Ahmet Payaslıoğlu
@Computeus7Incident Responder | Threat Hunter
Similar User

@batcain_

@PRODAFT

@0xabc0

@furk4n0zturk

@ahmettgurell

@DmitriyMelikov

@ccelikanil

@h4ck2s3c

@kaganisildak

@oktayyilddiz

@caliskanfurkan_

@FeCassie

@meto0x3d

@brkalbyrk7

@hebun_2107
Hackers abuse Avast anti-rootkit driver to disable defenses - @billtoulas bleepingcomputer.com/news/security/…">bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…">bleepingcomputer.com/news/security/…
Blog Series: Anti-Forensics techniques on Windows, Linux & Azure💕 Bypassing Windows event logging via native APIs inversecos.com/2022/03/window… Detecting forged logs in Entra ID inversecos.com/2023/01/detect… Timestomping all registry key write times inversecos.com/2022/04/malici… Timestomping…


YARA-X 0.11.0 has been released! github.com/VirusTotal/yar…
Ready for some Thanks Giving reading? Nighthawk 0.3.3 Evanesco is now live for customers nighthawkc2.io/evanesco/ #happythanksgiving

Hunting ClickFix Fake Captchas? 🕵️♂️ Use these TI Lookup queries in @anyrun_app to track recent submissions: 🔎 commandLine:"*captcha*" AND commandLine:"*mshta*" 🔎 commandLine:"*captcha*" AND commandLine:"*PowerShell*" Stay ahead of the game! 🚀 #ThreatIntelligence


It is really interesting to find anti-VM techniques being used by threat actors in the wild. This is a PowerShell script protecting a #Lumma Stealer build and being spread on YouTube videos. In this case, this was enough to make @anyrun_app to fail based on Screen Resolution



~100 of new threat hunting content (ES|QL, Osquery) for windows, macos, cloud and more ... github.com/elastic/detect…

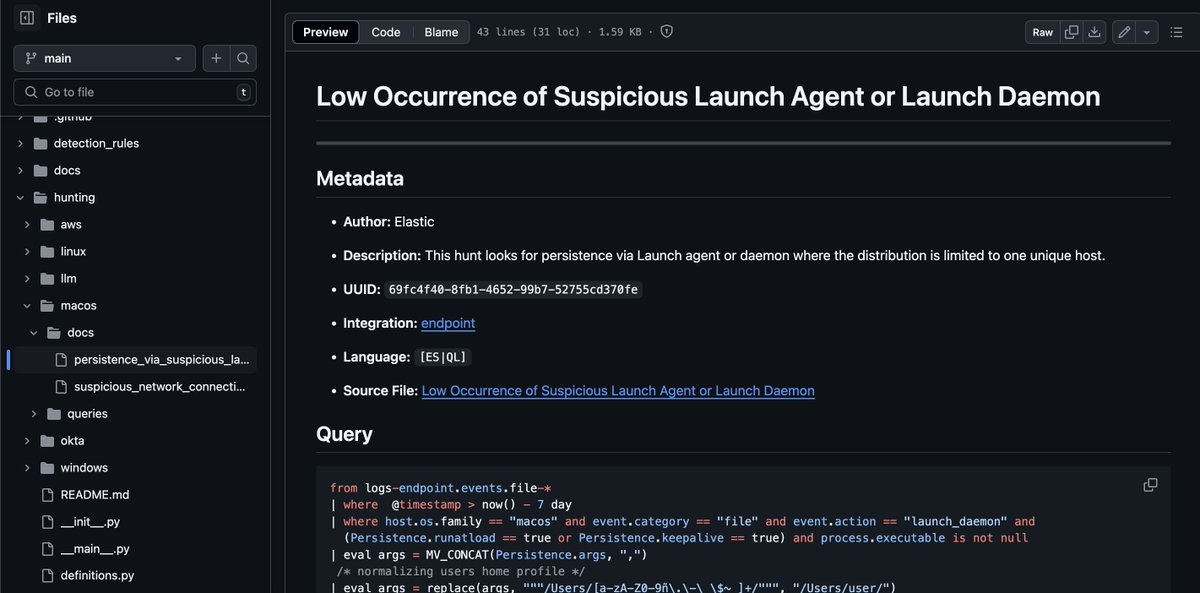
Threat hunting just got easier! This new repo of detection rules is crafted by our veteran detection engineers and powered by different Elastic query languages. Get the details of what’s included and see the future of this repo here: go.es.io/4h2JsTX #ElasticSecurityLabs
Likely StealC URLs on UrlScan👀 These can be found by searching URLScan for pages containing an IP (no domain), and ending in a 16 character .php file. urlscan.io/search/#page.u…


I created the first draft of a website for the EDR telemetry project to help people quickly compare vendor telemetry visibility. What do you think about it? Are there any specific features you want to see for the website? Built with ChatGPT 4o with canvas (wanted to test it…
🧵1/ If you're like me, you get tired of fighting Windows...from a win box for #malware analysis, or preventing Windows from updating when you don't want it to. Enter Windows Firewall Control (binisoft.org/wfc)

I’m in love with RansomLook, created by @adulau and Fafner! ❤️ There are multiple resources related to ransomware activities, and there's even an API so you can integrate the data directly into your backend! 🔥 Check it out: ransomlook.io #ransomware #threatintel



See that ad for Slack? It's actually a malicious site that tricks Mac users into downloading an infostealer.

In one of the #MalwareAnalysis communities I’m in, we were talking about Go malware. Someone mentioned CAPA as a good tool. I have to say, it’s really helpful for finding the 50kb of interesting code buried inside a 5mb Go binary 😎What other tools do you use?

The DFIR Report's latest analysis focuses on an intrusion that started with the execution of a Cobalt Strike beacon and ended in the deployment of BlackSuit ransomware. thedfirreport.com/2024/08/26/bla…

We just released Hayabusa 2.17.0 and Takajo 2.6.0 at Taiwan's greatest security conference: HITCON! Hayabusa has support for the new Sigma V2 modifiers and many various enhancements. Takajo has a new HTML summary report feature! github.com/Yamato-Securit… github.com/Yamato-Securit…



Oh, so you track ransomware tools? OK, name every one. Me:

Updated List of 109 Domains Potentially Impersonating Crowdstrike🍿 (All registered in the last 7 days, some might be legitimate) areyouaffectedbycrowdstrike[.]info britishairways[.]crowdstrike[.]feedback crowdstrike-ab1[.]pages[.]dev crowdstrike-bsod[.]co…

Adding a bunch more suspicious #crowdstrike domains registered in the last 7 days. crowdstrike-bsod[.]co crowdstrike-bsod[.]com crowdstrike-fix[.]zip crowdstrike-helpdesk[.]com crowdstrike-out[.]com crowdstrike[.]blue crowdstrike[.]bot crowdstrike[.]cam crowdstrike[.]ee…

Hello everyone, as promised, we are back with the first results of our investigation. any.run/cybersecurity-… In this report, we present the facts and timeline of the incident. We’ve also added our response actions. More updates will be provided later as we make further progress…
New version of ReverserAI, shortly before our @reconmtl talk: * supports a second, more powerful local LLM * applies static analysis to enhance results of GPT-based function renaming * various minor improvements and bug fixes Plugin: github.com/mrphrazer/reve…
United States Trends
- 1. $LFDOG 5.365 posts
- 2. #SmallBusinessSaturday 4.385 posts
- 3. $CUTO 7.041 posts
- 4. Las Palmas 41,6 B posts
- 5. Real ID 7.325 posts
- 6. Lando 45 B posts
- 7. #Caturday 5.986 posts
- 8. Go Bucks 1.867 posts
- 9. Gameday 13,2 B posts
- 10. #ShopSmall 3.033 posts
- 11. Go Blue 12,8 B posts
- 12. #SaturdayVibes 6.098 posts
- 13. Trudeau 191 B posts
- 14. Bournemouth 7.988 posts
- 15. Grok 54,2 B posts
- 16. Good Saturday 33,4 B posts
- 17. Zelensky 134 B posts
- 18. #TheGame N/A
- 19. Barcelona 118 B posts
- 20. Fermin 10,7 B posts
Who to follow
-
 batcain
batcain
@batcain_ -
 PRODAFT
PRODAFT
@PRODAFT -
 Ahmet Bilal Can 🦔
Ahmet Bilal Can 🦔
@0xabc0 -
 Furkan Öztürk
Furkan Öztürk
@furk4n0zturk -
 Ahmet GÜREL
Ahmet GÜREL
@ahmettgurell -
 Dmitry Melikov
Dmitry Melikov
@DmitriyMelikov -
 anıl
anıl
@ccelikanil -
 Muhammet Gedik
Muhammet Gedik
@h4ck2s3c -
 Kağan IŞILDAK
Kağan IŞILDAK
@kaganisildak -
 Oktay
Oktay
@oktayyilddiz -
 Furkan
Furkan
@caliskanfurkan_ -
 Fatih ERDOĞAN
Fatih ERDOĞAN
@FeCassie -
 meto
meto
@meto0x3d -
 Berk Albayrak
Berk Albayrak
@brkalbyrk7 -
 Hebun Kurt
Hebun Kurt
@hebun_2107
Something went wrong.
Something went wrong.