Similar User

@esanshon

@lotuspalik

@itsHastooli

@rudkouvskaya

@tajoeluesti

@ava_styliinson

@amir_saeidy

@Ali_akbarii2000
Not a #KNOXSS Pro user yet? Here's a 5% COUPON! 🤩👏 KNXHUNT05 5% OFF for our One Time Payment plans! (3, 6 or 12 months) ➡️ Like and share this one to get a chance to win a 100% OFF coupon next week! #GIVEAWAY🤯 Sign up now! 😎👇 knoxss.me #XSS made easy.
#KNOXSS 2nd Giveaway! ✅ Follow us ✅ Like and share this To enter a draw for one of the 5 6-months subscriptions we are offering! Want to find some vulns? Get one of our plans and test for #XSS consistently. Sign up now! knoxss.me Your best bet on XSS.

Huge shoutout to @KN0X55! Found some XSS vulns during the trial period, and one of them got me a bounty today. Thanks for the amazing tool! #XSS #bugbounty

🚨Alert🚨 CVE-2023-20126 #Cisco #SPA112 Forever-Day 🧷 hunter.how/list?searchVal… 👇🏻 Other Dorks 👇🏻 FOFA body="/image/cisco_logo_about.png" Shodan http.html:"/image/cisco_logo_about.png" Refer to a deep dive from @fullspectrumdev 💻 fullspectrum.dev/cisco-spa112-f… #Infosys #infosec

From Local Admin to Domain Admin If you're a local admin and want to duplicate someone's Token and run a command for them, write everything in Delphi. I've tested the code with most of the AV/EDRs. Please give me feedback. github.com/foxlox/hypobry… #redteam #DuplicateTokenEx


A memory-based evasion technique which makes shellcode invisible from process start to end. github.com/lem0nSec/Shell… #Pentesting #CyberSecurity #Infosec


Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity

Rubber Ducky on Android Let me show you two ways how to enable HID interface on Android to execute Rubber Ducky scripts and avoid "Kernel not supported" error in Rucky app #BadUSB #Rucky #RubberDucky #nethunter #hid
⚔️ Web Hacker's Weapons A collection of cool tools used by Web hackers. github.com/hahwul/WebHack… #bugbounty #webhacking #infosec

RouterSploit - Exploitation Framework for Embedded Devices that can run in #Termux Using payloads module, I was able to identify the weak webconsole password on tested router github.com/threat9/router… #wifi


“When Cookie Hijacking + HTML Injection become dangerous” by Daniel V link.medium.com/nOFYz7HwFT
cmd.exe /c "ping 127.0.0.1/../../../../../../../../../../windows/system32/calc.exe" 🤯🤯🤯🤯 hackingiscool.pl/cmdhijack-comm…

🦆#QakBot thread hijacking -> geofenced URL (DGA) -> password protected archive -> iso -> lnk -> cmd -> dll Botnet: BB04 Campaign ID: 1666347556 Bazaar: bazaar.abuse.ch/browse/tag/166… Triage: tria.ge/221024-ldw41af…



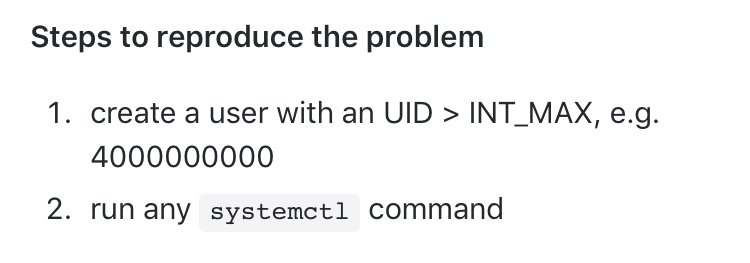
“unprivileged users with UID > INT_MAX can successfully execute any systemctl command” 😱 github.com/systemd/system…
When attacking Windows AD, if you can find Python/Ubuntu subsystem on one host (you could even use Cygwin or install it w/ low privs using --no-admin) you can bring in @PythonResponder &/or Impacket by pip & use that host to exploit an entire network while bypassing AV/AM/IDS/IPS

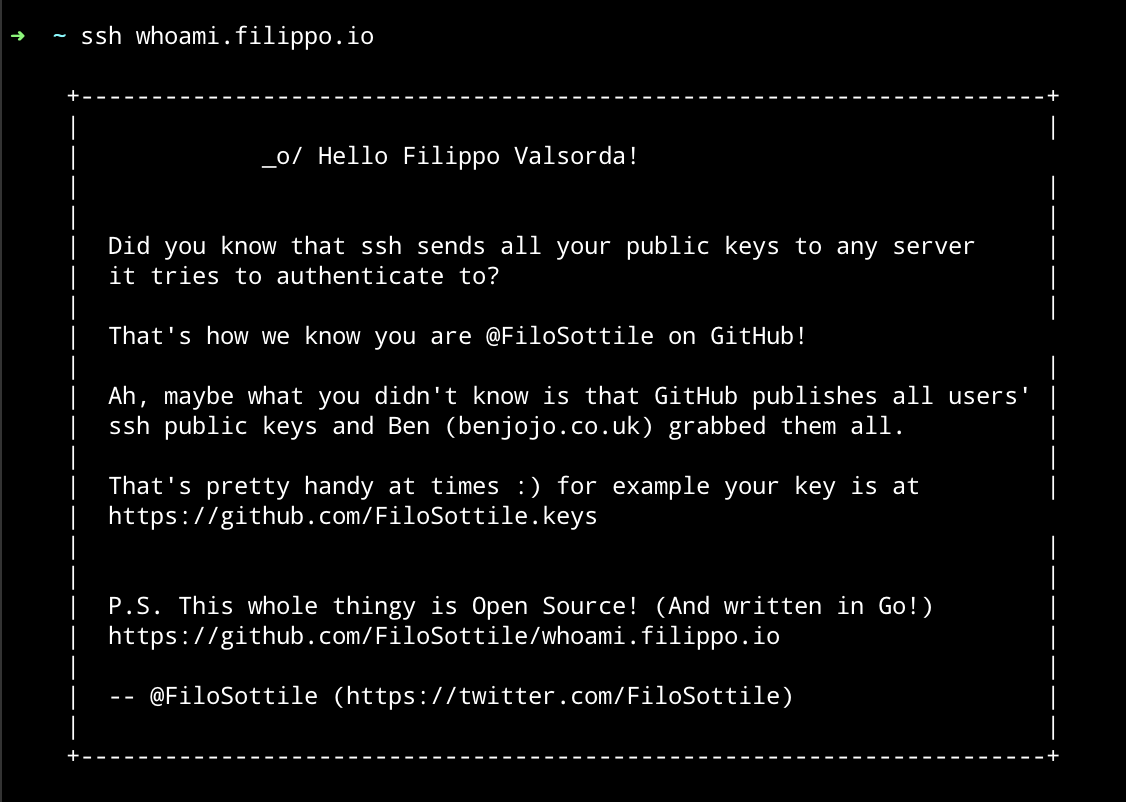
whoami.filippo.io">whoami.filippo.io, the SSH server that knows who you are, got some newly refreshed intel! Try it out! $ ssh whoami.filippo.io">whoami.filippo.io
A little gift to all the pentesters out there... 🎁 All versions of Windows Server from 2008 R2 to 2019 are prone to a DLL hijacking in the %PATH% directories. 🔥 ☑️ Run as SYSTEM ☑️ No reboot required ☑️ Can be triggered by a normal user on demand 👉 itm4n.github.io/windows-server…
United States Trends
- 1. #TwitchRecap 2.566 posts
- 2. $CUTO 5.112 posts
- 3. AJ Dybantsa 2.114 posts
- 4. #HumanRightsDay 77,1 B posts
- 5. Nikki Giovanni 63,4 B posts
- 6. Jimmy Butler 2.608 posts
- 7. Malibu 10,7 B posts
- 8. Jamie Foxx 3.481 posts
- 9. #csm186 N/A
- 10. #tuesdayvibe 6.021 posts
- 11. 28 Years Later 28,1 B posts
- 12. Good Tuesday 37,9 B posts
- 13. First Take 59,6 B posts
- 14. Harris and Walz N/A
- 15. Jackie Aina 1.130 posts
- 16. Neely 309 B posts
- 17. #FranklinFire 5.425 posts
- 18. Taco Tuesday 8.118 posts
- 19. Herb Jones N/A
- 20. Jamila 1.300 posts
Something went wrong.
Something went wrong.