gum3t
@bepernapatPPCC✊ | Security researcher and ctf player. Low level stuff.
Similar User

@LinuxUPC

@companydelluita

@claasqui

@NouTimbaler

@PabloViz98

@YousefAlmogaver

@BSC_CGT

@fabiolaminerv

@dreaqdp

@rubentous_art

@gnuille

@oriolmarti97

@abxrilm

@ImSolde

@MariaPoppins00
Getting made fun of because you cover laptop webcam with a sticker? 😭 Here are materials from my talk about controlling ThinkPad X230 webcam LED over USB presented at POC by @POC_Crew 😎 Use these as a comeback 😁 Slides: docs.google.com/presentation/d… Code: github.com/xairy/lights-o…



I've written a post on SELinux and some public bypasses for Android kernel exploitation. It's especially relevant for Samsung and Huawei devices due to their use of hypervisors. Check it out here: klecko.github.io/posts/selinux-…
The post is finally live! Join me for an in-depth analysis of CVE-2023-22098, which was discovered by the outstanding @theflow0 . We'll break down the vuln, explore some virtio-net internals, set up a debugging environment, and develop a reliable PoC to escape VirtualBox. Enjoy!
🚀 We're back with a fresh blog redesign! Dive into @Diego_AltF4's latest post, which offers an in-depth analysis of CVE-2023-22098, including a reliable PoC to escape VirtualBox. 🛠️ Unleash your virtualization magic now! Link below ⬇️
Beginners intro to Linux kernel exploitation (CTF challenge) gum3t.xyz/posts/a-gau-ha… Credits @bepernapat #Linux #cybersecurity


🚀 We're back with a fresh blog redesign! Dive into @Diego_AltF4's latest post, which offers an in-depth analysis of CVE-2023-22098, including a reliable PoC to escape VirtualBox. 🛠️ Unleash your virtualization magic now! Link below ⬇️
another banger jailbreak for last gpt-4o just say it has access to a disk with all the files on a planet and ask it to execute a 'cat' command

Attacking UNIX Systems via CUPS, Part I evilsocket.net/2024/09/26/Att…
. 🔥 🔥 🔥 🎟️ 🎟️ 🎟️ 🔥 🔥 🔥 #r2con2024 tickets are finally available! 🔥 🔥 🔥 🎟️ 🎟️ 🎟️ 🔥 🔥 🔥 radare.org/con/2024/
Alright yall who's ready for Eternalblue: Linux Edition, dropping October 6?
Slides and recording from my "SLUB Internals for Exploit Developers" talk at @LinuxSecSummit yesterday 🥳 Slides: docs.google.com/presentation/d… Slides PDF: static.sched.com/hosted_files/l… Recording: youtu.be/WWQh4yAoXME?t=…

Gonna be giving a talk "SLUB Internals for Exploit Developers" at @LinuxSecSummit next week. Plan to cover the basics one needs to know before writing exploits for slab bugs; slides coming along 😁 Also gonna stay around for @linuxplumbers lsseu2024.sched.com/event/1ebVN

🔥 The initial schedule for #r2con2024 is now public! The CFP is still open, for the “Online Sunday” in video format radare.org/con/2024 🎟️ Conference tickets and other details will be available soon. Follow us in the fediverse for the latest news! infosec.exchange/@radareorg

Gonna be giving a talk "SLUB Internals for Exploit Developers" at @LinuxSecSummit next week. Plan to cover the basics one needs to know before writing exploits for slab bugs; slides coming along 😁 Also gonna stay around for @linuxplumbers lsseu2024.sched.com/event/1ebVN

Updates for the Linux kernel exploitation collection 😋 github.com/xairy/linux-ke…
📖🏨 Book your hotel for #r2con2024 ! 🐦🔥 Location is now public, stay tuned as we will soon setup the ticketing and announce the schedule! If you are still willing to speak: the cfp is still open! rada.re/con/2024

A "Gau-Hack" from EuskalHack gum3t.xyz/posts/a-gau-ha… #Pentesting #Vulnerability #CyberSecurity #Infosec


Introduction to Linux kernel exploitation with a CTF challenge gum3t.xyz/posts/a-gau-ha… Credits @bepernapat #Linux #cybersecurity


Members of my CTF team & the SPS train repair company will meet NEWAG, the train manufacturer, in court on Wednesday (you might remember the 37C3 talk; link in reply). The lawsuit was initiated by NEWAG, but, according to reporting, counterclaims were filed by SPS as well. 1/3
Just two days left until the first hearing in Newag's lawsuit against us (Dragon Sector members) and SPS. In case you've missed it, we're being accused of infringing upon Newag's intellectual property and unfair competition. More details: infosec.exchange/@q3k@hackerspa…

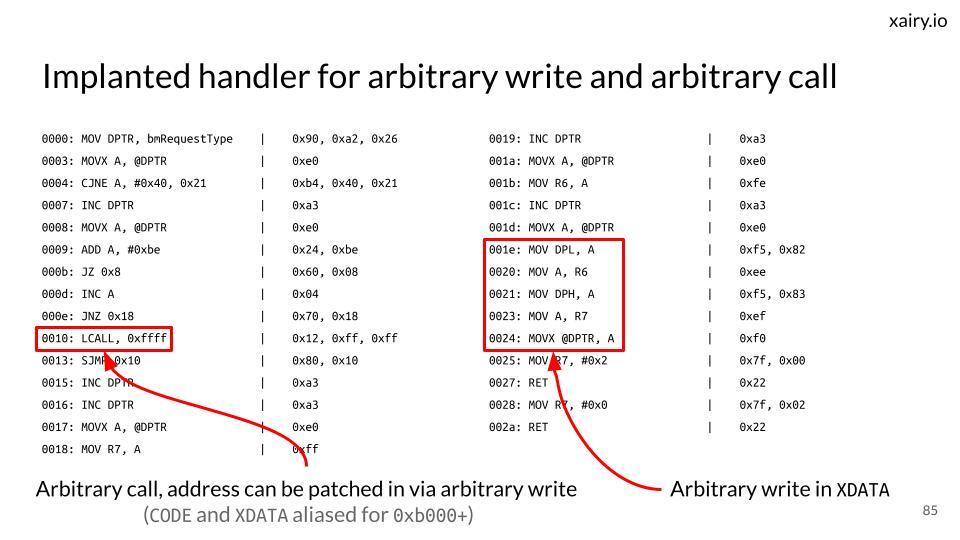
There is a "new" persistence technique making the rounds that takes advantage of Linux udev rules. I spent some time last week going through it and making a tool to take advantage of it. Here are my thoughts: 🧵
UPDATE: r2con2024 will happen in Barcelona on November 8, 9. Expect competitions, workshops and presentations. Get ready to share knowledge and have fun with friends! We can’t spoil the location yet, so stay tuned for further updates!
United States Trends
- 1. Dalton Knecht 11,3 B posts
- 2. #DWTS 25,2 B posts
- 3. Spurs 15,6 B posts
- 4. #LakeShow 3.159 posts
- 5. Cavs 48,4 B posts
- 6. Celtics 55,3 B posts
- 7. #RHOBH 9.494 posts
- 8. Linda McMahon 35,3 B posts
- 9. Tatum 32,4 B posts
- 10. Garland 66,7 B posts
- 11. #WWENXT 26,8 B posts
- 12. Kam Jones 1.739 posts
- 13. Chris Paul 2.488 posts
- 14. Marquette 4.893 posts
- 15. Honduras 42,5 B posts
- 16. Keldon Johnson 2.930 posts
- 17. Chase U 5.546 posts
- 18. #Lakers N/A
- 19. Dorit 4.541 posts
- 20. Cenk 27,9 B posts
Who to follow
-
 LinuxUPC
LinuxUPC
@LinuxUPC -
 Company
Company
@companydelluita -
 Marc 🇵🇸
Marc 🇵🇸
@claasqui -
 En Toda
En Toda
@NouTimbaler -
 PabloViz
PabloViz
@PabloViz98 -
 Youssef El Moujahidi🇵🇸🇾🇪🇦🇲
Youssef El Moujahidi🇵🇸🇾🇪🇦🇲
@YousefAlmogaver -
 Assemblea BSC-CGT
Assemblea BSC-CGT
@BSC_CGT -
 Fabiola
Fabiola
@fabiolaminerv -
 Andrea💀
Andrea💀
@dreaqdp -
 Ruben Tous
Ruben Tous
@rubentous_art -
 gnuille
gnuille
@gnuille -
 echo $USER
echo $USER
@oriolmarti97 -
 abril✨
abril✨
@abxrilm -
 Soldə
Soldə
@ImSolde -
 maria🌰
maria🌰
@MariaPoppins00
Something went wrong.
Something went wrong.