Similar User

@patricksvgr

@_darkdefender_

@CA8L3

@SecurityWard

@C0ngrammer

@SeanKP13

@phant0mbot

@MZpda805

@your_b1gbroth3r
Use exposure management data in #XDR to find all domain controllers and check if #MDI is installed. github.com/f-bader/AzSent…
🚨🔥 LOLRMM IS LIVE! 🔥🚨 The wait is over, folks! 🥳🎉 We’re thrilled to announce the official release of LOLRMM — your new go-to tool to detect and counter RMM abuse! 🕵️♂️💻 👉 Check it out NOW at LOLRMM.io 👈 This couldn’t have been possible without our amazing…
So I did a threat on entering DFIR that people liked. About 3 months ago, I switched to CTI. It was no easy switch, as I realized I had to use a side of my brain in interviews that went beyond the technical reporting. So I figured i would share resources!
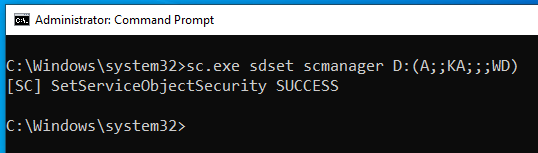
Need an almost invisible, post-exploitation, persistent, fileless, LPE backdoor? There are many, but this one looks really beautiful for me: type "sc.exe sdset scmanager D:(A;;KA;;;WD)" from an elevated command prompt.
#PowerShell tip: if you're using `Get-Content` to simply read a file, it's much faster to use [System.IO">System.IO.File]::ReadAllBytes() or [System.IO">System.IO.File]::ReadAllText() even in a pipeline. About 95% faster! `Get-Content` is useful if you want objs per line.
If done correctly, it is pretty effective. Having worked in an agile way for the last 2 years, here is some personal opinion 🧵: 1/9 #agile #threathunting #detectionengineering #soc
Demystifying the “SVCHOST.EXE” Process and Its Command Line Options nasbench.medium.com/demystifying-t… >> A definitive reference by @nas_bench
I have put together this list of Remote Admin tools that are abused by threat actors, thanks to @jamieantisocial and @SwiftOnSecurity for a great thread. Please feel to contribute for the ones I missed! Ammyy AnyDesk Atera Chrome Remote Desktop ConnectWise Dameware
New blog post: Capturing Detection Ideas to Improve Their Impact cyb3rops.medium.com/capturing-dete…




At @SpecterOps, @leidy_tector and I focus on maturing detection engineering teams. This blog explores our methodology for prioritizing the detection engineering backlog. posts.specterops.io/prioritization…
If you enjoyed this thread, please: 1. Subscribe to my newsletter: tessardavis.com/newsletter/ 2. Retweet the first tweet of the thread: twitter.com/TessaRDavis/st…
5\ METHOD 3: Review Azure Sign-in Logs or UAL These will show logons into a user account originating from the malicious application. It's important you do Method 2 before Method 3 so you can get the application object ID and application name to make this high-fidelity ;)

Cobalt Strike ain't 💩 Let's chat about how to unravel Cobalt Strike and deny the adversary further access As ALWAYS, I am showing you data so fresh out the kitchen it hasn't even been cleared by ThreatOps Director @MaxRogers5 👀🧑🍳 🧵
Lateral movement with Outlook + WMI COM objects


Building out a #ThreatHunting program can be scary! @H3dTr1p shares his ‘Crawl, Walk, Run’ approach, which tactically breaks down the individual Threat Hunt building process & provides organizations a strategic option to meet their program objectives hubs.la/Q0171xb50
New Challenge -> Pwned-DC (Active Directory Case). Adversaries were able to take over the corporate domain controller. Investigate the case and reveal the Who, When, What, Where, Why, and How. cyberdefenders.org/blueteam-ctf-c… #DFIR #BlueTeam #InfoSec #CyberSecurity
Detection engineers don't just produce or apply IOCs Detection engineers transform observed activity into detection rules (which includes IOCs) E.g. when I watch talks on TA activity I write rules on a scratch pad. They usually differ from the IOCs provided with the reports.



READ OUR RESEARCH: Sockbot in GoLand - Linking APT Actors with Ransomware gangs securityjoes.com/blog Full report: …reports.s3.eu-central-1.amazonaws.com/Sockbot%2Bin%2…
United States Trends
- 1. #SpotifyWrapped 146 B posts
- 2. #CUTOSHI 3.395 posts
- 3. Pete 424 B posts
- 4. Conor McGregor 1.420 posts
- 5. Happy Birthday Dan 5.601 posts
- 6. DeSantis 44,6 B posts
- 7. #NSD25 9.275 posts
- 8. Good Wednesday 30 B posts
- 9. #wednesdayfeelings 1.918 posts
- 10. Hump Day 13,9 B posts
- 11. National Signing Day 5.542 posts
- 12. #NationalCookieDay 1.431 posts
- 13. Happy Founders N/A
- 14. Graham 108 B posts
- 15. SecDef 14,7 B posts
- 16. Welcome Home 17,2 B posts
- 17. Founders Day N/A
- 18. chappell 10,2 B posts
- 19. Apple Music 218 B posts
- 20. Secretary of Defense 93 B posts
Something went wrong.
Something went wrong.