Similar User

@OldWonk

@LirooPierre

@akavish33

@RIKILIFT

@Trikiwinky

@meyroux1
We've had our first collision of #Pwn2Own Ireland. The @Synacktiv team exploited the #Lorex camera with two bugs, but one had previously been used in the contest. They still earn $11,250 and 2.25 Master of Pwn points. #P2OIreland

New breach: Internet Archive had 31M records breached last month including email address, screen name and bcrypt password hash. 54% were already in @haveibeenpwned Read more: bleepingcomputer.com/news/security/…
Our very own @_p0ly_ and @masthoon are now presenting: 0-click RCE on Tesla Model 3 through TPMS Sensors #HEXACON2024

There’s a reason they call it ethical hacking. Good pentesters will document their activity via commands they ran and screenshots, but we don’t track every little thing, that would be impossible given the timeframe we test in. Pentesters are entrusted with organizations deep…
here me out, this dude is not getting replaced by AI

> 37,000 commits per year > deploys straight to production > how to not break prod? “just code more carefully” Absolute Chad
Quelqu'un lui a juste dit que les études d'informatique commençait par une semaine de piscine ?
Est-ce que vous vous rendez bien compte que de toutes les études possibles en parallèle de sa carrière sportive ce crack de Léon Marchand a choisi L'INFORMATIQUE ?!!

We found a CPU bug that allows an arbitrary physical memory write, thus allow to *read* and *write* the memory for every process! Check out the website for more details: ghostwriteattack.com
With the #GhostWrite CPU vulnerability, all isolation boundaries are broken - sandbox/container/VM can't prevent GhostWrite from writing and reading arbitrary physical memory on affected RISC-V CPUs. Deterministic, fast, and reliable - no side channels. ghostwriteattack.com

This is what I mean when I say working with MSRC is degrading. They want everything: write up, stack traces, PoC, exploit source, analysis, life advice, approval on anything you will ever publish. In return they will patch your bug whenever they feel like it and not tell you
Uncoordinated Vulnerability Disclosure: After more than a decade of CVD, has it benefited vendors or researchers more? Have the number of bugs increased to where vendors simply cannot cope with CVD? @dustin_childs has some thoughts - & lots of questions. zerodayinitiative.com/blog/2024/7/15…
I'm on a 6-hour flight with Starlink, and I am using my GPD Pocket tiny laptop, to Parsec home to my desktop and access all my virtual machines and home lab server. Honestly I just think it is funny. 😂

Black hats hate this: hacker-proof your Windows PC

The final boss of tipping: this landlord sent a rent payment request ($1,549) and the tenant web portal has a tipping option (15%, 20%, 25% or custom).

CVE-2024-20391 - Our ninjas @l4x4 and @k3vinTell discovered that a mouse and a vulnerable Cisco NAM Client is all you need to get SYSTEM privileges from unauthenticated physical access. synacktiv.com/advisories/cod…
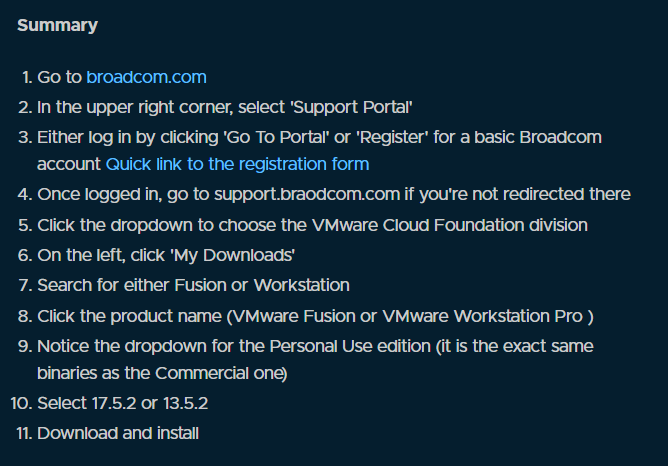
Broadcom managed to turn VMware software download into an escape room 😂 mikeroysoft.com/post/download-…

Memo to myself: Take a high quality photoshoot before getting arrested
Update: Someone asked for a comment from Synology. Synology confirmed they were targeted by (what they believe to be) a spear-phishing campaign in April, 2023. tl;dr the data is old. No ransomware was deployed. The company is not impacted.

United States Trends
- 1. Celtics 3.561 posts
- 2. Cavs 25,1 B posts
- 3. #DWTS 3.253 posts
- 4. #RHOBH 2.242 posts
- 5. Joey Galloway N/A
- 6. #OnlyKash 77,4 B posts
- 7. $MADGUY N/A
- 8. Darius Garland 1.423 posts
- 9. Mobley 2.589 posts
- 10. Nancy Mace 100 B posts
- 11. Jaguar 72 B posts
- 12. #MCADE N/A
- 13. Pat Murphy 2.777 posts
- 14. Linda McMahon 8.593 posts
- 15. Queta N/A
- 16. Cenk 19,9 B posts
- 17. Lichtman 4.418 posts
- 18. Chile 171 B posts
- 19. Indiana 30,8 B posts
- 20. #spitemoney N/A
Something went wrong.
Something went wrong.




























































































































