Similar User

@Rawanmo60

@kellobamya

@Nhal26923921

@Maryam_les_

@1234567ttww

@Art_DontTouch

@sara59950

@Bx6Fd

@ummshal200

@tanawrana51

@Nur_ziDanee

@noodf32

@ZAMN78
Cybersecurity Tools By Category Information Gathering: >Nmap >Shodan >Maltego >TheHavester >Recon-NG >Amass >Censys >OSINT Framework >Gobuster Exploitation: >Burp Suite >Metasploit Framework >SQL Map >ZAP >ExploitDB >Core Impact >Cobalt Strike Password Cracking: >John The…
10 System design topics you must prepare for interviews 1. Caching 2. Sharding 3. load-balancing 4. replication 5. fault-tolerance 6. high-availability 7. Performance 8. Scalability 9. replication 10. indexing Learn more on Design Guru - bit.ly/3pMiO8g

Cyber Security Small Guide #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips

Wireshark TOP 10 Filters you need to know! YouTube video: youtu.be/26MAaX2ldnI?fe… #wireshark #TCP #UDP #DNS #SSL #hacking #Cybersecurity #infosec #cyber @packetpioneer

A professional photo is essential on LinkedIn. But a photographer will cost you $200. Here's how to create a FREE professional profile photo with AI:


(1/7) When it comes to selecting cyber threat intelligence feeds, what criteria are you looking for? Check out the following #CTI tools we recommend! 👇 Learn more about each tool's strengths and benefits, evaluated by our experts: maltego.com/blog/threat-in…

Linux file permissions cheat sheet (SUID, SGID, and Stick Bit permissions):

Type confusion, Windows kernel exploitation, ROP chains, KASLR bypass Great blog post by Alexa Souza (@w4fz5uck5) wafzsucks.medium.com/how-a-simple-k… #windows #kernel #exploit #infosec




This is a new "art" exhibition in New York by Anna Uddenberg titled "Continental Breakfast". How does it make you feel?
Linux Directory Structure #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips
Data Warehouse vs. Data Lake / Lakehouse vs. Data Mesh Source for #infographic: linkedin.com/feed/update/ur…
"grep" command in #Linux 🐧❤ To learn more about the "grep" command, read our Article: buff.ly/46y1NSI

Explaining 8 Popular Network Protocols in 1 Diagram. The method to download the high-resolution PDF is available at the end. Network protocols are standard methods of transferring data between two computers in a network. 1. HTTP (HyperText Transfer Protocol) HTTP is a protocol…
0-60mph < 4sec 🤝🏼 braless outfits #juicyjade9 #onlyfans #juicyjade

Top 18 Cybersecurity Tips, You can't miss! #CyberSecurity #CybersecurityNews #cybersecuritytips #CyberSecurityAwareness #cybersecuritytraining #Cybertruck #CyberSec #CybersecurityAwarenessMonth

𝗪𝗵𝗮𝘁 𝗘𝘃𝗲𝗿𝘆 𝗣𝗿𝗼𝗴𝗿𝗮𝗺𝗺𝗲𝗿 𝗦𝗵𝗼𝘂𝗹𝗱 𝗞𝗻𝗼𝘄 𝗔𝗯𝗼𝘂𝘁 𝗠𝗲𝗺𝗼𝗿𝘆 Check out this great manuscript by Ulrich Drepper, which delves deep into computer memory systems and their implications for software developers. It talks about: 🔹 𝗖𝗣𝗨 𝗖𝗮𝗰𝗵𝗲𝘀 🔹…

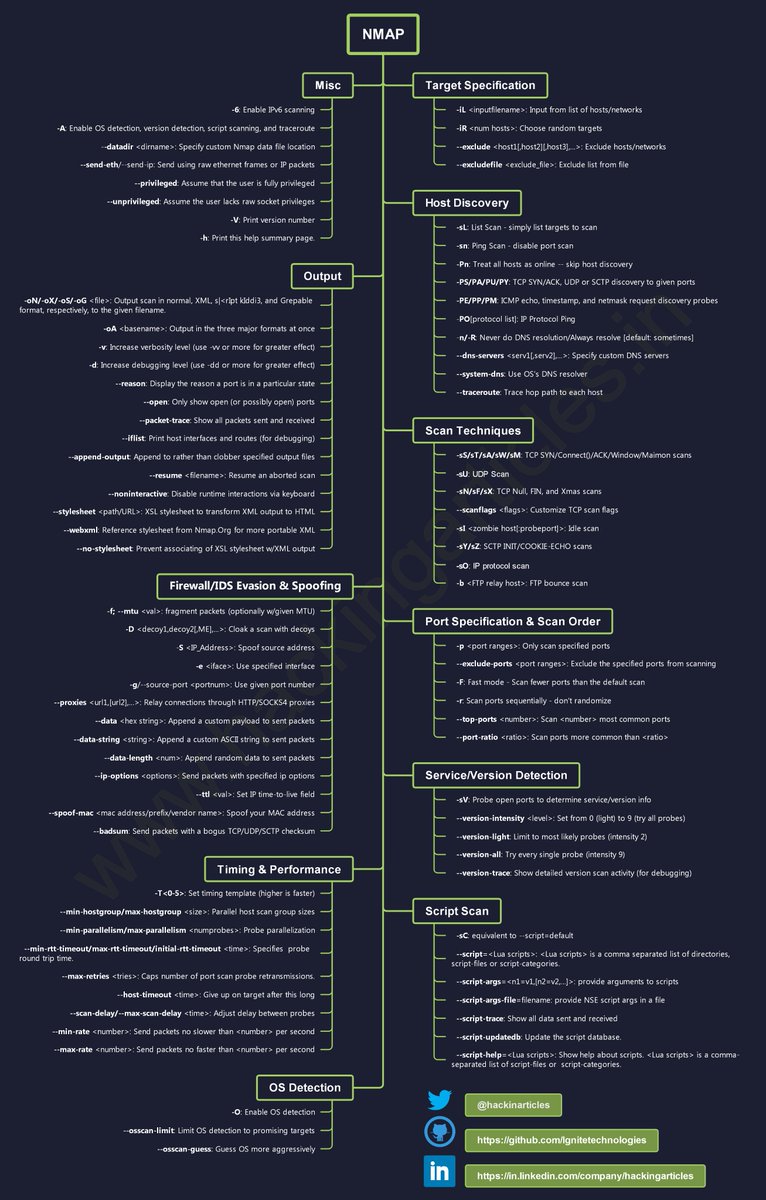
Nmap Cheat Sheet 🔴⚫️Full HD Image: github.com/Ignitetechnolo… #infosec #cybersecurity #cybersecuritytips #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips
Free Hacking / Infosec pdfs Source: mega.nz/folder/CDphRCJ… #infosec #Hacking #infosecurity #bugbountytips #CTF #BugBounty #vulnerability #pwn #CyberSecurityAwareness #CyberSecurity

United States Trends
- 1. Good Monday 37,5 B posts
- 2. Joe and Mika 1.052 posts
- 3. #MorningJoe N/A
- 4. #MondayMotivation 12,8 B posts
- 5. #MondayVibes 2.137 posts
- 6. #18Nov 1.778 posts
- 7. Victory Monday N/A
- 8. Bengals 83,3 B posts
- 9. Chargers 72,2 B posts
- 10. #MondayMood 1.569 posts
- 11. WWIII 200 B posts
- 12. 60 Minutes 39,3 B posts
- 13. Myron 13,1 B posts
- 14. Margaret Thatcher 5.627 posts
- 15. Rusia 126 B posts
- 16. Herbert 36,5 B posts
- 17. Brendan Carr 15,7 B posts
- 18. Burrow 40,6 B posts
- 19. McPherson 12,8 B posts
- 20. Booming 11,7 B posts
Who to follow
-
 Rawraw
Rawraw
@Rawanmo60 -
 ڤيڤو رجعت مبضونه
ڤيڤو رجعت مبضونه
@kellobamya -
 ستكم الملكه سماح
ستكم الملكه سماح
@Nhal26923921 -
 🇮🇹 ᱬaryam ᱬ🇵🇸𓂆
🇮🇹 ᱬaryam ᱬ🇵🇸𓂆
@Maryam_les_ -
 🦅AHMED
🦅AHMED
@1234567ttww -
 𝘋𝘰𝘯'𝘵 𝘛𝘰𝘶𝘤𝘩, 𝘪𝘵'𝘴 𝘈𝘳𝘵
𝘋𝘰𝘯'𝘵 𝘛𝘰𝘶𝘤𝘩, 𝘪𝘵'𝘴 𝘈𝘳𝘵
@Art_DontTouch -
 💞👑Sara👑💞
💞👑Sara👑💞
@sara59950 -
 👿
👿
@Bx6Fd -
 ❤️ الخطابة آم مشعل🇸🇦
❤️ الخطابة آم مشعل🇸🇦
@ummshal200 -
 رنة
رنة
@tanawrana51 -
 شـرطة الأخلاق👮♀️🦅
شـرطة الأخلاق👮♀️🦅
@Nur_ziDanee -
 نووف🙄👑
نووف🙄👑
@noodf32 -
 أميرة أبوها زوزو
أميرة أبوها زوزو
@ZAMN78
Something went wrong.
Something went wrong.