
Lewis
@lewsecurityIR, malware, threats and intelligence research. Doing security @Microsoft. Based in the UK. (Opinions my own).
Similar User

@paramdhagia

@hikari_lmc

@jayaharsha

@JDSaladfinger

@D8c_au
Virus.xcheck is a Python tool that bulk verifies the existence of file hashes in the Virus Exchange database. Note this is alpha. #Vx #Malware #Python @vxunderground github.com/lewiswigmore/V…
Between July 2023 and June 2024, Microsoft observed nation-state threat actors conduct operations for financial gain, enlist cybercriminals to collect intelligence, and make use of the same tools and frameworks favored by cybercriminals: msft.it/6018mf9Sm
Playing charades with the Tesla Optimus robot last night. This is either the single greatest robotics and LLM demo the world has ever seen, or it's MOSTLY remote operated by a human. No in between.
New breach: Internet Archive had 31M records breached last month including email address, screen name and bcrypt password hash. 54% were already in @haveibeenpwned Read more: bleepingcomputer.com/news/security/…
Updates to vx-underground Samples: - AcidRain - AgentTesla - Android.SoumniBot - AveMaria - GuLoader - LummaStealer - NjRat - PikaBot - QakBot - Rawdoor - Remcos - SystemBC - Upstyle - Vultur - zLoader Papers: - 2024-06-06 - Remcos RAT Analysis - 2024-06-06 - Agent Tesla…

Read this FAQ on the XZ Utils vulnerability CVE-2024-3094 and get guidance on assessing exposure and discovering affected devices using Microsoft Defender Vulnerability Management, Microsoft Defender for Cloud, and Microsoft Security Exposure Management: msft.it/6015cLJVB
The xz package, starting from version 5.6.0 to 5.6.1, was found to contain a backdoor. The impact of this vulnerability affected Kali between March 26th to March 29th. If you updated your Kali installation on or after March 26th, it is crucial to apply the latest updates today.
Over the past couple of days we have become aware of malware targeting gamers! More specifically, a currently unidentified Threat Actor is utilizing an infostealer to target individuals who cheat (Pay-to-Cheat) in video games. A Call of Duty cheat provider (PhantomOverlay) was…
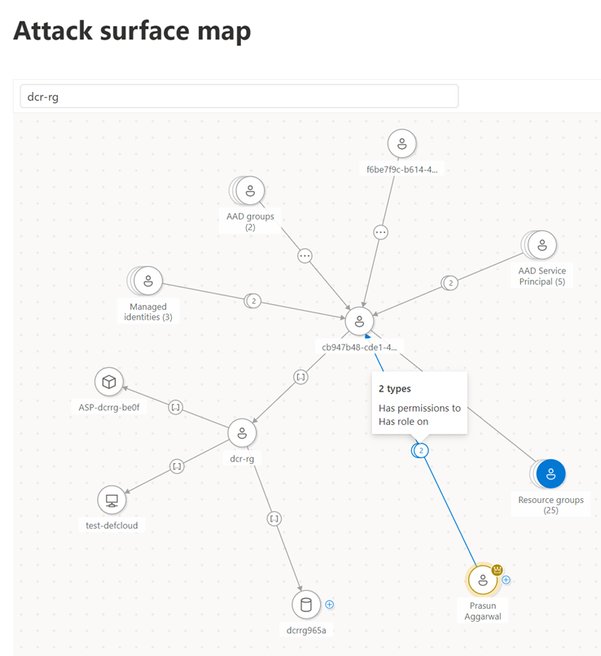
The new Microsoft Security Exposure Management is a huge win for all #MXDR customers and I especially love the overhauled Attack Path Analysis feature. 🛡️ If you are a customer go check it out today in the security portal. techcommunity.microsoft.com/t5/security-co…
Credit to @britishlibrary for sharing lessons learned from the cyber attack it experienced last year – a great example of taking a transparent approach for the benefit of others.
Today we’ve published a paper about the cyber-attack that took place last October. Its goal is to share our understanding of what happened and to help others learn from our experience. You can read the paper on our website, and hear from our CEO, Sir Roly Keating, in this…

Google Open Sources Magika: AI-Powered File Identification Tool 🔧 thehackernews.com/2024/02/google… #Google #RCE
Ivanti Pulse Secure Found Using 11-Year-Old Linux Version and Outdated Libraries 🤖 thehackernews.com/2024/02/ivanti… #Linux
U.S. Internet Leaked Years of Internal, Customer Emails 🔧 krebsonsecurity.com/2024/02/u-s-in… #Dataleak
Vulnerability Summary for the Week of February 5, 2024 | CISA 🛠️ cisa.gov/news-events/bu… #Vulnerability
Bank of America warns customers of data breach after vendor hack 🛠️ bleepingcomputer.com/news/security/… #Databreach
Vulnerability Summary for the Week of February 5, 2024 | CISA ⚙️ cisa.gov/news-events/bu… #Vulnerability
⚙️ Google: Half of all zero-days used against our products are developed by spyware vendors therecord.media/google-spyware… #Google #ZeroDay #Spyware
🤖 MIT PhD Student Hacks Apple Vision Pro Days After Release, Reveals Potential Jailbreaks And Malware Threats in.mashable.com/tech/68954/mit… #Apple #Malware #AR
United States Trends
- 1. Kash 689 B posts
- 2. #FayeYokoYentertainAwards 189 B posts
- 3. SPOTLIGHT COUPLE FAYEYOKO 191 B posts
- 4. Happy New Month 119 B posts
- 5. Houston 32,8 B posts
- 6. Wray 56,4 B posts
- 7. Fauna 91,8 B posts
- 8. #sundayvibes 3.661 posts
- 9. Iowa State 10,4 B posts
- 10. jeno 336 B posts
- 11. #HookEm 15,7 B posts
- 12. #FortniteChapter6 9.059 posts
- 13. #LAGalaxy 2.143 posts
- 14. Texas 183 B posts
- 15. McCabe 42,2 B posts
- 16. Oregon 36,9 B posts
- 17. Elko 3.437 posts
- 18. Hololive 43,2 B posts
- 19. Bill Barr 9.865 posts
- 20. Aggies 12,8 B posts
Something went wrong.
Something went wrong.





















































































