MUHAMMAD
@muhammadhacker_Interested in all things #AI,#RedTeam,#quantum
Similar User

@jeffmcjunkin

@0sm0s1z

@aglerj

@80sDweeb

@sysjohns

@illustrioushefe

@sociosploit

@LElliottInfoSec

@MoarGood

@WH_Y

@0xsparwol

@petal_tech

@DoddsyLTD

@njtreker

@undercl0ck
🎉GIVEAWAY⭐️ I am giving away 1 print copy and 5 e-book copies of Mastering AWS Security! 🛡️☁️ 📚Book: packtpub.com/en-ca/product/… Enter before Tuesday, September 03, 2024 at 6PM EST by following, commenting, and RT! @PacktPublishing Author: linkedin.com/in/laurentm

🚩Palo Alto Networks has released workaround guidance for a command injection vulnerability (CVE-2024-3400) affecting PAN-OS versions 10.2, 11.0 & 11.1. Apply workarounds asap 👉 cisa.gov/news-events/al…
Regarding the xz backdoored binary, see the one-liner below to check the version you have installed. **I wouldn’t suggest folks running the malicious binary with -v option🫠🫣 for xz_p in $(type -a xz | awk '{print $NF}' | uniq); do strings "$xz_p" | grep "xz (XZ Utils)" ||…
A quick note about xz-utils backdoor: 1 - luckily, this was caught early. 2 - most run xz-utils 5.2/5.4. 5.6 is bad. 3 - quick check: `xz -V` 4 - Thanks to people who paid attention openwall.com/lists/oss-secu… cisa.gov/news-events/al…
Security researchers found flaws in Saflok hotel keycard locks, used on 3 million doors in 13,000 properties worldwide, that can be used to open them in seconds. The lockmaker Dormakaba has been working on a fix but told them only 36% of locks are updated. wired.com/story/saflok-h…
Earlier someone asked if @HuntressLabs hires associate/junior levels: We love to hire folks who climb the leaderboards of hack the box and blue team labs online. A lot of our interview focuses on basic DFIR so I recommend consuming @13CubedDFIR content fanatically. Read and…
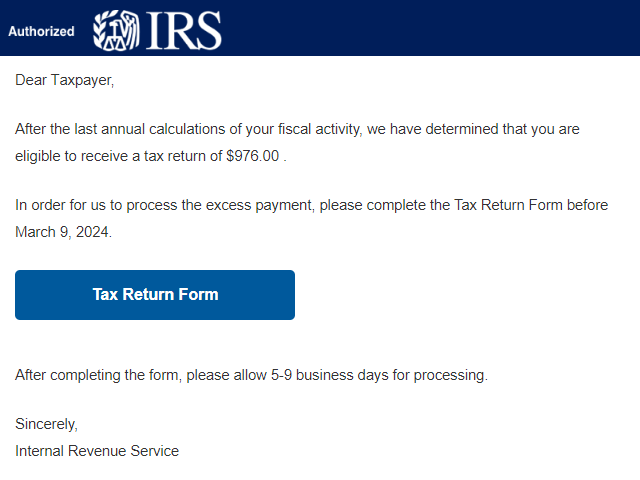
Phishing campaigns, including ones related to known phishing-as-a-service (PhaaS) platforms such as Tycoon and NakedPages, are taking advantage of the tax season in the US for social engineering.
Eight years ago, #AlphaGo made history by becoming the first AI to defeat world champion Lee Sae Dol in the game of Go. ⚫⚪ He spoke to @GoogleKorea to share his reflections on this milestone match and how it showed the potential of AI to the world. ↓ dpmd.ai/3Pplkyk
Intern, Junior, Senior, Principal, Sr Principal, Staff, Master, Artisan. These are the levels I believe best suites most of the fields of study in Cyber Security. I worked with @carnal0wnage to put some of this together one day and wanted to share my thoughts on it:
Over the past year, we have been prototyping and building a new machine-learning approach to detection, and today are open-sourcing a new detection engine for Snort called "SnortML." This is included in the latest Snort 3 release (version 3.1.82.0) cs.co/6019kkLdB

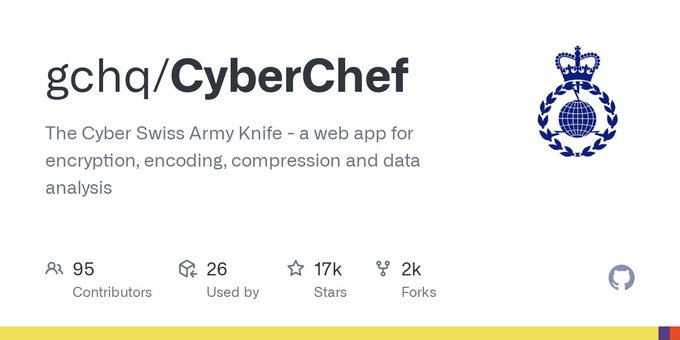
Version 10 of CyberChef is ready for exploring. Developed by GCHQ's very own software engineers, explore the latest features of the cyber Swiss Army knife ⬇️ github.com/gchq
Want to help aspiring security professionals from areas where the cost of living is extremely high, or those from marginalized communities? Consider a membership with the Off By One Security channel, and take a look at our goals and the benefits! youtube.com/@OffByOneSecur…
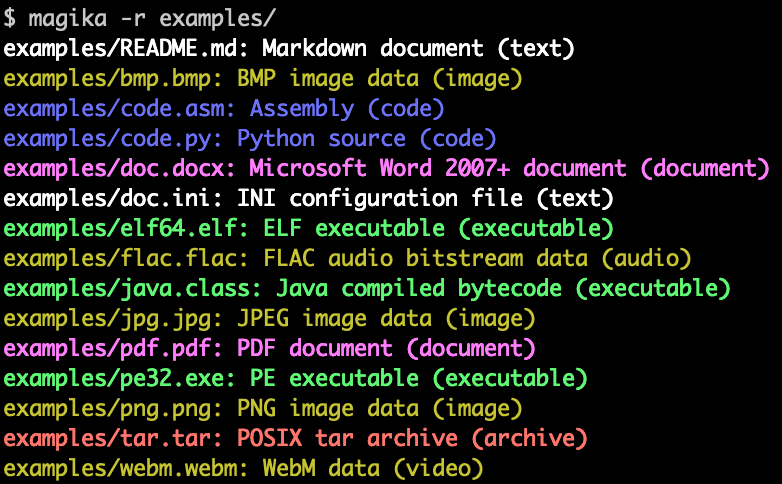
🔥 icymi - @Google has released #magika, an "AI powered file type detection tool that relies on .. deep learning" github.com/google/magika Curious what everyone's results have been if you're using it. I've done limited testing and so far looks promising :)
🚨 On February 26th and 27th Telekom Security and Bayern-CERT observed threat actor #TA577 phishing campaigns. This time the actor is not spreading malware, but apparently uses NTLMv2 handshakes to steal user credentials/hashes. 🧵1/7
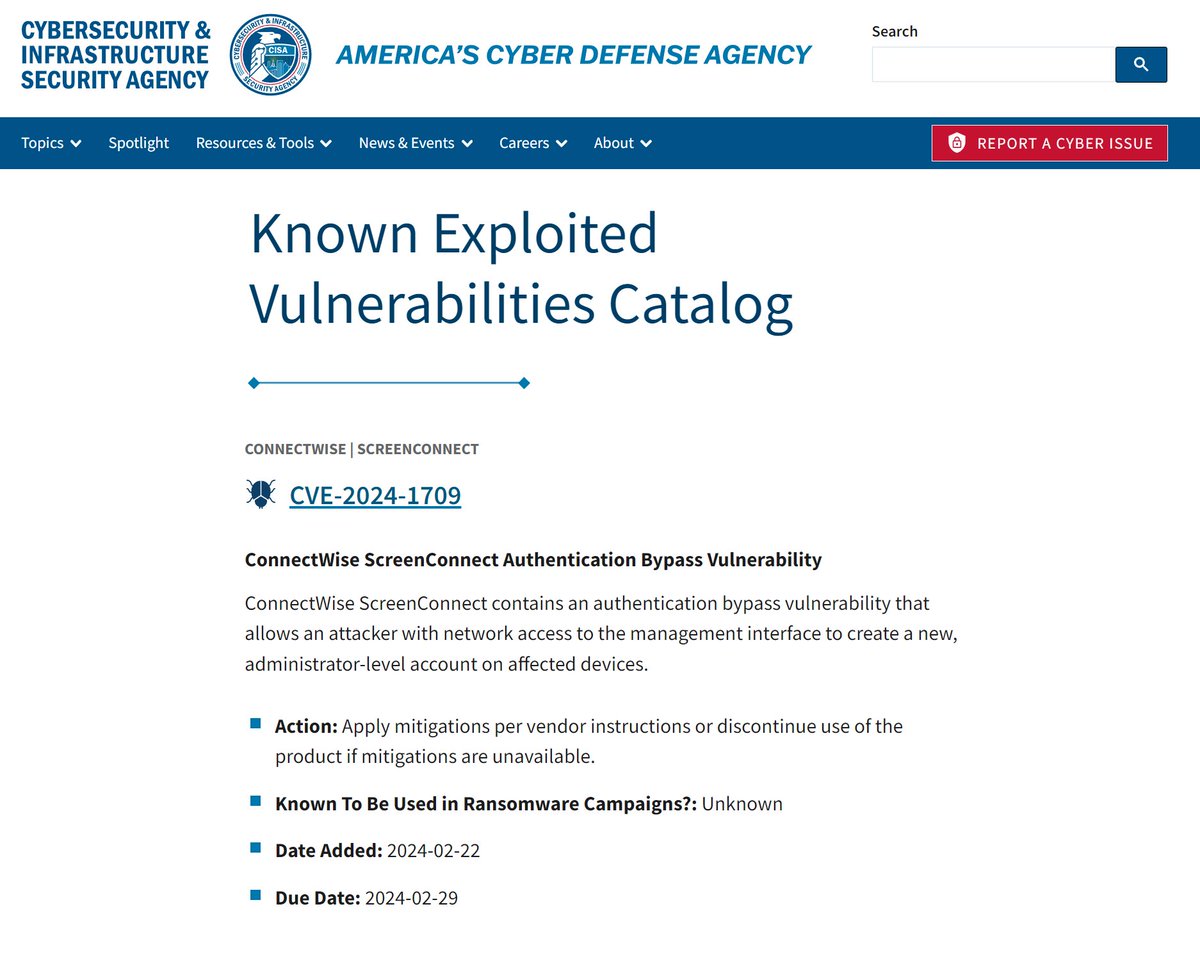
CISA adds #ScreenConnect CVE-2024-1709 authentication bypass to the KEV, deadline Feb 29th.
Tool to remotely dump secrets from the Windows registry github.com/jfjallid/go-se…
CSP causes app pentesters to curse heavily, which is a good thing. You should be using these.
Harden your web application by controlling the rules of the game! In our new #blog, @hoodoer guides us through implementing a Content Security Policy (CSP), making exploiting XSS vulnerabilities significantly more difficult for attackers. Read it now! hubs.la/Q02kmb1v0
It's time!
New ep! 142: Axact Axact sells fake diplomas and degrees. What could go wrong with this business plan? darknetdiaries.com/episode/142

After a few weeks of teasing, I'm happy to officially announce the launch of Fabric. Fabric is an open-source framework for augmenting humans using AI. 📄Tons of prompts for real-world use cases 🧱A free AI server for hosting your own APIs …much more! github.com/danielmiessler…
You should take some time today and read all of @assume_breach 's post -> assume-breach.medium.com/im-not-a-pente… I could probably pick a few parts that I could counter on semantics but it's a fantastic post of the reality of pentesting. Forward this to your friends and students.
I cant remember where i saw it but someone posted a awesome browser extention for scraping data a while back... anyone remember?
United States Trends
- 1. #AcousticPianoCollection 2.687 posts
- 2. $CUTO 7.478 posts
- 3. Jaguar 193 B posts
- 4. #TSTheErasTour 1.801 posts
- 5. #ASKJAGE N/A
- 6. Hobi 67,4 B posts
- 7. #wednesdayfeelings 3.048 posts
- 8. $TGT 3.767 posts
- 9. Hampton Inn 3.655 posts
- 10. Ray Lewis 1.552 posts
- 11. Vinatieri N/A
- 12. DeFi 111 B posts
- 13. Hump Day 18,5 B posts
- 14. Vatican City N/A
- 15. Jay Leno 6.848 posts
- 16. Good Wednesday N/A
- 17. Antonio Gates N/A
- 18. #WorldChildrensDay 21,1 B posts
- 19. Linda McMahon 1.889 posts
- 20. Liam Payne 88 B posts
Who to follow
-
 Jeff McJunkin
Jeff McJunkin
@jeffmcjunkin -
 Matthew Toussain
Matthew Toussain
@0sm0s1z -
 Joe Agler
Joe Agler
@aglerj -
 Scott Williams, the CyberDweeb
Scott Williams, the CyberDweeb
@80sDweeb -
 Aaron Johns
Aaron Johns
@sysjohns -
 Biteater
Biteater
@illustrioushefe -
 Hutch (Sociosploit)
Hutch (Sociosploit)
@sociosploit -
 Logan Elliott
Logan Elliott
@LElliottInfoSec -
 kyle hendrickson
kyle hendrickson
@MoarGood -
 Andy H
Andy H
@WH_Y -
 sparwol
sparwol
@0xsparwol -
 Petagaye AC
Petagaye AC
@petal_tech -
 Doddsy - im still alive somehow..
Doddsy - im still alive somehow..
@DoddsyLTD -
 Charlie Fraser - @[email protected]
Charlie Fraser - @[email protected]
@njtreker -
 𝚛𝚢ム𝚗 🕊
𝚛𝚢ム𝚗 🕊
@undercl0ck
Something went wrong.
Something went wrong.