
Przemek Soszynski
@psoszynskidotnet core, Microsoft Azure, Security, neo4j, quality
Similar User

@emcpadden

@stavrossk

@purekrome

@sintaxasn

@charithwiki

@robrtc

@zell71
Huge congrats to @AIatMeta on the Llama 3.1 release! Few notes: Today, with the 405B model release, is the first time that a frontier-capability LLM is available to everyone to work with and build on. The model appears to be GPT-4 / Claude 3.5 Sonnet grade and the weights are…
How to improve API performance? Here are 5 tips: 1. 𝗣𝗮𝗴𝗶𝗻𝗮𝘁𝗶𝗼𝗻 Pagination is a common optimization technique when result sets are large. By streaming results back to the client in pages, service responsiveness can be improved. 2. 𝗔𝘀𝘆𝗻𝗰𝗵𝗿𝗼𝗻𝗼𝘂𝘀…

Understanding JSON Web Tokens (JWT) JWTs are a compact and self-contained method for securely transmitting information between parties as a JSON object. Let's break this down: 1. 𝗝𝗦𝗢𝗡 stands for JavaScript Object Notation - a lightweight data interchange format that is easy…

Trying to choose the right #Azure compute service for your application? Dive into Azure #AppService, Azure #KubernetesService (AKS), and more to find the perfect fit. See more here: msft.it/6015YArOl

Design Patterns Cheat Sheet

Understanding OAuth 2.0 OAuth is an open standard that allows users to grant limited access to their data on one site to other sites or applications without exposing their passwords. It has become the backbone of secure authorization across the web and mobile apps. 𝗧𝗵𝗲…

Top 8 Cyberattacks

Oauth 2.0 Explained With Simple Terms. OAuth 2.0 is a powerful and secure framework that allows different applications to securely interact with each other on behalf of users without sharing sensitive credentials. The entities involved in OAuth are the User, the Server, and…

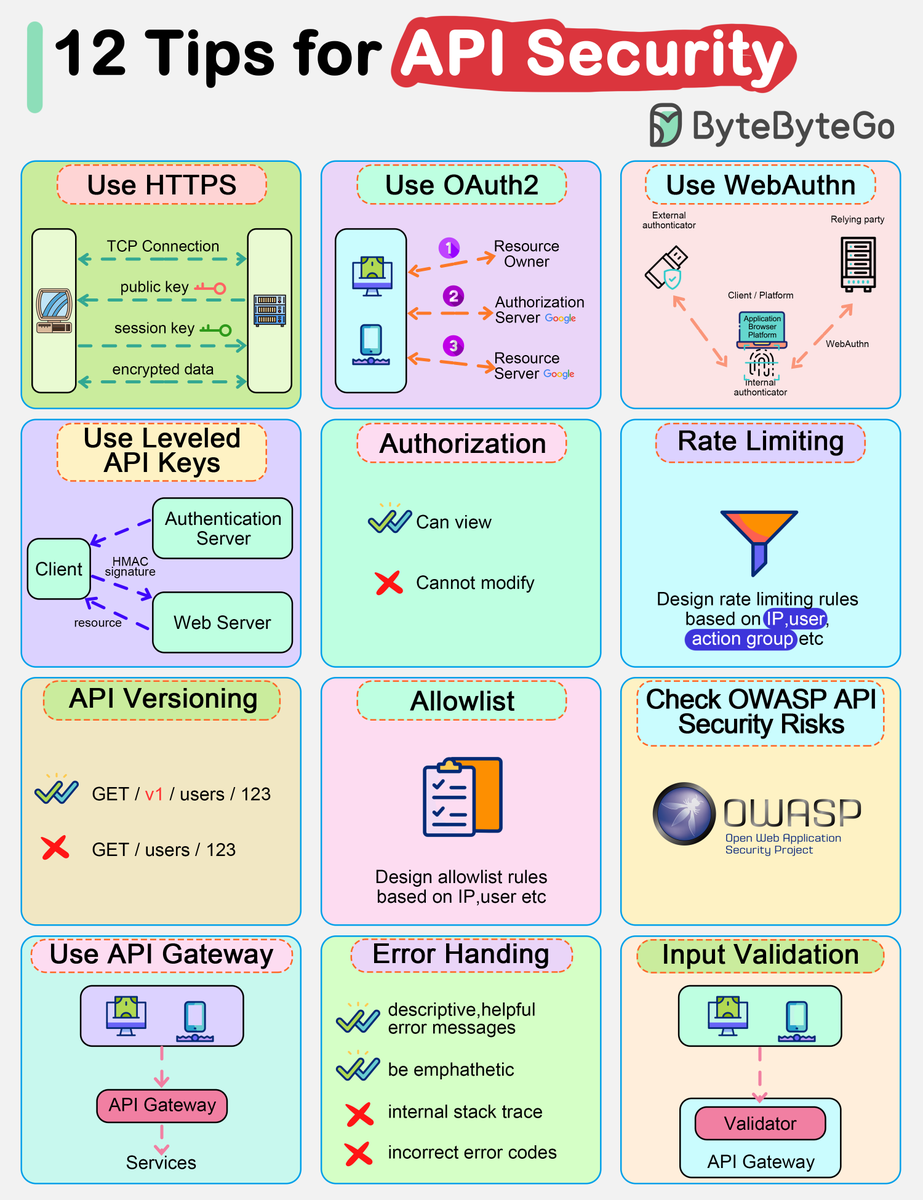
Top 12 Tips for API Security - Use HTTPS - Use OAuth2 - Use WebAuthn - Use Leveled API Keys - Authorization - Rate Limiting - API Versioning - Whitelisting - Check OWASP API Security Risks - Use API Gateway - Error Handling - Input Validation – Subscribe to our weekly…
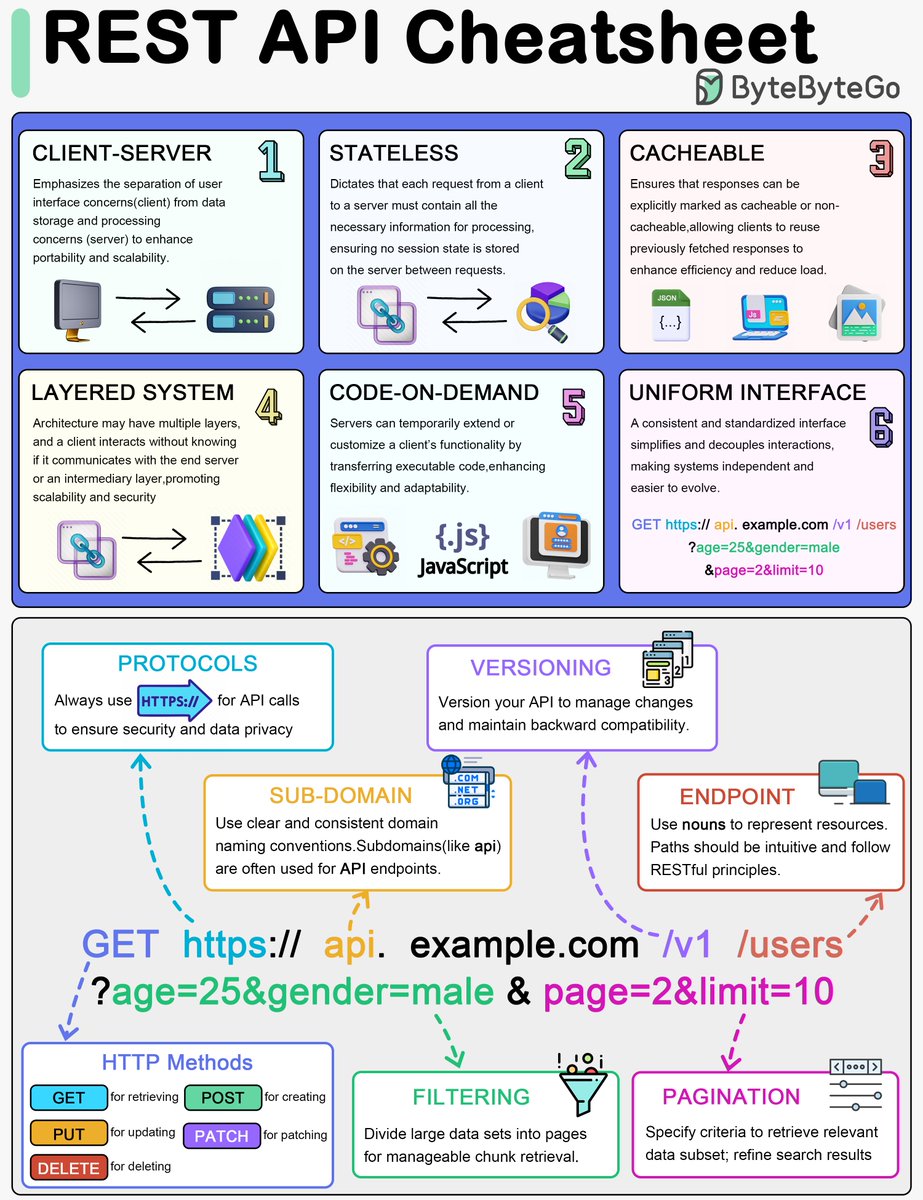
REST API Cheatsheet It covers: ✅ The six fundamental principles of REST API design ✅ Key components like HTTP methods, protocols, and versioning ✅ Practical tips on pagination, filtering, and endpoint design – Subscribe to our weekly newsletter to get a Free System Design…
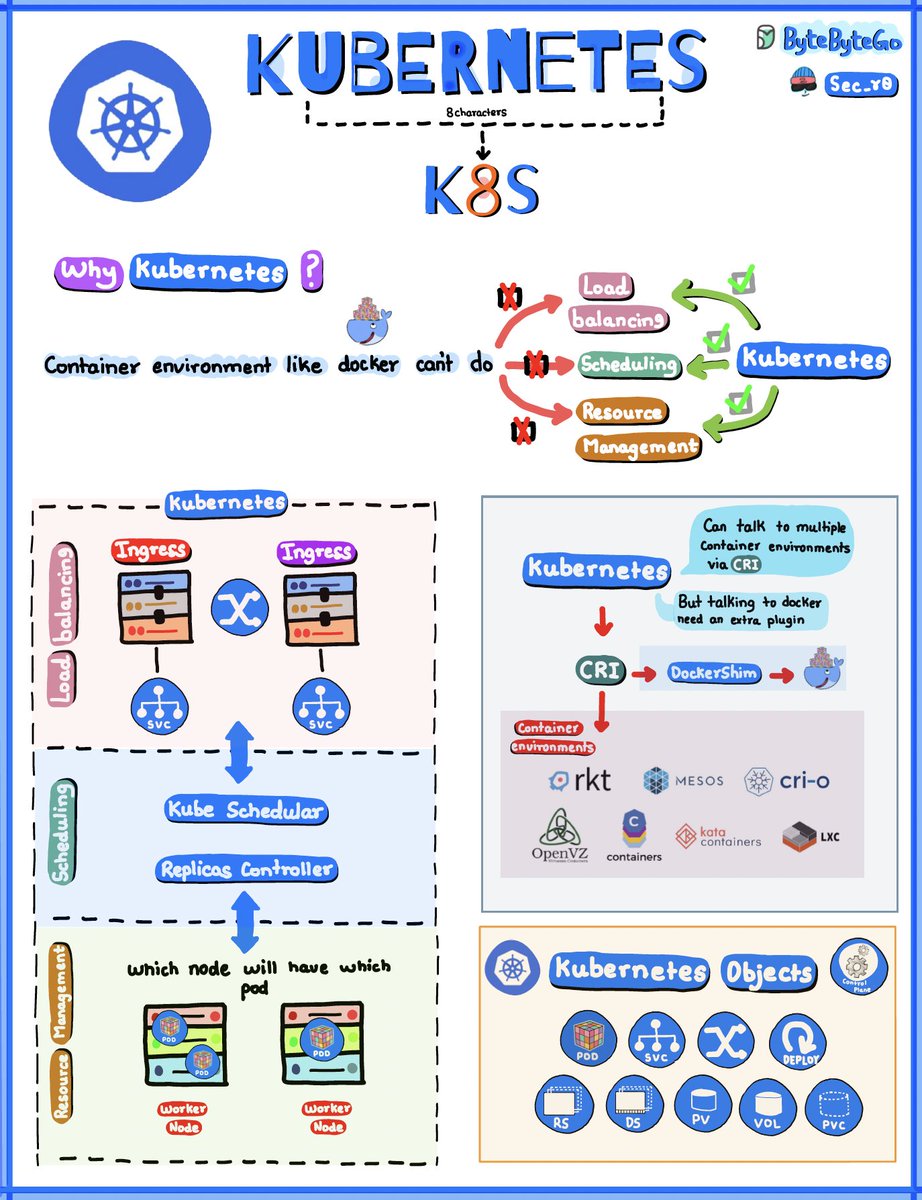
A Visual Overview of Kubernetes Containers revolutionized modern application development and deployment. Unlike bulky virtual machines, containers package up just the application code and dependencies, making them lightweight and portable. However, running containers at scale…
REST API Cheatsheet It covers: ✅ The six fundamental principles of REST API design ✅ Key components like HTTP methods, protocols, and versioning ✅ Practical tips on pagination, filtering, and endpoint design – Subscribe to our weekly newsletter to get a Free System Design…

Three pillars of observability: logging, tracing, and metrics. 🔹 Logging Logging involves recording discrete events within a system, such as incoming requests or database accesses. It typically generates high volumes of data. The ELK stack (Elasticsearch, Logstash, Kibana) is…

Symmetric vs Asymmetric Encryption Symmetric encryption and asymmetric encryption are two types of cryptographic techniques used to secure data and communications, but they differ in their methods of encryption and decryption. 🔹 In symmetric encryption, a single key is used…

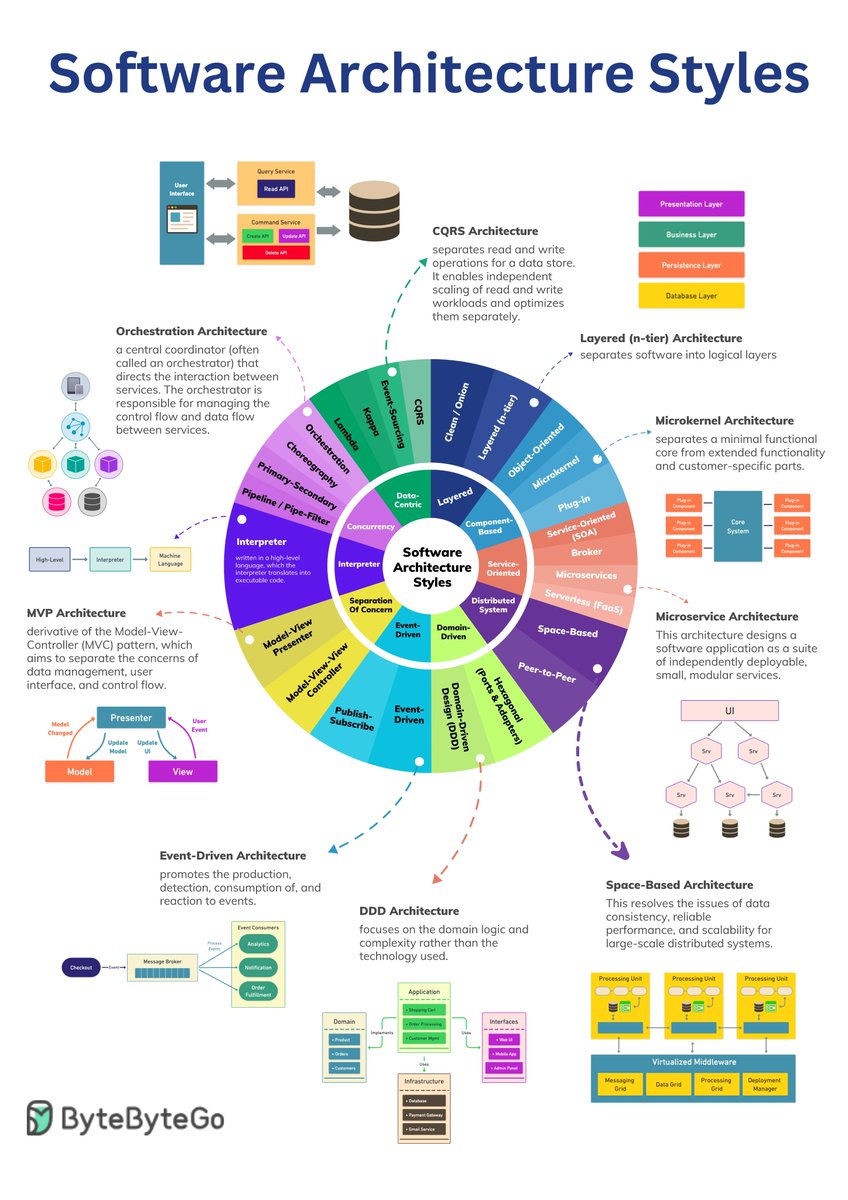
Top Architectural Styles In software development, the architecture you choose plays a key role in shaping a system's structure and behavior. It lays out a blueprint showing how different pieces will fit together to make the software work. Architectural styles offer proven…
What Does ACID Mean? Below is a breakdown of the ACID properties, which are critical to the operations of database transactions. 🔹 Atomicity A transaction is a single unit of operation – either all its data modifications are performed, or none are. If a fault occurs during the…

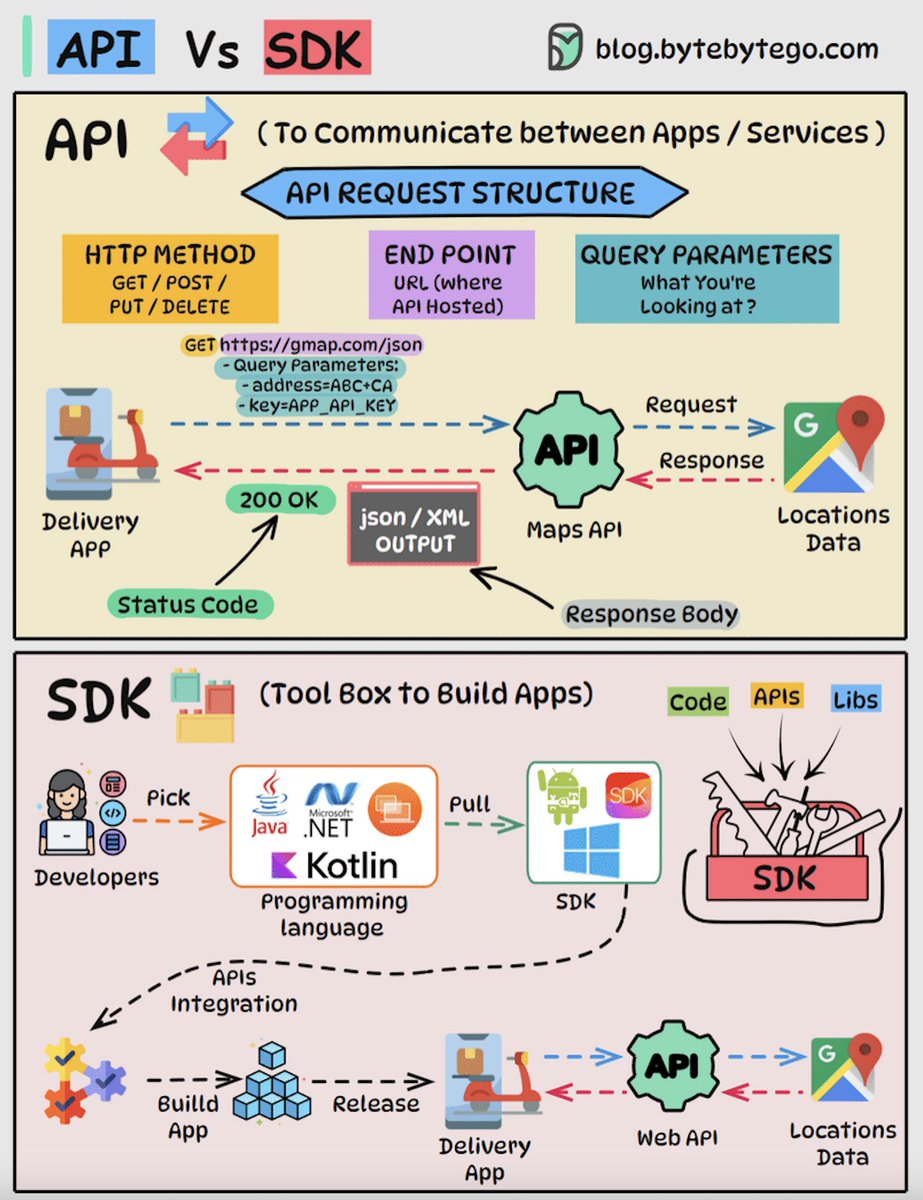
API vs SDK: Key Differences APIs (Application Programming Interfaces) and SDKs (Software Development Kits) are essential tools for software development, but they serve different purposes: 𝗔𝗣𝗜 An API is a set of rules and protocols that allows different software applications…
Top 12 Tips for API Security - Use HTTPS - Use OAuth2 - Use WebAuthn - Use Leveled API Keys - Authorization - Rate Limiting - API Versioning - Whitelisting - Check OWASP API Security Risks - Use API Gateway - Error Handling - Input Validation – Subscribe to our weekly…
Are you considering writing web apps in a different language? Let me suggest C#. I bet #Blazor will make you reconsider. Your mind will be blown.💥💥
How do companies ship code to production? The following describes a typical software delivery workflow. Companies have diverse environments using different tools. This is one representative workflow that demonstrates some common practices. Details will differ across…
United States Trends
- 1. #TheGameAwards 162 B posts
- 2. Clive 19 B posts
- 3. Stafford 8.627 posts
- 4. Elden Ring 89,3 B posts
- 5. Trent Williams 3.122 posts
- 6. Witcher 4 25,4 B posts
- 7. Deebo 9.774 posts
- 8. Tifa 14,5 B posts
- 9. Virtua Fighter 7.479 posts
- 10. Rams 27,2 B posts
- 11. Ciri 25,3 B posts
- 12. Harrison Ford 10,1 B posts
- 13. Kittle 5.140 posts
- 14. 49ers 30,9 B posts
- 15. Hannah Hidalgo 3.997 posts
- 16. Split Fiction 4.858 posts
- 17. Turok 3.918 posts
- 18. Geoff 17,2 B posts
- 19. $LINGO 65,4 B posts
- 20. UConn 7.194 posts
Something went wrong.
Something went wrong.

























































































































