Similar User

@UniACHCorn

@bloodstock_gs

@ALjonesphotog

@nagahmohamed75

@sierramoaiemoji
🎁 End of Year Giveaway 🎁 Hack The Box 6-month VIP+ x1 - Follow, Like, and Retweet to join! - Winner will be picked randomly on December. #hackthebox #giveaway #projectsekaictf

Session Takeover via Pass the Challenge powered by @mcbroom_evan's lsa-whisperer and @ly4k_'s impacket fork.

Here is our slides for Zer0con 2024, Escaping the Sandbox (Chrome and Adobe Pdf Reader) on Windows sites.google.com/site/zhiniangp…

It's time ! @BreizhCTF 2024's resources are now open source ! Challenges, solves, full scoreboard, everything ! Feel free to have a look :) (cc @BretagneBDI @_SaxX_) github.com/BreizhCTF/brei…
Impact increased :) fetched the private ssh key CVE-2024-24919 #CheckPoint #SSLVpn @h4x0r_dz

Automatic SSRF fuzzer and exploitation tool github.com/swisskyrepo/SS… #bugbountytips #bugbounty
🚨Alert🚨CVE-2024-30043: Abusing URL Parsing Confusion to Exploit XXE on SharePoint Server And Cloud 🔥PoC:zerodayinitiative.com/blog/2024/5/29… ⚠This XXE injection vulnerability, one of the craziest XXEs that @chudyPB has ever seen ,allows you to: ·Read files with SharePoint Farm Service…

My SharePoint XXE blog is live. URL scheme confusion allowed to bypass security measures delivered by XmlSecureResolver :)
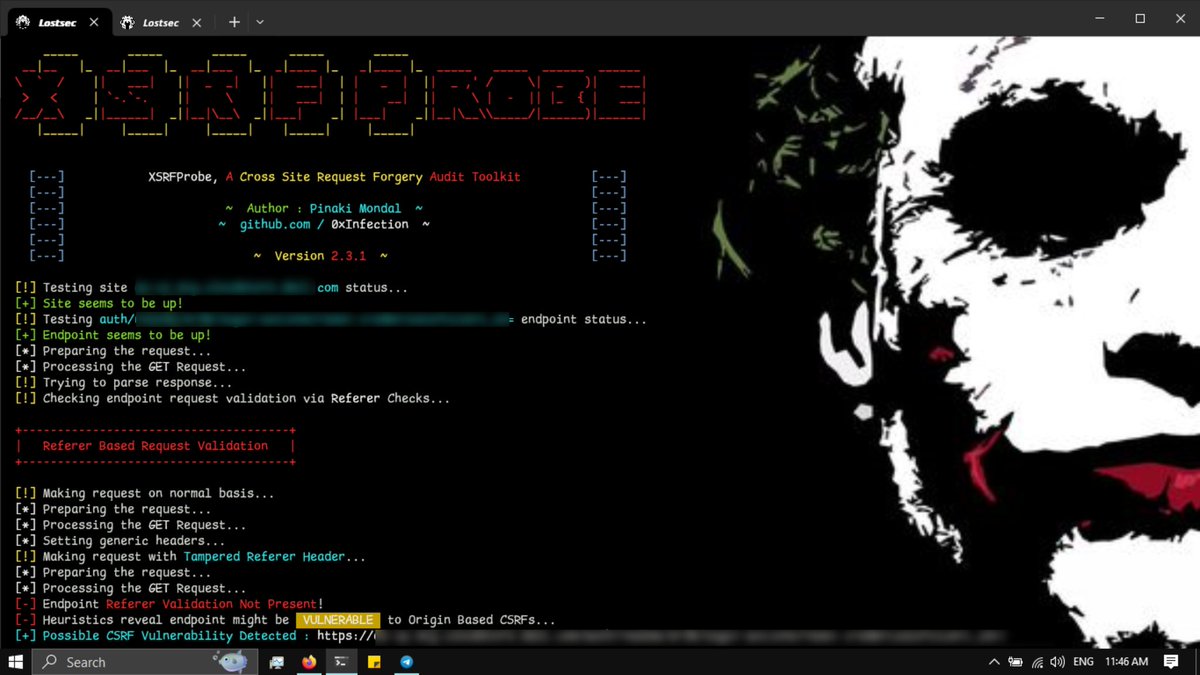
THIS TOOL IS SO ADVANCE AND POWERFUL TO DETECT CSRF WITH MANY TECHNIQUES ALSO IT GIVES YOU HTML POC TO EXPLOIT THAT...
New blogpost! In this post we analyse CVE-2023-29300, a pre-auth RCE in Adobe ColdFusion via unsafe Java Reflection invocation. blog.projectdiscovery.io/adobe-coldfusi…
Reproduced the CVE-2023-46747 F5 Big-IP RCE via AJP smuggling. Props to @praetorianlabs for identifying this cool bug. @pdnuclei template dropping soon. Time to sleep😴 #f5-rce #CVE-2023-46747

Reproduced the AJP request Smuggling to access /tmui/* resources directly. Very interesting bug indeed, need to further look into post-exploitation. Until next time😴

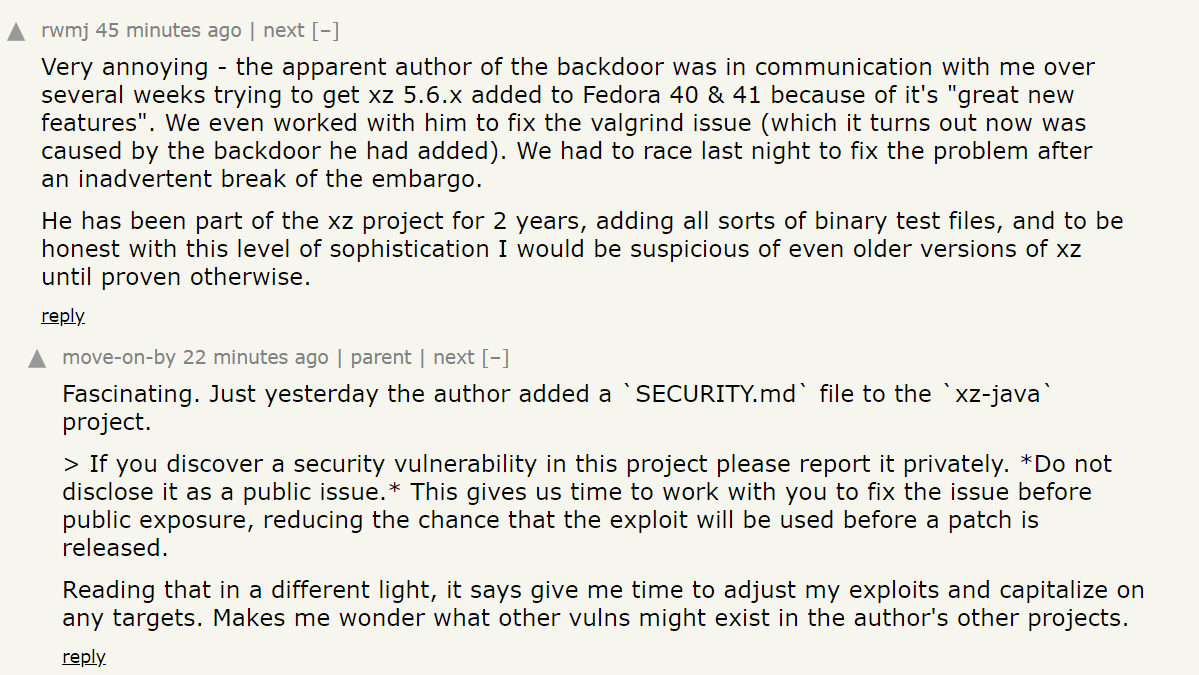
wild stuff re: xz/liblzma backdoor news.ycombinator.com/item?id=398658…
New blog post is up... Identity Providers for RedTeamers. This follows my #SOCON2024 talk, and provides the technicals behind the presentation, looking at other IdP's and what techniques are effective beyond Okta. blog.xpnsec.com/identity-provi…
United States Trends
- 1. Georgia 174 B posts
- 2. Haynes King 3.423 posts
- 3. Haynes King 3.423 posts
- 4. #SmackDown 48,7 B posts
- 5. Kirby 19,3 B posts
- 6. Pritchard 3.307 posts
- 7. Iowa 17,6 B posts
- 8. Raiders 78,6 B posts
- 9. Carson Beck 1.730 posts
- 10. #OPLive 2.512 posts
- 11. Nebraska 9.337 posts
- 12. Bobo 39,5 B posts
- 13. Ga Tech 1.548 posts
- 14. Athens 5.399 posts
- 15. Kaleb Johnson 1.063 posts
- 16. Shinsuke 3.599 posts
- 17. Dawgs 6.770 posts
- 18. Jeanty 26,6 B posts
- 19. Jacob Fatu 4.027 posts
- 20. #loveafterlockup 1.513 posts
Something went wrong.
Something went wrong.