S I D D
@siddakmopnamak swaad anusaar akad aukkaat anusaar
Similar User

@MrDuaneJohnson

@newbiepath

@Mar0_0uane

@1m4xx0

@Tiksha_

@deeptimancode

@dastan9408
OMG Cable - The New Batch Now in USB C, the implant is much smaller, but it’s even more powerful than before. Smartphone/tablet attacks, extreme long range triggers, geofencing, etc. o.mg.lol
I didn't know Chrome Devtools had the ability to see unused JS! That's really cool. This article has some things you may know, some you may not, nice resource: blog.asayer.io/15-devtool-sec…

Hunting phishing websites with favicon hashes isc.sans.edu/diary/27326

How will I even manage to see all the talks?!?!? Epicness at play! 🔥🔥
Excited to host a village for my Live Recon show during #NahamCon this Sunday on Discord with awesome demos and talks from @_StaticFlow_, @pry0cc, @rez0__, @d0nutptr, @honoki and @codingo_! Discord.nahamcon.com

Ab bol skta hai omaagoo turu lub 🔥
Congrats Raunak. Finally you did it after immense dedication
1.5 years ago me and my mom saw a dream which finally became true. My mom's 2 years of income has been finally paid off. #OSWE #tryharder Thanks, @offsectraining for wonderful course and certification. Finally I am OSWE. cc. @m0nkeyshell

Happy New Year! The first release #OWASP Amass of 2021 is now available: - Refactor of the #enumeration engine - New #Amass data source scripts - Users no longer need to worry about #DNS resolvers #recon #osint #security #infosec #discovery #bugbounty github.com/OWASP/Amass/re…
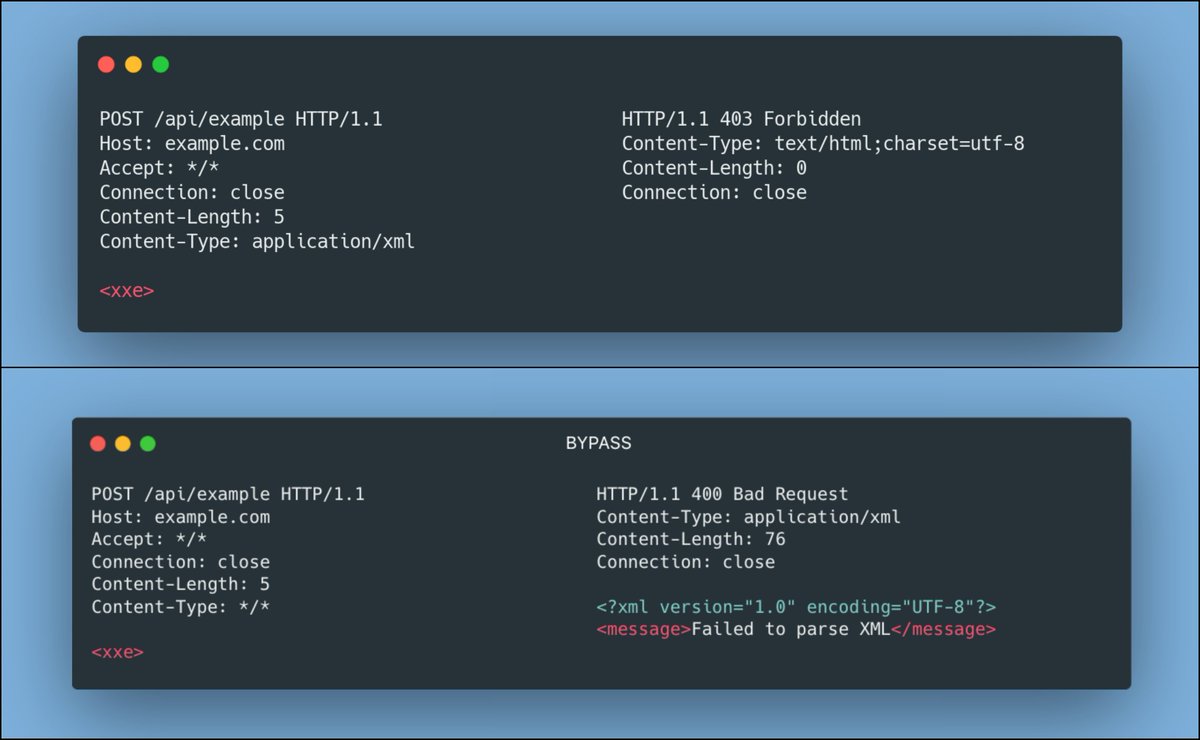
A simple bypass for XXE To avoid XXE Injections, some web applications have custom filters that will block requests which contain "application/xml" Content-Type, to bypass these filters, we can set the Content-Type to wildcard "*/*"
Target-> http://134.122.15.129/ Type-> Real Life based Vulnerability-> Account Takeover | RCE Note-> No brute force needed, Includes real life enumeration Hint: Application writing in python. Lab will be live for max 1 week @abbytheripper @riyazwalikar @security_prince
Cloudflare blocking you? Scan ASN > use get-title to match the the site titles behind cloudflare > add hosts to /etc/hosts > let Burp crawl and scan it for low hanging fruit. Easy win today!
I had so much fun doing this that I needed to share it 😅😆 🤣 Dimitri deserves a P1! #bugbounty #infosec
Haha instead of posting "yay I was awarded any amount of momey", atleast post some tips and writeups so that others can learn as well. Once I asked a top researcher in ATT to share some tweets about his work and tips, his reply was too rude. Only few researchers who share a lot.
~ CTF begins 😋 --> http://134.122.25.252 Here is the lab for our session on Sunday This will be live till the 7th of June Hints: 1. SQL injection(Advance) [Flag: ***] 2. SSRF [Flag: ***] NOTE :👇 Please don't do Bruteforcing or directory search🙏 SQlmap is not needed
[1/2] Hey Guys, I'll go live on youtube 7th June 2020, We will cover 3 really interesting bugs as a black box pentester and really helpful for a bug bounty hunter. 1. Blind Second-order SQL injection 2. Html injection --> PDF --> SSRF 3. XXE via microsoft word
Different ways to represent IPv4 addresses. This can be handy when bypassing SSRF filters. Did you know you can overflow IPs and they will be correctly resolved? I did not till yesterday. #infosec #bugbountytips #IT #Security #programming #networks

RCE through GIF Image with gist.github.com/asdqwe3124/e63… ;). Tip got from here: medium.com/@asdqwedev/rem…
I know it's common sense but remember when parsing JS for endpoints/files: / = Root directory . = This location .. = Up a directory ./ = Current directory ../ = Parent of current directory ../../ = Two directories backwards #bugbountytips ?
The venue is set and so are we! Are you ready too? See all you Women Ninjas on 6th! #3daystoWINJA #countdowntoWINJA #winja2020 #nullcon2020 #winjactf #womenincybersecurity #stem @nullcon @infosecgirls @nullblr @wosectweets



United States Trends
- 1. Dolphins 42,4 B posts
- 2. Datsun 10,3 B posts
- 3. The Party Never Ends 19,9 B posts
- 4. #WinterAhead 212 B posts
- 5. #ena5twt 1.607 posts
- 6. #GoPackGo 10 B posts
- 7. Rental 14,1 B posts
- 8. #TPNE 1.793 posts
- 9. #DonCheadleDay 1.104 posts
- 10. McDaniel 7.625 posts
- 11. Packers 57,9 B posts
- 12. Kindred 5.364 posts
- 13. Bibby 1.535 posts
- 14. Josh Jacobs 8.666 posts
- 15. K Like A Russian N/A
- 16. Party By Myself 1.177 posts
- 17. All Life Long 2.719 posts
- 18. Jordan Love 9.224 posts
- 19. KTM Drip 1.465 posts
- 20. Adore You 6.342 posts
Something went wrong.
Something went wrong.