
BlueSkjaldborg
@BlueSkjaldborgTales for the Skjaldes ⚠️ From high level to low level and back. Everything regarding #blueteam. 🆙️
Similar User

@LucyIsOpal

@assume_breach

@shantanukhande

@Tw1sm

@collfuse

@ZohyrC

@homme_fait

@gl4ssesbo1

@vp_aria

@innateself

@ferdosisla23572

@Steelers5821

@dashbak

@astra_tours

@MapisAdams2
This was a fun one! Really enjoyed it. @ACEResponder
📢 New Challenge: Locked Up Your domain is infected with ransomware. Take on a unique attack path in this beginner-friendly challenge. #ThreatHunting #DFIR aceresponder.com/challenge/lock…
Periodic Table of Windows Events #ThreatHunting #DFIR #Windows

How Component Object Model (COM) works. #ThreatHunting #DFIR #Windows #Microsoft

How Windows security descriptors work. #ThreatHunting #DFIR #Windows #ActiveDirectory

Interesting challenge @ACEResponder!
📢A new challenge is now available on ACEResponder.com! Investigate an incident that spans a Windows and Linux server environment. #ThreatHunting #DFIR aceresponder.com/challenge/blin…

How character classes work in regular expressions.
How Windows access tokens work. #ThreatHunting #DFIR #Windows

How Kerberos authentication works across domain trusts. #ThreatHunting #DFIR
Don't sleep on @ACEResponder labs and courses, they are very well done and educational.
📢A new challenge is now available on ACEResponder.com! Take on a hybrid #Entra #Azure AD compromise #ThreatHunting #DFIR aceresponder.com/challenge/intu…
📢A new challenge is now available on ACEResponder.com! Take on a hybrid #Entra #Azure AD compromise #ThreatHunting #DFIR aceresponder.com/challenge/intu…
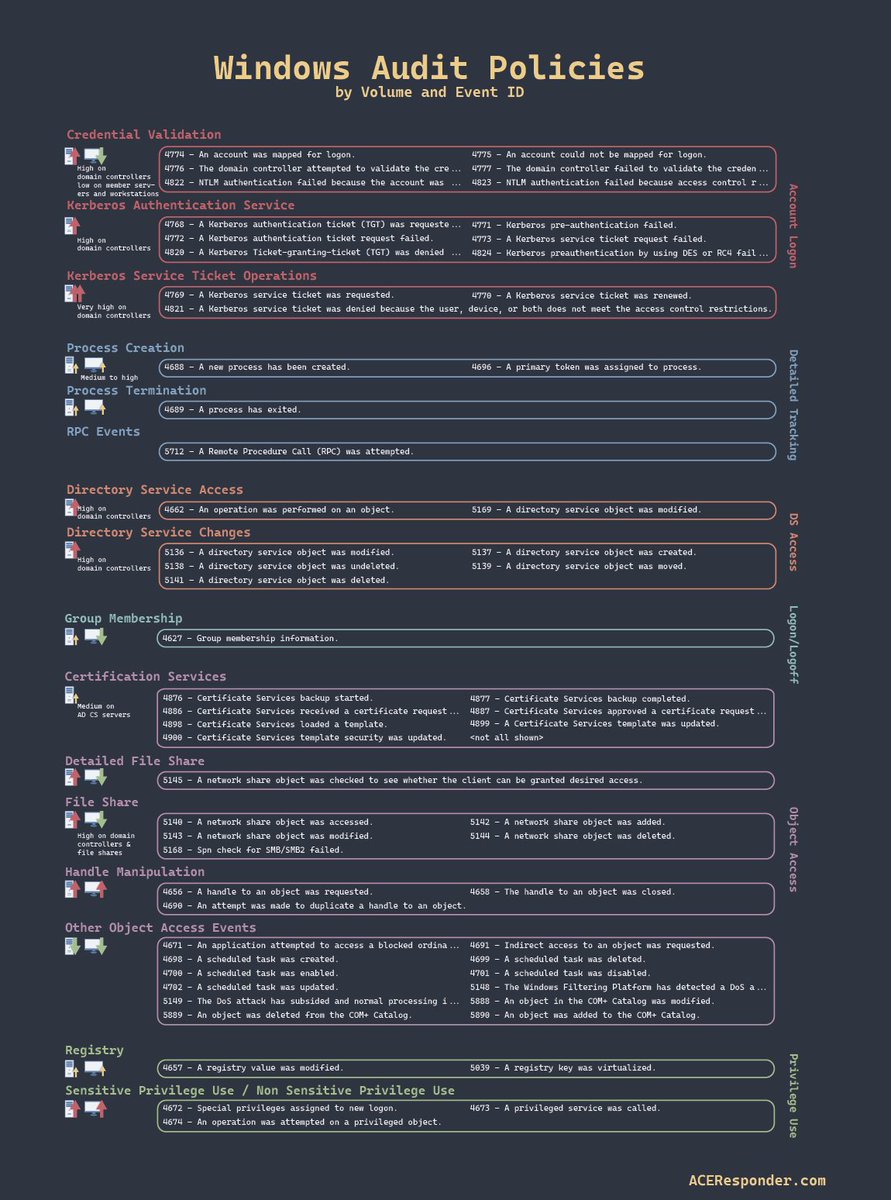
Windows audit policies, the events they enable and the relative volume of events they generate #ThreatHunting #DFIR
Threat Hunting Techniques: Clustering 💠 #ThreatHunting #DFIR

Threat Hunting Techniques: Searching 🔍 #ThreatHunting #DFIR

📢New Learning Module! #ThreatHunting #DFIR aceresponder.com/learn/hunting-…
A skeleton key attack patches authentication functions in LSASS. This gives the attacker a master password without changing any user passwords. #ThreatHunting #DFIR
How Kerberos authentication works when the service is configured for unconstrained delegation. #ThreatHunting #DFIR
DCOM lateral movement using Excel ActivateMicrosoftApp() #ThreatHunting #DFIR
United States Trends
- 1. Ole Miss 3.144 posts
- 2. Indiana 56,4 B posts
- 3. Jaxson Dart 5.232 posts
- 4. Gators 14,4 B posts
- 5. Ohio State 37 B posts
- 6. Lane Kiffin 3.772 posts
- 7. Billy Napier 2.858 posts
- 8. Ryan Day 6.075 posts
- 9. Wayne 131 B posts
- 10. UMass 5.682 posts
- 11. Howard 25,2 B posts
- 12. Rutgers 4.207 posts
- 13. Buckeyes 12,3 B posts
- 14. Lagway 6.743 posts
- 15. Caleb Downs 7.737 posts
- 16. Gerard Martin 20,3 B posts
- 17. Surgeon General 161 B posts
- 18. #GoBucks 7.840 posts
- 19. Devin Neal N/A
- 20. Cignetti 5.630 posts
Who to follow
-
 Connected
Connected
@LucyIsOpal -
 assume_breach
assume_breach
@assume_breach -
 Shantanu Khandelwal
Shantanu Khandelwal
@shantanukhande -
 Matt Creel
Matt Creel
@Tw1sm -
 collfuse.com 🇨🇭
collfuse.com 🇨🇭
@collfuse -
 zohyr caicedo
zohyr caicedo
@ZohyrC -
 L’homme qui fait trembler les autres
L’homme qui fait trembler les autres
@homme_fait -
 Bleon Proko
Bleon Proko
@gl4ssesbo1 -
 AriaVP♏
AriaVP♏
@vp_aria -
 Beverly Wells
Beverly Wells
@innateself -
 ferdosisla
ferdosisla
@ferdosisla23572 -
 Steelers5821
Steelers5821
@Steelers5821 -
 dash bs
dash bs
@dashbak -
 Astra-Tours - mit #zugstattflug nach Osteuropa!
Astra-Tours - mit #zugstattflug nach Osteuropa!
@astra_tours -
 Mapada###
Mapada###
@MapisAdams2
Something went wrong.
Something went wrong.





















































































