Similar User

@CHANCHONHIM2

@linyiyi94
btw these large scary math symbols are just for-loops

How Component Object Model (COM) works. #ThreatHunting #DFIR #Windows #Microsoft

How To Pick The Right Docker Image For Your Node.js App 👇 - Use an LTS release - Avoid bloated images - Balance simplicity/security All mainstream image candidates with the usage advice on a single diagram:

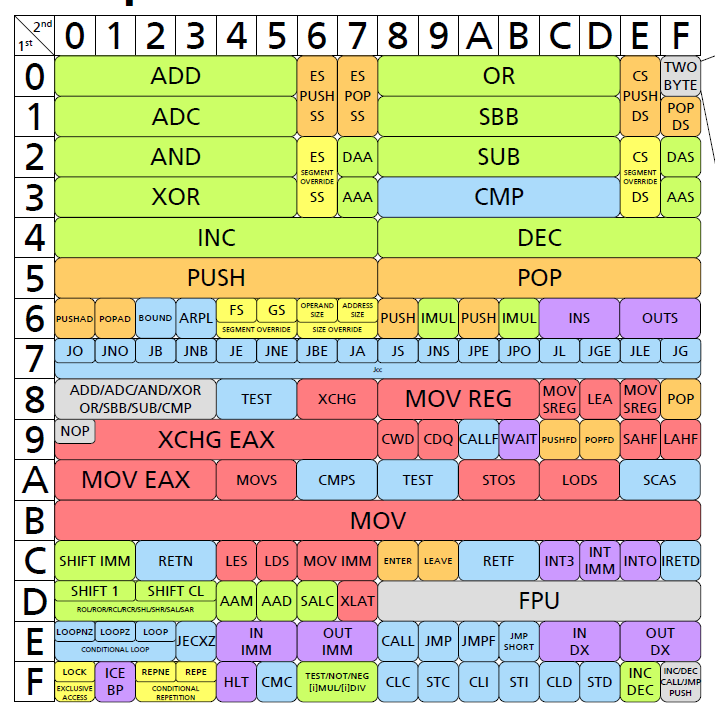
I've just discovered this amazing document showing super clearly the relation between the opcode and the instruction 🤯 pnx.tf/files/x86_opco…
Binary Representations of Numeric Values Cheat Sheet

Bayes’ theorem, clearly explained:

Linux Control Groups (cgroup v2) cheat sheet 🧐 CPU, memory, and other resources of regular Linux processes, systemd daemons, Docker containers, and Kubernetes pods are controlled with exactly the same kernel mechanism - cgroup. The main cgroup concepts on a single diagram 👇

I wish I had this cheatsheet for Apache Flink earlier...

OpenAI 前首席科学家 Ilya sutskever 大佬分享的约 30 篇顶级 AI 研究论文清单爆火🔥💥,据说看完可以掌握当前人工智能最为关键的 90% 的知识! 包括 Transformer 架构、RNN、LSTM、神经网络复杂度、计算机视觉等领域 清单地址:arc.net/folder/D0472A2… 以下是核心论文介绍:👇

I’ve spent the past seven years mapping out a significant chunk of the math genome. The mathematical hierarchy is a vast and profoundly interconnected web of topics, where advanced topics depend intricately on more basic ones, which in turn rest on even more fundamental ideas.…

Linux Page Cache for SREs: syscalls, kernel internals and knobs, perf, vmtouch, cgroup v2, LRUs, writeback, mmap() tricks and much more in my series of articles biriukov.dev/docs/page-cach…

Best way we could explain it 🤣

A visual overview of the world's 10 largest public semiconductor companies' market caps: $NVDA $TSM $AVGO $ASML $TXN $ARM $AMAT $QCOM $AMD

llm.c by Hand✍️ C programming + matrix multiplication by hand This combination is perhaps as low as we can get to explain how the Transformer works. Special thanks to @karpathy for encouraging early feedback and @7etsuo for helping me understand the pragma magic. I hope…
Cybersecurity 101 in one picture. 1. Introduction to Cybersecurity 2. The CIA Triad 3. Common Cybersecurity Threats 4. Basic Defense Mechanisms 5. Cybersecurity Frameworks – Subscribe to our weekly newsletter to get a Free System Design PDF (158 pages): bit.ly/3KCnWXq

Digging the Gum choose TUI. These are the pickers you'll get when installing Omakub now.


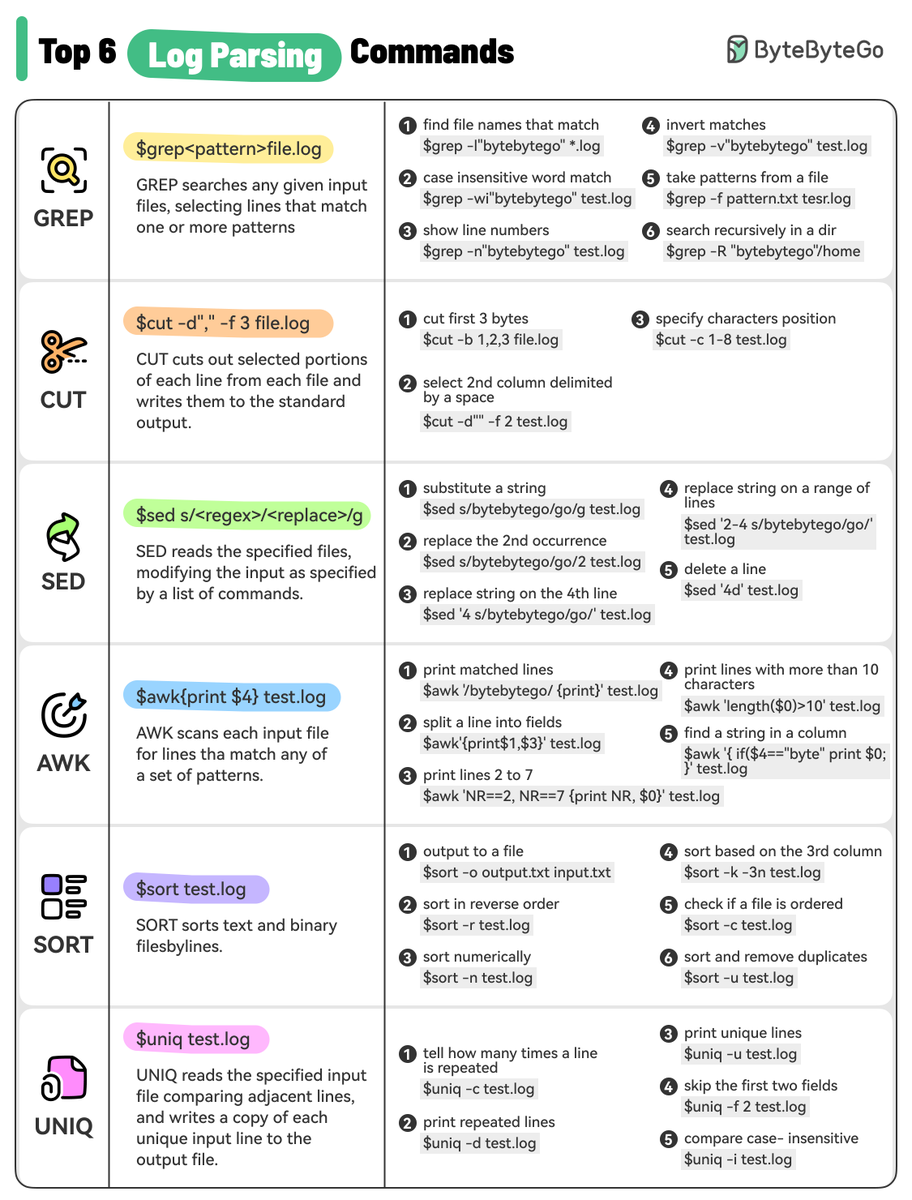
Log Parsing Cheat Sheet. The diagram below lists the top 6 log parsing commands. 1. GREP GREP searches any given input files, selecting lines that match one or more patterns. 2. CUT CUT cuts out selected portions of each line from each file and writes them to the…
Gathered the main Docker concepts into one diagram 👇

United States Trends
- 1. #UFC309 55,2 B posts
- 2. Brian Kelly 9.168 posts
- 3. #MissUniverse 118 B posts
- 4. Jim Miller 5.103 posts
- 5. Beck 14,5 B posts
- 6. Mizzou 6.744 posts
- 7. Feds 37 B posts
- 8. Nebraska 12,2 B posts
- 9. #AEWCollision 10,4 B posts
- 10. Romero 18,1 B posts
- 11. Gators 11,3 B posts
- 12. Onama 2.783 posts
- 13. Louisville 7.180 posts
- 14. Tennessee 40 B posts
- 15. #LAMH 1.275 posts
- 16. #Svengoolie 2.040 posts
- 17. Dylan Sampson 1.496 posts
- 18. Locke 3.907 posts
- 19. Stanford 9.628 posts
- 20. Dinamarca 8.321 posts
Who to follow
Something went wrong.
Something went wrong.






















































































































