1nv0k3r
@1nv0k3r_Focus on Software Security, IoT Security, and Fuzz, independence researcher, developer, hearing handicap L2.
Similar User

@1chig0_sec

@bestswngs

@e4stjun

@P4nda20371774

@Eqq111e

@4uuu_Nya

@wywwzjj

@xiumulty

@LeoQ7_

@0chencc

@0xmuhe

@Q1ngShan

@peri0d4
CVE-2022-39197 Cobalt Strike < 4.7.1 RCE Analyze mp.weixin.qq.com/s/Eb0pQ-1ebLSK…
Chinese new year gift: Wine IDA Pro in Docker, with Jupyter Notebook support github.com/NyaMisty/docke…
I have reversed all the code of certificate validation but does not found any bug wtf😰
In our 1st #Pwn2Own #AfterDark entry this evening, @Synacktiv used an improper certificate validation and a stack-based buffer overflow to compromise the NETGEAR router via the WAN interface. They earn $20,000 and 2 critical Master of Pwn points. #P2OAustin
wtf, 当初考研看到IP数据包分片这块就感觉很容易出漏洞, 但是转念一想全世界应该一堆大佬盯着这块, 没想到真有啊就 zh-cn.tenable.com/blog/microsoft…
What about change the Black Hat to Block Hat lol
你一定要喊吗
Introducing the GeForce RTX 2080 Ti Cyberpunk 2077 Edition. We made 77 for our community. Want one? Here's how: 1. RT this video. 2. Tag a gamer who is as excited as you about Cyberpunk 2077 in the replies with #RTXOn 3. If selected, you BOTH win these limited edition GPUs!
I'm releasing ghidra scripts that I made for pwn and reversing tasks, starting with this set of scripts to replace linux/libc magic numbers with readable names for aarch64, amd64/i386, arm/thumb, hppa, m68k, mips, ppc, ppc64, sh, sh4, sparc and sparc64. github.com/0xb0bb/pwndra
Geared up! #TianfuCup 2019 PWN contest kicks off at 9am tomorrow (GMT+8). Stay tuned~

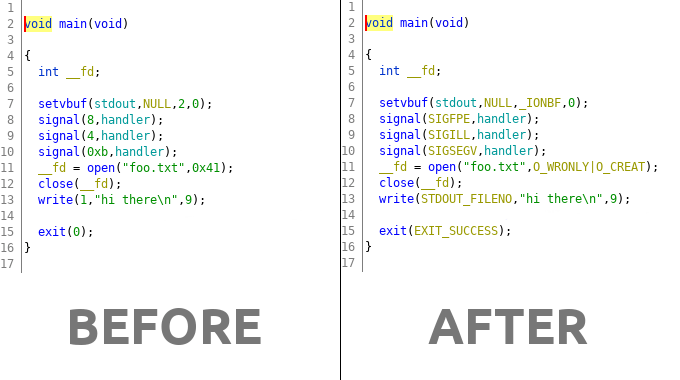
VMware just repairs the vulnerability I use in my exploit :(
"Correlation is not causation"
The co-author who didn’t do anything
cloudflare «XSS» payload to bypass protection. 🦍 {` <body \< onscroll =1(_=prompt,_(String.fromCharCode(88,83,83,32,66,121,32,77,111,114,112,104,105,110,101)))> ´} #BugBounty #BugBountyTip #WAF #infosec
cve-2019-16928 I have a PoC now, and I am try to make it to RCE. 😝

United States Trends
- 1. Astro Bot 105 B posts
- 2. GOTY 73,4 B posts
- 3. $LINGO 70,3 B posts
- 4. Ciri 75 B posts
- 5. #TheGameAwards 471 B posts
- 6. Happy Friday the 13th 3.198 posts
- 7. Naughty Dog 59,7 B posts
- 8. Okami 118 B posts
- 9. 49ers 59,5 B posts
- 10. Deebo 36,7 B posts
- 11. Purdy 22,2 B posts
- 12. Witcher 97,5 B posts
- 13. Elden Ring 197 B posts
- 14. Rams 43,5 B posts
- 15. Niners 10,8 B posts
- 16. Arcane 276 B posts
- 17. Clive 36 B posts
- 18. Fallout 45,5 B posts
- 19. Wukong 34 B posts
- 20. Geralt 9.140 posts
Something went wrong.
Something went wrong.