few weeks ago I started to rewrite the Havoc Framework from scratch for various reasons. Redesigning the server architecture, RESTful API driven, and the client fully scriptable using Python (commands, events, UI). I wanna fully rewrite everything in the next ~2 months [1/11]
Today at #BHEU, Microsoft researchers are sharing info about the open-source Microsoft ICS forensics framework, as well as new Rockwell RSLogix and Omron tools that defenders can use and customize for detecting suspicious artifacts in ICS environments: msft.it/6018iumFC
📘 Cyberattacks on UK Critical Infrastructure 🇬🇧 CTI GitHub Repo - OSINT collection of reports related to cyberattacks and campaigns against UK critical national infrastructure (CNI) for case studies #cybersecurity #infosec #blueteam #cti #threatintel github.com/BushidoUK/UK-C…

Want to start learning about software exploitation? Then check my FREE course below. More than 12h+ of recorded hands-on content and all the labs, slides, etc are published completely FREE! The course start with the very basics. #Cybersecurity #exploit youtube.com/playlist?list=…

We’ve published a whitepaper with @NCA_UK outlining the tactics of the cyber crime groups behind ransomware attacks on UK organisations. 🧵

I've started challenging the very term "technical." There's no one way to be "technical." Someone who codes might know jack about network forensics. There are so many "technical" areas...and understanding how technologies work at a high level and communicating that is technical!
Industrial Control Systems: Engineering Foundations and Cyber-Physical Attack Lifecycle cyberphysicalsecurity.info by Dr.Marina Krotofil
📢The Microsoft AI Red Team is hiring across all levels! Your area can be Adversarial ML or Responsible AI or Pen testing, and you will fit right in! Questions? DM always open Junior: jobs.careers.microsoft.com/global/en/job/… Senior: jobs.careers.microsoft.com/global/en/job/… Principal: jobs.careers.microsoft.com/global/en/job/…
United States Trends
- 1. $cuto 7.423 posts
- 2. Happy Thanksgiving Eve 2.879 posts
- 3. #MigglesArmy 1.827 posts
- 4. #sociprovider N/A
- 5. Custom 70,3 B posts
- 6. Dodgers 57,8 B posts
- 7. #WednesdayMotivation 4.461 posts
- 8. Good Wednesday 24,8 B posts
- 9. Wrecking 13,6 B posts
- 10. #27Nov 3.253 posts
- 11. Landman 3.352 posts
- 12. Sharon Stone 23,1 B posts
- 13. DB Cooper 3.028 posts
- 14. Hump Day 12,7 B posts
- 15. #FayeYokoGQMOTY 267 B posts
- 16. Cutoshi 1.219 posts
- 17. DESTINY COUPLE FAYEYOKO 259 B posts
- 18. Snell 37,9 B posts
- 19. Happy Hump 8.175 posts
- 20. Kerry 25,1 B posts
Who to follow
-
 Fabio Pierazzi
Fabio Pierazzi
@fbpierazzi -
 Cybersecurity Club || نادي الأمن السيبراني
Cybersecurity Club || نادي الأمن السيبراني
@CySecClub_UPM -
 Secure ICS OT
Secure ICS OT
@Secure_ICS_OT -
 NawaF ..💙
NawaF ..💙
@NawaF_Aloufi -
 Maura Pintor
Maura Pintor
@maurapintor -
 Sagar Samtani
Sagar Samtani
@_Sagar_Samtani -
 Mohamad Kontar
Mohamad Kontar
@MHMDQi -
 Shree Janani
Shree Janani
@ShreeJananiS -
 Mohammed Raef
Mohammed Raef
@mhd_raef -
 Haitham
Haitham
@ita7min -
 Abdul Malik Sardar
Abdul Malik Sardar
@ICS_AMS -
 Mohanned | مهنّد
Mohanned | مهنّد
@mshehris -
 wairimu_maina
wairimu_maina
@wairimu1maina -
 Ralf
Ralf
@rlfbrt -
 mohamed atta
mohamed atta
@m3atta
Something went wrong.
Something went wrong.