harminator
@harminatorA tech guy, cybersecurity & helping people understand tech.
Similar User

@x86_n64

@LongGameFit

@GkglassGreg

@oliviafalcon_

@gloomybb

@BrilAmsterdam

@janded_home_boi

@glavasidis

@anghnd
Thousands of Devices Wiped Remotely Following Mobile Guardian Hack securityweek.com/thousands-of-d…
What does this mean…. Word for word? I hardly post about politics, but this needs to be understood..
I was looking at UNODA - Cyber Diplomacy 1. Cooperation for Stability 2. Duty of Care 3. No nation user of territory for malicious cyberactivities and 8 more. I doubt any nation state complies with one! #CyberSecurity #UNODA #Compliance
It’s quite true! Nothing Smart in this house! If I leave the house and I don’t know what’s in the fridge, too effing bad.

Widom quote: Put your brain in motion before you put your mouth in gear! #Wisdom #senselife #Management
Been using some IT compliance tools. @RapidFireTools Its pretty amazing how much compliance has evolved over the last 15 years. #Compliance #CIS #CISO #NISTCSF
Bad debate nights happen. Trust me, I know. But this election is still a choice between someone who has fought for ordinary folks his entire life and someone who only cares about himself. Between someone who tells the truth; who knows right from wrong and will give it to the…
So I have been working closely with CyberSec stuff. The amount of misinformation boggles my mind! top of that the certification authorities are making it more and more complex for the average business person to understand why the safeguards & controls are being put in place!
12 clear signs of a high-performing employee: And how to implement them. (Learnt from recruiting 500+ people across 15 years)

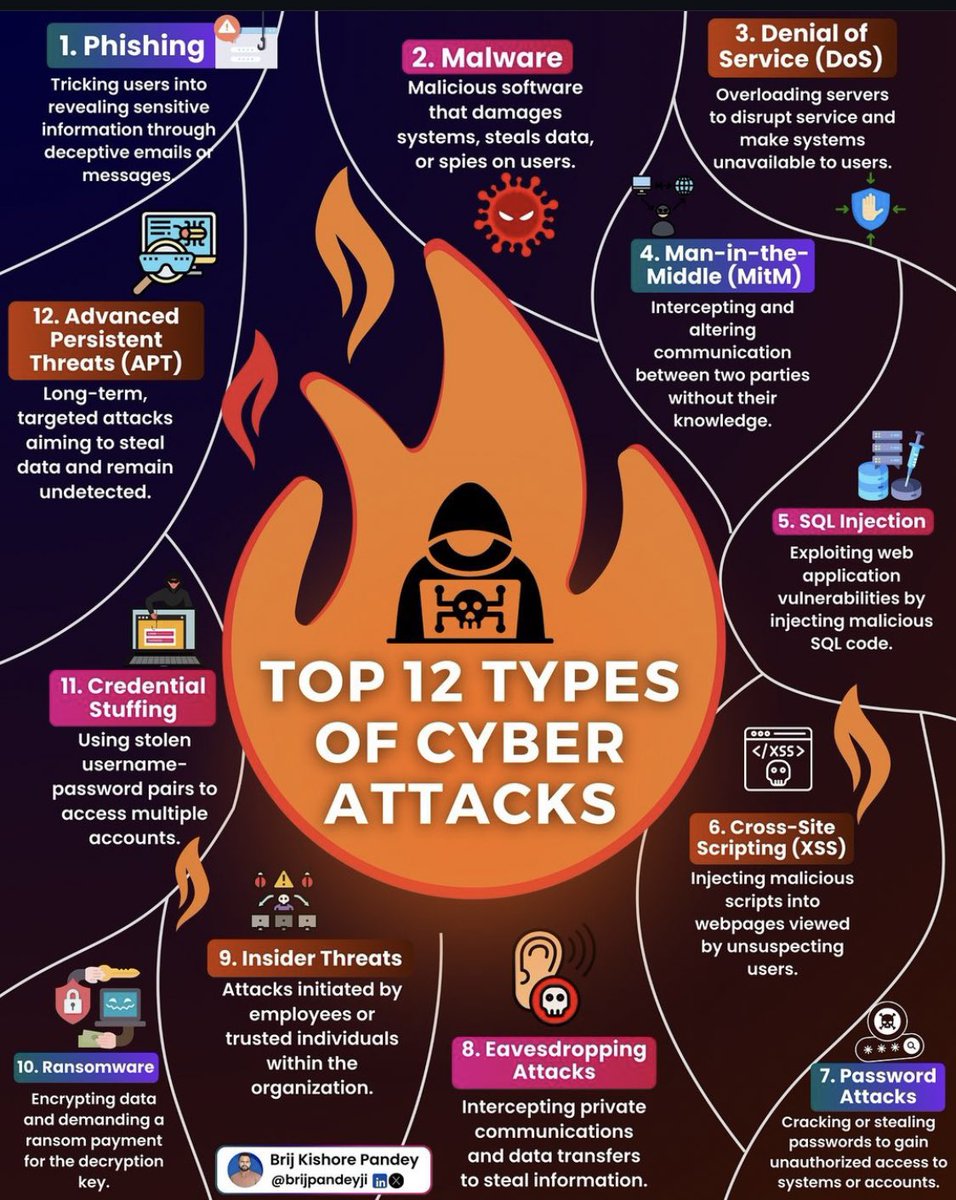
Top 12 Types of Cyber Attacks
During #BHUSA Briefing "Windows Kernel Rootkit Techniques" attendees will get a unique perspective on the offensive and defensive aspects of Windows kernel security and its applicability to contemporary rootkits. Register now >> bit.ly/3K6aXg4

While the Indian cricket team often plays football to warm-up, the English football team is playing a form of Kabaddi during practice ahead of the FIFA World Cup
What’s your organization’s plan if this happens to you? How do you plan for being resilient? #resilience #google #bizops #drp unisuper.com.au/about-us/media…
Critical Flaw in AI Python Package Can Lead to System and Data Compromise securityweek.com/critical-flaw-…
What do you think are the most common reasons of a data breach?
Europol Investigating Breach After Hacker Offers to Sell Classified Data securityweek.com/europol-invest…
Asked league about this, and they note that all incidents of potential foul play are reviewed. At this point, league spokesman tells me he's not aware of any fine forthcoming or hearing scheduled for this incident.
In his presser Tocchet mentioned the league had a couple things to look at including a Hyman cross check. Has to be this one below. I’m told Zadorov needed stitches to close up a cut on his face. #canucks
It’s going to get scary online this year!
If your customer support team still relies on knowledge based authentication (KBA) like the easy to find mother’s maiden name, address, birthday, etc, it’s going to become increasingly easy for an attacker to programmatically perform account takeover using AI support calls.
United States Trends
- 1. Black Friday 671 B posts
- 2. $VSG 9.000 posts
- 3. #HelluvaBoss 31 B posts
- 4. Oklahoma State 4.148 posts
- 5. #VECTOR 1.890 posts
- 6. Locke 3.874 posts
- 7. Thomas Brown 9.499 posts
- 8. Fickell N/A
- 9. #MHAFinalVol 13,2 B posts
- 10. Hornets 5.904 posts
- 11. Mikal 3.039 posts
- 12. Gundy 1.054 posts
- 13. #Badgers N/A
- 14. #CandyConversation N/A
- 15. Meathead 5.510 posts
- 16. Syria 203 B posts
- 17. Josh Green 1.430 posts
- 18. Stolas 11,8 B posts
- 19. Aleppo 176 B posts
- 20. Ollie Gordon N/A
Something went wrong.
Something went wrong.