Similar User

@TahmidNil

@0zxyx

@B19R8A14

@Bel_i_e_v_e

@Jayway50063422

@sourabh_tomar_

@i_am_sahinislam

@Hyperio44159824

@sickhuntt

@The_Cyber_Lycan

@Rando2217

@_shday

@Infoneeds1

@HanggoroSeto

@QeradanM
🔥 Filter out noise in Burp Suite 🔥 ➡️ While you are testing with Burp Suite, you may want to add these patterns into the Burp Suite > Proxy > Options > TLS Pass Through settings: .*\.google\.com .*\.gstatic\.com .*\.googleapis\.com .*\.pki\.goog .*\.mozilla\..* 📃 Now all…

Easy Account Take Over 1.Go to web.archive.org 2. Put the domain and search for urls 3. Type in the filter ( %40 ) and search 4. Get a lot of urls that have a parameter leaks the email and password of the users By: @Sayed_v2 credit: @RootMoksha #BugBounty

🔥 Found SQL Injection to Account Takeover Manually :) 1. Enter mobile number to login intercept {"mobile_number":"8888888888"} >> 200 {"mobile_number":"8888888888'"} >> 500 {"mobile_number":"8888888888''"} >> 200 credit: @bbr_bug #bugbountytips

Bypassed SQLi in Philippine Government,Ghauri is Excellient tool for finding timebased blind sqli..

Hacking devices are great. Here are hacker tools you should know. They are awesome.

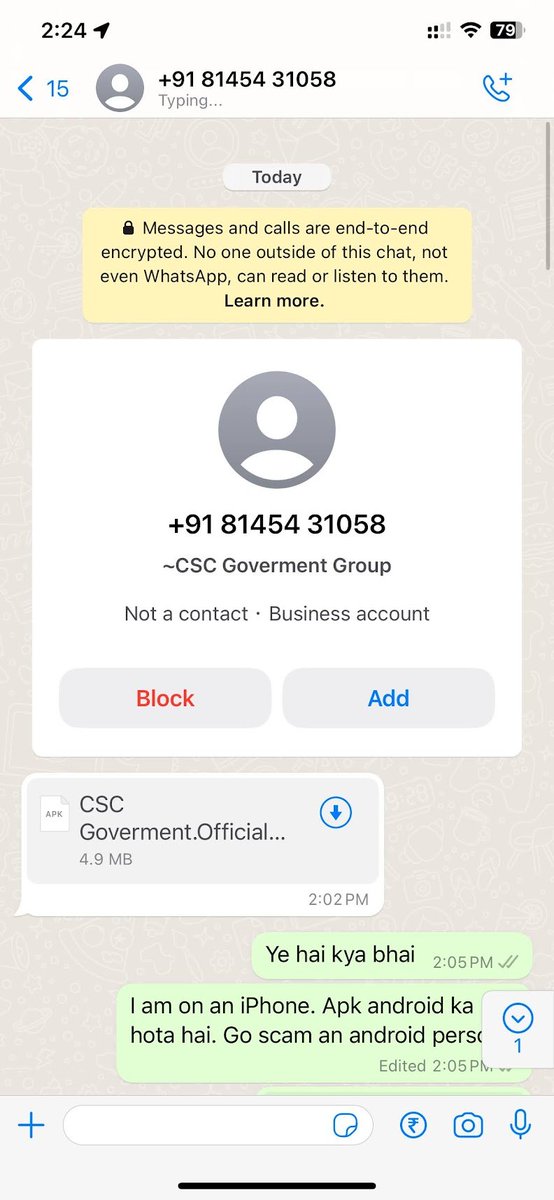
I spoke with yet another scammer today. I don't know why I do this, but here we go. It all started with a few annoying Whatsapp messages trying to scam me. But we ended up wishing each other good luck 😂 1/n
How I Automate Finding Amazon S3 Buckets Using A Simple Python Script From internet 🛜 medium.com/@gradillagusta…
Planning to add a bypassing secuity controls primer and a payload mutation section to TBHMLive.com I dont know if it will fit in 2 days anymore! 😬😅
Rook to XSS: How I hacked chess.com with a rookie exploit skii.dev/rook-to-xss/
Security Code Review: Finding XML vulnerabilities in Code [1/2] muqsitbaig.com/blog/security-…
From P5 to Payday $$$: Escalating Reflected XSS to Account Takeover medium.com/@hasanka-amara…
Do Not Stop at One Attack ! by: Yappare credit: @Pwn4arn #bugbountytips #BugBounty

How DNS works? Credits:@LetsDefendIO #bugbountytips #BugBounty #bugbountytip #bugbounty

My friend just created his new site and said he found a clever way to translate his new blog! 😎 But something looks off... can you tell what it is? 🤔

Here are the top 25 parameters that could be vulnerable to server-side request forgery (SSRF) vulnerability. Credits:@trbughunters #bugbountytips #BugBounty #bugbountytip #bugbounty

🚨Alert🚨CVE-2023-49070:Critical Pre-auth RCE Vulnerability Discovered in Apache OFBiz 🔗 Hunter:hunter.how/list?searchVal… Dorks 👇👇👇 FOFA app="Apache_OFBiz" 📰Refer to securityonline.info/cve-2023-49070… #infosec #infosecurity #Infosys #Vulnerability #cybersecurity

echo "sleep 0.1" >> ~/.bashrc Every time the target opens a terminal, a 100 millisecond delay is added. It becomes annoying when the delay adds up gradually and reaches seconds.
You found an RCE... What's the first command that you're executing? 😎️
JWT Token Bypasses #2 1. Capture the JWT token. 2. If the algorithm is RS256 change to HS256 and sign the token with the public key (which you can get by visiting jwks Uri / mostly it will be the public key from the site's https certificate) (1/2) Credits:@HackerHumble #BugBounty
If you get a reverse shell on Ubuntu 18.04.x or can run remote code execution, you should definitely try this exploit on that server or workspace ; raw.githubusercontent.com/ThrynSec/CVE-2… #RCE #privilegeescalation #BugBounty #bugbountytip


United States Trends
- 1. McDonald 53,8 B posts
- 2. #AskFFT 1.024 posts
- 3. Mike Johnson 57 B posts
- 4. #RollWithUs N/A
- 5. Go Bills 5.407 posts
- 6. Good Sunday 74,1 B posts
- 7. #sundayvibes 8.985 posts
- 8. Tillman 2.180 posts
- 9. Big Mac 5.867 posts
- 10. Coke 33,8 B posts
- 11. #GoPackGo N/A
- 12. #AskZB N/A
- 13. Full PPR N/A
- 14. Kittle 1.588 posts
- 15. Happy Founders 1.044 posts
- 16. Chubb N/A
- 17. Shakir 2.063 posts
- 18. NFL Sunday 6.076 posts
- 19. Founders Day 1.336 posts
- 20. Higgins 9.249 posts
Who to follow
-
 Tahmid Niloy
Tahmid Niloy
@TahmidNil -
 0zxyx
0zxyx
@0zxyx -
 B19R8A14
B19R8A14
@B19R8A14 -
 Believe😊
Believe😊
@Bel_i_e_v_e -
 Cristing
Cristing
@Jayway50063422 -
 Sourabh_tomar_official
Sourabh_tomar_official
@sourabh_tomar_ -
 Sahin islam
Sahin islam
@i_am_sahinislam -
 Iftekhar_ul Haque
Iftekhar_ul Haque
@Hyperio44159824 -
 Tushar
Tushar
@sickhuntt -
 Shubham
Shubham
@The_Cyber_Lycan -
 jake green
jake green
@Rando2217 -
 shady
shady
@_shday -
 Infoneeds
Infoneeds
@Infoneeds1 -
 Rezn
Rezn
@HanggoroSeto -
 M Qeradan
M Qeradan
@QeradanM
Something went wrong.
Something went wrong.