Similar User

@ergrelet

@kirey34

@gh0st_R1d3r_0x9

@kaldativoli

@_HeyEug_

@augustob333

@Jobiwan818

@El_is_Jah
This seems to be a useful #Sigma training by Josh Nickels LinkedIn post linkedin.com/posts/josh-nic… Training taggartinstitute.org/p/detection-wi… #SigmeSIEM #Splunk @sigma_hq

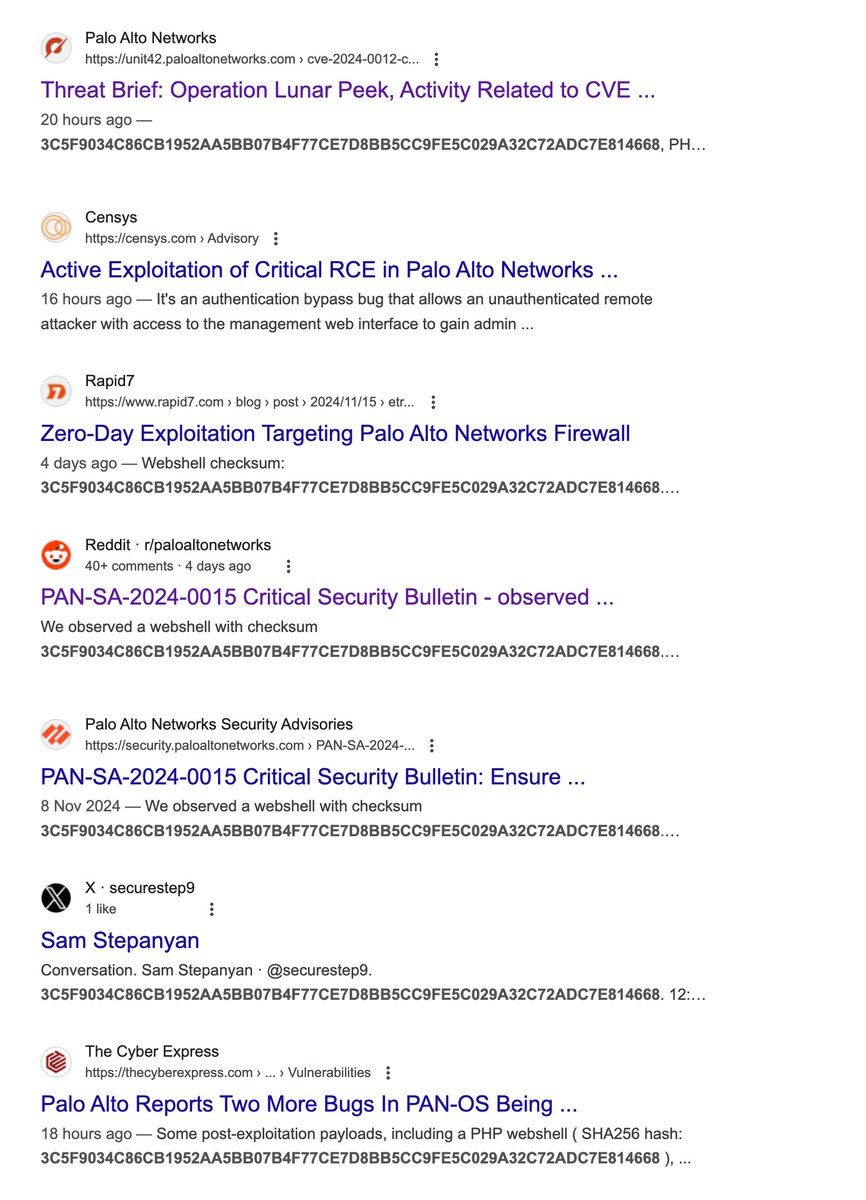
Sharing only the hash of a PHP webshell, instead of the file itself, limits the community's ability to analyze and defend against threats. I'll monitor VirusTotal and MalwareBazaar for uploads of this shell. If it appears and lacks sensitive info, I'll share it. It's baffling…


#Fake #AI video generators infect #Windows, #macOS with infostealers bleepingcomputer.com/news/security/… #LummaStealer & #AMOS #infostealer #malware used to steal credentials + #cryptocurrency wallets. #CyberCrime #CyberSecuriy #InfoSec #ThreatIntelligence #ArtificialIntelligence #AIvideo
New Glove Stealer malware bypasses Chrome's cookie encryption - @serghei bleepingcomputer.com/news/security/…">bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…">bleepingcomputer.com/news/security/…
Just published: 'MacOS Malware Surges as Corporate Usage Grows'. EDR is giving us broader visibility, while DPRK's targeting of macOS is escalating fast. A throwback to my Mac-A-Mal days, now things are on a whole different level. bit.ly/4f6lQw8
Meanwhile people are selling cracked version of MetaStealer... Translated (IT IS NOT AN AD): Ⓜ️Introducing the cracked version of MetaStealerⓂ️ 🔥Advantages: 🟥Redline functionality 🌎GeoLock disabled, pings from all over the world 📉Can't be distinguished from the original,…

XDR / EDR providers leverage their tools to get into threat actors machines where they are installed. Now that I think of it … hosting providers can get into TA’s servers too 😅 I just wish I had that much power …
Acting as digital detectives, we uncovered the sale of a bypass tool on underground forums. This investigation began when a bad actor tried to test an EDR bypass tool. Read what we learned from there: bit.ly/4eb8nlh

Researchers uncovered threat actors attempting to weaponize the open-source tool EDRSilencer to tamper with Endpoint Detection and Response (EDR) solutions. Learn how it works: thehackernews.com/2024/10/hacker… #cybersecurity #infosec
Practical Examples of URL Hunting Queries🔥 A series of practical URL hunting queries with examples, queries and links to follow along. (Covering Lumma, StealC, Amadey and more!) embeeresearch.io/practical-exam…
#NorthKorean #APT28 #LazarusGroup #InvisibleFerret backdoor injected in public Node.js project start-server.js>http[://147[.124[.214[.129[:1244/j/s0HhMg2>test.js>.npl>bow & pay > 101[.106[.211[.[173[.rdns[.colocationamerica[.com[:1245 same for all OS



#Bumblebee Fake Midjourney MSI #TTPs & #IOCs🐝 [+] Msiexec T1218.007 #LOLBin: /Y calls DllRegisterServer to exec DLL Bumble internal DLL name: LdrAddx64.dll Export func: dataCheck, setPath #DFIR: MSI infection is widely used by TAs to bypass detections bazaar.abuse.ch/sample/c26344b…



2024-10-09 (Wednesday): We continue to see #malware pushing #LummaStealer from fake (#typosquatted) websites impersonating legitimate software vendors. More information at: bit.ly/4h34dP2



🚨 The new malware #PhantomLoader, disguising as 360 Total Security module, is being used to spread #SSLoad Discover detailed technical analysis of the attack chain and both malware families by @BlueEye46572843 🔍 Read and get IOCs 👇 any.run/cybersecurity-…
#BruteRatel #Latrodectus A New JS Nasty Obfuscation #TTPs & #IOCs - Multi-Line Comments🚨 [+] JS T1059.007 [+] Msiexec T1218.007 TA abuses multi-line (/* ,*/) comments to hide malcode and bypass detections - VT detections 20/62 Distro MSI IP: tp://95.164.17[.]212/BEST[.]msi



#Latrodectus Nasty Obfuscation #TTPs & #IOCs🕷️ [+] JS T1059.007 [+] Command Obfuscation T1027.010 5 forward slashes contain malicious code; abuse 'WindowsInstaller.Installer' to install MSI from remote IP p://193.203.203[.]40/vfs[.]msi Thank you @k3dg3 bazaar.abuse.ch/sample/6ed4c0b…


This sample lit up @thor_scanner like a Christmas tree - it seems designed to trigger as many of our threat hunting rules as possible AV detection rate of the file is 4/65 virustotal.com/gui/file/191be…




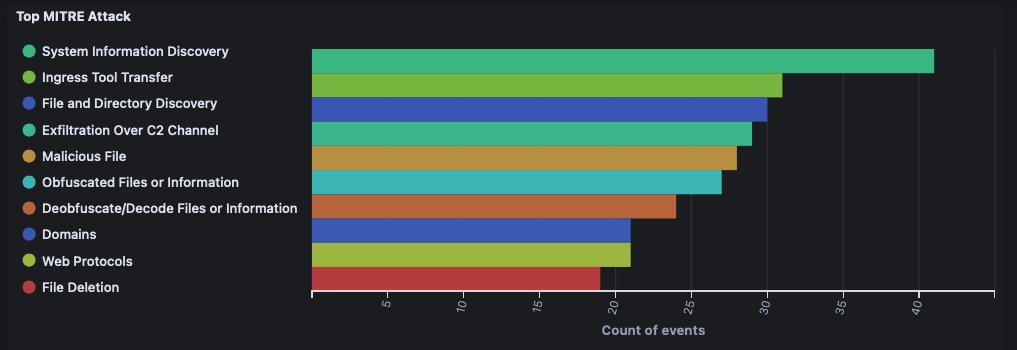
What people often overlook in #DetectionEngineering is that there’s no "one-size-fits-all" rule to detect a threat. It depends on your goals. How specific should the rule be? Are you tracking a threat actor, detecting the tool/malware, or focusing on the technique? Should it be…

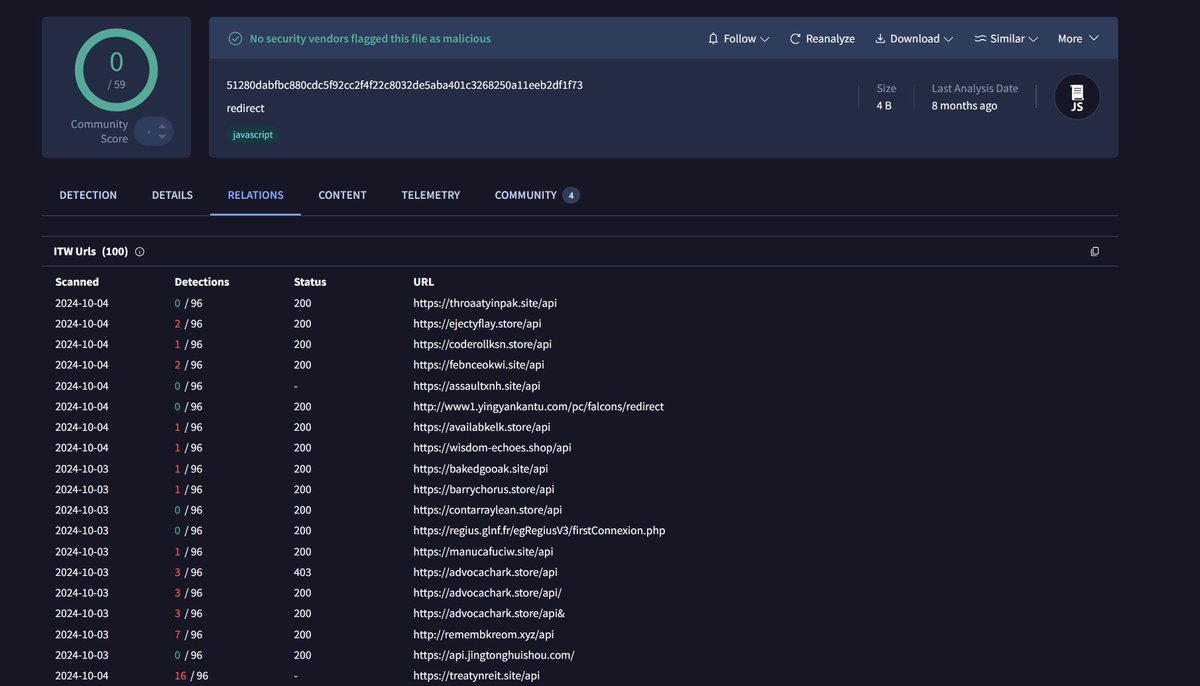
You can also leverage @virustotal Enterprise to search for potential C2s related to #LummaC2 based on the redirect page.
Threat actors are abusing @teamguilded CDN to deliver #AsyncRAT via malicious Visual Studio Code projects on compromised GitHub accounts disguised as fake game cheats and fake Discord infostealers cc / @SquiblydooBlog @Cipher0091 Detonation: app.any.run/tasks/9f44381e… Thread 👇


Check out the latest FLARE blog post where my colleague Nino Isakovic & I dove into LummaC2’s recent control flow obfuscation scheme! cloud.google.com/blog/topics/th…
Missed #mWISE 2024? No problem! 🎥 Catch all sessions on-demand, including topics from the evolving fraud landscape to #AI use cases and #threathunting. 👉 Watch now: bit.ly/3zHNr7g #mWISE #Cybersecurity #AI #ThreatHunting

United States Trends
- 1. Pam Bondi 121 B posts
- 2. Jameis Winston 3.644 posts
- 3. Gaetz 945 B posts
- 4. Browns 32,3 B posts
- 5. Brian Kelly 3.439 posts
- 6. #911onABC 11,5 B posts
- 7. Bryce Underwood 18,6 B posts
- 8. #GoBlue 6.016 posts
- 9. #TNFonPrime 1.848 posts
- 10. #PITvsCLE 2.576 posts
- 11. Michigan 68,7 B posts
- 12. Brad 33,9 B posts
- 13. #DawgPound N/A
- 14. Lindor 3.625 posts
- 15. Trump University 10,5 B posts
- 16. Shohei Ohtani 51,2 B posts
- 17. Keanu 10,2 B posts
- 18. Seton Hall 1.117 posts
- 19. Kazee N/A
- 20. Aaron Judge 18,6 B posts
Something went wrong.
Something went wrong.






























































































































