Kabeer 🇮🇳
@kab33rrrEnterprise Security @zoom 💼 // Bug Bounty Hunter 🪲 // CoD & CSGO 🎮 // Anime🎥
Similar User

@basu_banakar

@0xNaeem

@zapstiko

@nihad_rekany

@GhimireVeshraj

@HolyBugx

@0x_Akoko

@0xJin

@3ncryptSaan

@mamunwhh

@Virdoex_hunter

@leo__rac

@AnubhavSingh_

@imranHudaA

@re_and_more
People who weren't smarter than you in college but are now doing well in life, not due to luck, but because they have mastered the art of solving difficult problems.
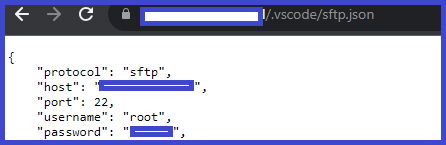
Files Containing Juicy Info inurl:"/.vscode/sftp.json" #bugbounty #bugbountytips #bugbountytip #cybersecurity #ethicalhacking
Thankful for the opportunity ! Excited to attend #bluehatindia May 2024 @MSFTBlueHat #bluehat #microsoft

Successfully bypassed a SSRF WAF by using a combination of IPV6 + Unicode. Payload for Metadata instances: http://[::ⓕⓕⓕⓕ:①⑥⑨。②⑤④。⑯⑨。②⑤④]:80 Check images for response difference between 169.254.169.254 and the above payload I shared 🔥 #bugbounty #infosec #waf


Bug bounty programs are one of the best ways to reward responsible security researchers for helping us better secure our customers. - Stephen Schmidt, Chief Security Officer, Amazon
500$ bounty When you invite users to your product, sometime it can carry hidden fields with the invite request it'll be a good opportunity to check for blind & stored XSS. #bugbountytips #bugbounty

OWASP LLM Top Ten v.1: 🚀 Prompt Injections 💧 Data Leakage 🏖️ Inadequate Sandboxing 📜 Unauthorized Code Execution 🌐 SSRF Vulnerabilities ⚖️ Overreliance on LLM-generated Content 🧭 Inadequate AI Alignment 🚫 Insufficient Access Controls ⚠️ Improper Error Handling 💀 Training…
सदा शिव सर्वदा शिव हर हर महादेव || Proud Indian🇮🇳 Proud Sanatani 🕉️

When you are hunting for blind XSS. Go to forget password and add admin@company .com and add your blind XSS payload on the header. Easy way and it will logged on admin log, if he checked his account you will exploit his account. #bugbountytips

Identified a XSS bug in your target? Don’t be too quick to report it for a Medium bounty. Read this post completely to learn how XSS is escalated to an ATO for much higher bounties 💸 1️⃣ Exploiting Session ID Leakage: XSS can be escalated to Account Takeover by exploiting…
curation of all(most) immunefi bug bounty writeups I could find(till now) github.com/sayan011/Immun…
#bugbountytips #bugbounty #cybersecurity #Pentesting #Hacking #bugcrowd #Hackerone #IDOR #XSS #SQLI Craft CMS Remote Code Execution Craft CMS is a flexible and user-friendly content management Affected Versions CMS version 4.0.0-RC1 through 4.4.14 EXPLOIT in Requset…

United States Trends
- 1. Max Fried 15,1 B posts
- 2. $DCARS 6.687 posts
- 3. #twitchrecap 22,7 B posts
- 4. Loan 48,8 B posts
- 5. Burnes 5.091 posts
- 6. WNBA 19,6 B posts
- 7. Lookman 36,6 B posts
- 8. Rodon 1.280 posts
- 9. Red Sox 6.601 posts
- 10. 2025 MLB Draft 1.585 posts
- 11. Vini 53 B posts
- 12. Ethan Holliday N/A
- 13. #Dreamcars 2.348 posts
- 14. Braves 4.231 posts
- 15. Breslow 1.001 posts
- 16. Strahan 2.693 posts
- 17. Favre 4.330 posts
- 18. Jamaal 5.651 posts
- 19. Atalanta 98 B posts
- 20. Stroman N/A
Who to follow
-
 Basavaraj Banakar🇮🇳
Basavaraj Banakar🇮🇳
@basu_banakar -
 Naeem Ahmed Sayed 🇧🇩
Naeem Ahmed Sayed 🇧🇩
@0xNaeem -
 𝐑𝐀𝐢𝐡𝐚𝐧 ✪
𝐑𝐀𝐢𝐡𝐚𝐧 ✪
@zapstiko -
 Nihad
Nihad
@nihad_rekany -
 Veshraj Ghimire🇳🇵
Veshraj Ghimire🇳🇵
@GhimireVeshraj -
 HolyBugx
HolyBugx
@HolyBugx -
 Roberto Nunes
Roberto Nunes
@0x_Akoko -
 0xJin
0xJin
@0xJin -
 Shakti Ranjan Mohanty || 🇮🇳 ||
Shakti Ranjan Mohanty || 🇮🇳 ||
@3ncryptSaan -
 khan mamun
khan mamun
@mamunwhh -
 Deepak Dhiman🇮🇳
Deepak Dhiman🇮🇳
@Virdoex_hunter -
 Leo Rac
Leo Rac
@leo__rac -
 Anubhav Singh🇮🇳
Anubhav Singh🇮🇳
@AnubhavSingh_ -
 Imran Huda(Ahhad)
Imran Huda(Ahhad)
@imranHudaA -
 Reverse Engineering and More
Reverse Engineering and More
@re_and_more
Something went wrong.
Something went wrong.



















































































![[Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)