adnan jafar
@He1l0worldmalware analyst | Red Team | Penetration Tester
Similar User

@0x1115

@tsof_relox

@DharaniSanjaiy

@k0st8

@NKO41675803

@nasara_solomon

@Divyesh4683

@D3lt4r3d

@maheshag08

@XThalach

@TodkarR

@Luvious_

@AmadouI42724755

@sql2njection
How to change your life using monk mode (Man learn to late) //Thread//🧵

Today's Training Tuesday Highlight is @MosseInstitute! They have several 100% hands-on certifications related to DFIR, OSINT and Malware Analysis including: - Certified DFIR Specialist - Cyber Defense Forensics Analyst - Cyber Defense Incident Responder - Certified Threat…

Last week, a copycat version of the popular open-source script #linPEAS was discovered to have a sneaky line of remote logging in it, this underscores the importance of checking over #opensource tools or scripts and verifying they're from the original source. In this clip,…
Malware analysis is an exciting field that can be interesting, fun, and valuable for your cybersecurity career. In The InfoSec Survival Guide, Volume 3, @_JohnHammond has compiled a quick list of tools, tips, and advice to help you begin your journey! Tools: PeStudio -…




how i unblurred the code from @CDisillusion
WOW, amazing! And scary. I guess you're getting a video shoutout!

❤️🇵🇸 The martyred Yahya Sinwar now lives rent free in every Zionist's head.

Malware code hidden inside an image in EXE file, reverse engineering analysis of a steganography method used to evade anti-virus. pelock.com/articles/code-… #malware #assembler #reversing #itsecurity #itsec #steganography #hacker #hacking #programming #programmer #virus #TechNews
How Does Pass-the-Hash Work #infosec #cybersecurity #cybersecuritytips #pentesting #redteam #informationsecurity #CyberSec #networking #offensivesecurity #infosecurity #cyberattacks #security #oscp #cybersecurityawareness #bugbounty #bugbountytips
Write-up on 1-click Exploit in South Korea's #KakaoTalk mobile chat app allowed to steal access token and remotely exfiltrate all chat messages Issue is fixed, but @dschmidt0815 haven't received reward, because only Koreans are eligible to receive bounty😲 stulle123.github.io/posts/kakaotal…
Network Evasion Techniques: unprotect.it/category/netwo… #C2 #framework #network #evasion #redteam #pwn

Join me for a chat w/ Q&A time about the new CCNA V1.1 blueprint. We'll also dig in on a few of the more challenging new topics. Hosted by Global Knowledge (zurl.co/LLzW )! Registration page: zurl.co/DNwK Sept 19th at 11 AM US Eastern time. See you then!
Hack the Orbit: Interactive Satellite CTF Online Workshop 🛰 cybernetix.academy/satellite-ctf-…

"Hack ANY Cell Phone" - Hacker Shows How Easy It Is To Hack Your Cell Phone. @patrickbetdavid @0dayCTF
💾 Save this video to quickly remember the differences.
DeadPotato DeadPotato is a windows privilege escalation utility from the Potato family of exploits, leveraging the SeImpersonate right to obtain SYSTEM privileges. github.com/lypd0/DeadPota… #cybersecurity #infosec #Windows #privilegeescalation
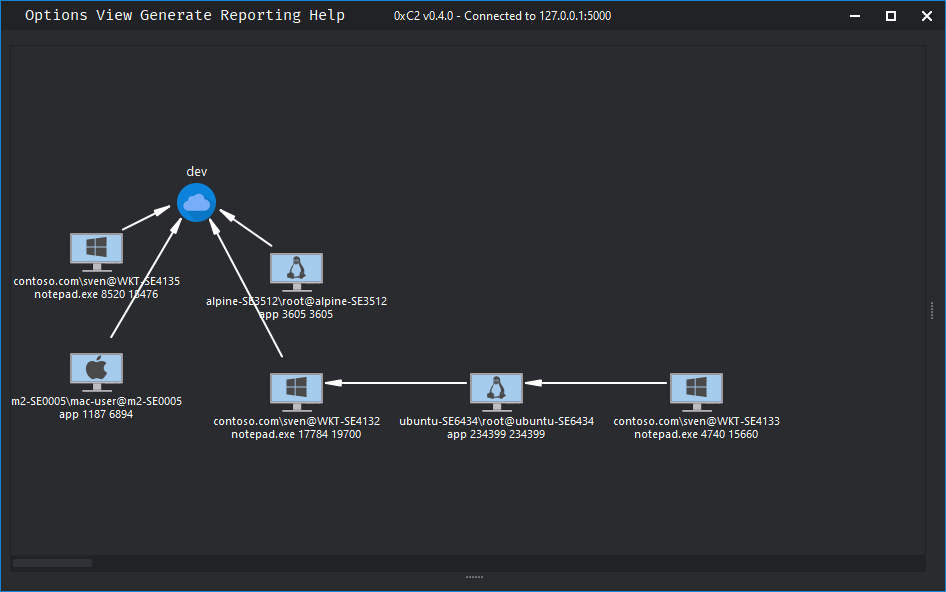
Over a year ago, I left my position at WithSecure to start a new journey, create something new, and do my own thing. Today, I'm excited to publicly announce what I've been working on all this time. Introducing 0xC2, a cross-platform C2 framework targeting Windows, Linux, and…
📢 12 Free Risk Assessment Resources Unlocking Insights, Tools, and Guidance for Safer Operations 🛡️ 𝟭. 𝗜𝗦𝗢 𝟮𝟳𝟬𝟬𝟱 (🔒 lnkd.in/gMKsx-uj) 𝟮. 𝗕𝘂𝗶𝗹𝗱𝗶𝗻𝗴 𝗮 𝗥𝗶𝘀𝗸 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 𝗣𝗿𝗼𝗴𝗿𝗮𝗺 (🎥 lnkd.in/gRSvHpX7) 𝟯. 𝗡𝗜𝗦𝗧 𝟴𝟬𝟬-𝟯𝟬…
Metasploit: Spyware generator in a pocket Attackers can generate, host and distribute malware only using a smartphone mobile-hacker.com/2024/06/20/net… #NetHunter
Today I have a great IT Audit Checklist suggestion for Active Directory❗️🤓 Don't forget to add it to your bookmarks.🤞🏻🌸 PDF Link: media.licdn.com/dms/document/m… #cybersecurity #infosec #activedirectory #windows #pentest #pentester #audit #activedirectorysecurity #checklist
United States Trends
- 1. #TheGameAwards 61,4 B posts
- 2. Ninja Gaiden 4.502 posts
- 3. Hannah Hidalgo 1.562 posts
- 4. Waldorf 1.552 posts
- 5. $LINGO 62,8 B posts
- 6. Geoff 12,7 B posts
- 7. Guerendo 5.035 posts
- 8. Paige 11 B posts
- 9. Pac-Man 5.554 posts
- 10. Astro Bot 1.461 posts
- 11. Tekken 8 6.440 posts
- 12. #WhyIChime 3.587 posts
- 13. $WMTX 2.179 posts
- 14. Shadow Labyrinth 1.182 posts
- 15. ELLA PURNELL 2.425 posts
- 16. Ray Epps 16,1 B posts
- 17. #TNFonPrime 1.849 posts
- 18. Best Family Game 1.338 posts
- 19. #BBMAs 67,1 B posts
- 20. #ShootingStar N/A
Who to follow
-
 0xeleven@AFK
0xeleven@AFK
@0x1115 -
 Tsof
Tsof
@tsof_relox -
 WaterBucket
WaterBucket
@DharaniSanjaiy -
 Kosta B.
Kosta B.
@k0st8 -
 しゃう
しゃう
@NKO41675803 -
 Solomon Nasara
Solomon Nasara
@nasara_solomon -
 Divyesh Bhesaniya 🇮🇳
Divyesh Bhesaniya 🇮🇳
@Divyesh4683 -
 Delta Red
Delta Red
@D3lt4r3d -
 Mahesh Anthappagudem
Mahesh Anthappagudem
@maheshag08 -
 xThalach
xThalach
@XThalach -
 🏃Snehal
🏃Snehal
@TodkarR -
 Luvious
Luvious
@Luvious_ -
 aibrahim
aibrahim
@AmadouI42724755 -
 Kauan M.
Kauan M.
@sql2njection
Something went wrong.
Something went wrong.