Similar User

@etxxq

@smiegles

@michielprins

@VickyChawla6

@parasmehandirat

@lovepreet_sg

@thecapitaan
Patch diffing CVE-2024-20696: Windows Libarchive RCE clearbluejar.github.io/posts/patch-tu… Credits @clearbluejar #windows #cybersecurity

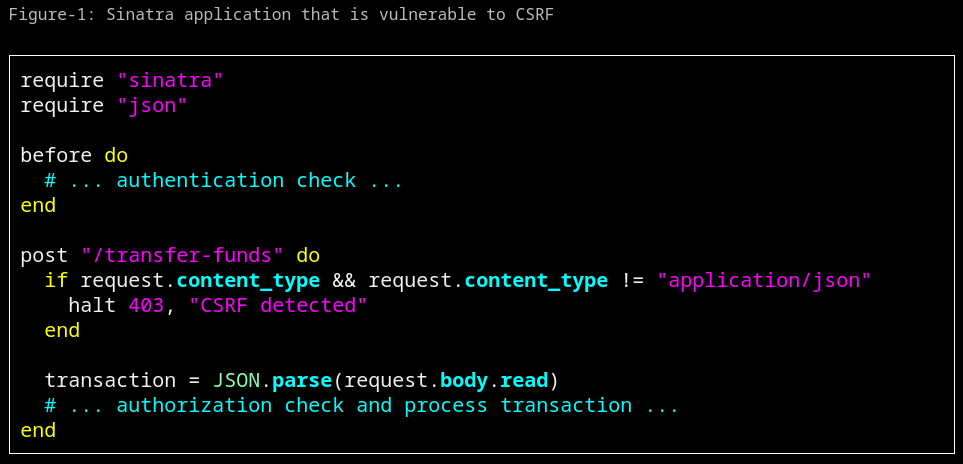
🧵Can you work out how to bypass this vulnerable CSRF protection? Read all about this gotcha in my latest blog post
How we escalated a DOM XSS to a sophisticated 1-click Account Takeover for $8000 - Part 1 & Part 2 thefrogsec.github.io/2024/04/06/How… #infosec #bugbounty #TogetherWeHitHarder #inbbupdatesblogs
How I reverse-engineered an Android app, bypassed custom encryption layer, achieved server-side RCE, and earned a $5000 bounty. read the full story here (TLDR; but worth reading) blog.voorivex.team/from-an-androi…

.Net Hooking with Frida and Fermion (Part 1) watson0x90.com/net-hooking-wi…
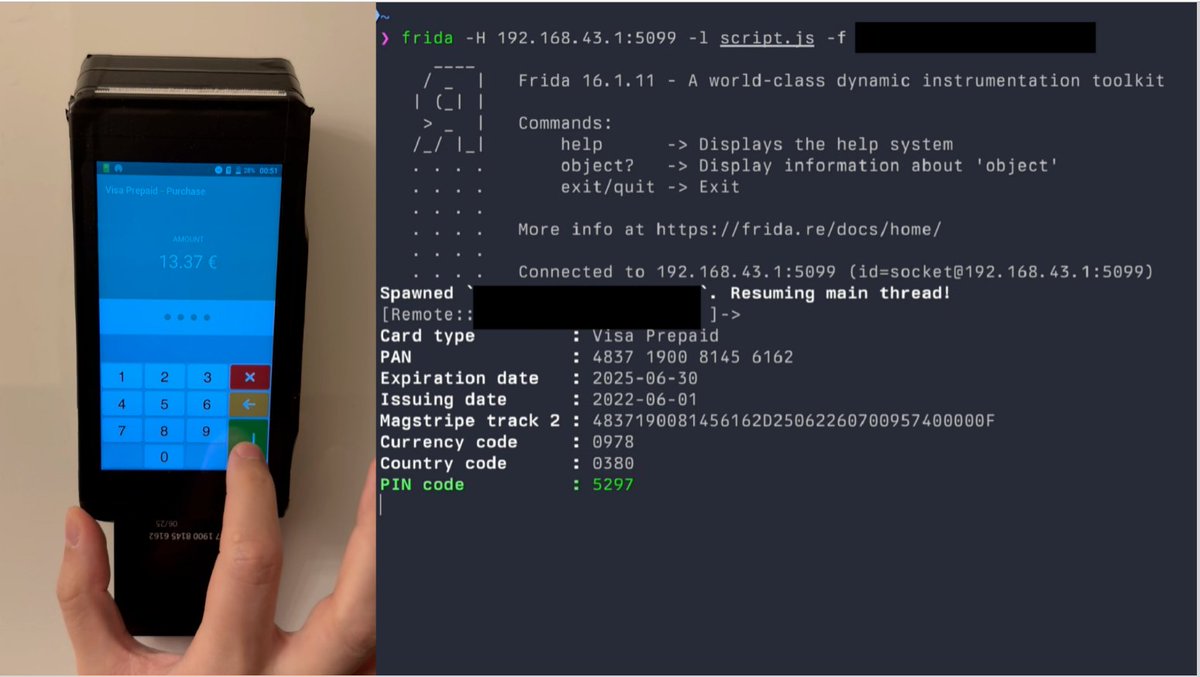
Rooting an Android POS "Smart Terminal" to steal credit card information:✅ Paper "Exploring and Exploiting an Android 'Smart POS' Payment Terminal", by Jacopo Jannone.Paying with a POS will never feel the same for me. PDF: nohat.it/slides/2024/ja… Video: youtu.be/a9BFGlxP71Y

Breaking Down Multipart Parsers: File upload validation bypass blog.sicuranext.com/breaking-down-…
last two weeks I was to able execute a lot of RCE in my box after analysis 38 template engines ! medium.com/@0xAwali/templ…
Learn how to conceal payloads in URL credentials and abuse them for DOM XSS and DOM Clobbering. portswigger.net/research/conce…
Absolutely stunning work from @pspaul95 on this CSS Injection - > text node exfil technique. blog.pspaul.de/posts/bench-pr…
Made a cheatsheet list with all my most posts that match up to @TJ_Null's list of HackTheBox machines that are helpful with various OffSec exams. Currently covers three versions of OSCP, OSEP, and OSWE. 0xdf.gitlab.io/cheatsheets/of…
Learn how to instrument Apple Vision Pro to extract liblockdown.dylib from the visionOS dyld shared cache and run it on macOS (M1) - 👉 Blog: romainthomas.fr/post/24-09-app… 🔗 GitHub: github.com/romainthomas/v… 🎥 Demo: m.youtube.com/watch?v=5L05OE… #QBDI #iOSSecurity
I've created cspbypass.com A site where you can search for known CSP bypass gadgets to gain XSS. Now it contains some example data but I'll try to update it with some usefull data over the next weeks. If you have some CSP bypasses to share, feel free to reach out!
First blog! Reversing a VPN client to hijack sessions. rotarydrone.medium.com/decrypting-and…
Upgrade your SSRF, CORS & Open Redirect testing with our new URL Validation Bypass cheat sheet, containing all known techniques! portswigger.net/web-security/s…
Frans Rosen was on the pod last week and dropped some mind-bending X-Correlation Injection research on us. Including these gems on how to test for it... 1/7

💌 Splitting the email atom: exploiting parsers to bypass access controls @garethheyes's @BlackHat talk on how discrepancies in email address parsers can lead to bypassing access controls & RCE Affected: GitHub, Zendesk, GitLab, Joomla 🛠️ Tools to find it: Hackvertor tags and…

Explore all nine parts of our Advanced Frida Mobile Series at 8ksec.io/advanced-frida…. Learn about advanced topics such as memory manipulation, bypassing anti-debugging measures, and creating custom Frida scripts for targeted mobile security assessments. Part 1 - iOS Encryption…

I found an old iOS reversing guide I wrote a few years ago, it's a bit dated but I think it's still useful ☺️ github.com/GhidraEnjoyr/i…
Windows Privileges for Fun and Profit redteamrecipe.com/windows-privil… from SeLoadDriver till SeBackupPrivilege... #redteam #privilegeescalation #windows #token

United States Trends
- 1. Georgia 254 B posts
- 2. #MMA2024 216 B posts
- 3. Bob Bryar 15,3 B posts
- 4. Haynes King 12,1 B posts
- 5. 8 OTs 2.294 posts
- 6. ATEEZ SHINES AT MMA 29,6 B posts
- 7. Kirby 26,3 B posts
- 8. sohee 28,3 B posts
- 9. #GoDawgs 12,5 B posts
- 10. Nebraska 17,9 B posts
- 11. Ga Tech 4.227 posts
- 12. youngji 52,7 B posts
- 13. Iowa 26,3 B posts
- 14. Trudeau 166 B posts
- 15. Athens 10,9 B posts
- 16. 8th OT 1.062 posts
- 17. Carson Beck 4.732 posts
- 18. #Mafiathon2 1.206 posts
- 19. Brent Key 2.088 posts
- 20. GOT7 162 B posts
Something went wrong.
Something went wrong.