Leigh
@0x1337LeighI retweet posts related to #OSINT 🔍, #Cybersecurity , #RedTeam 🔴, #BlueTeam and sometimes #AI & #Privacy
Similar User

@Hack3rRunway

@Splintersfury

@BreakEvenCrypto

@evdaycomputer

@wakesupat10am

@theshyhat

@0x90b

@AcidRaZor

@martin_holzman

@SimpScientist23

@TropicalSec

@Suresh_3_6

@0x04E1

@mattyakel

@mr_alwadi
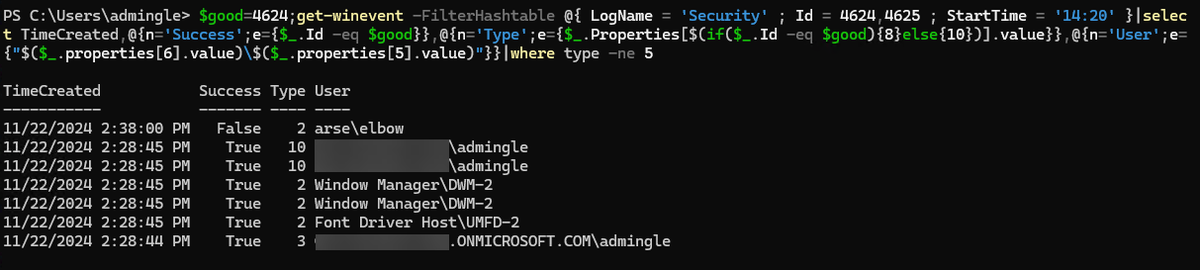
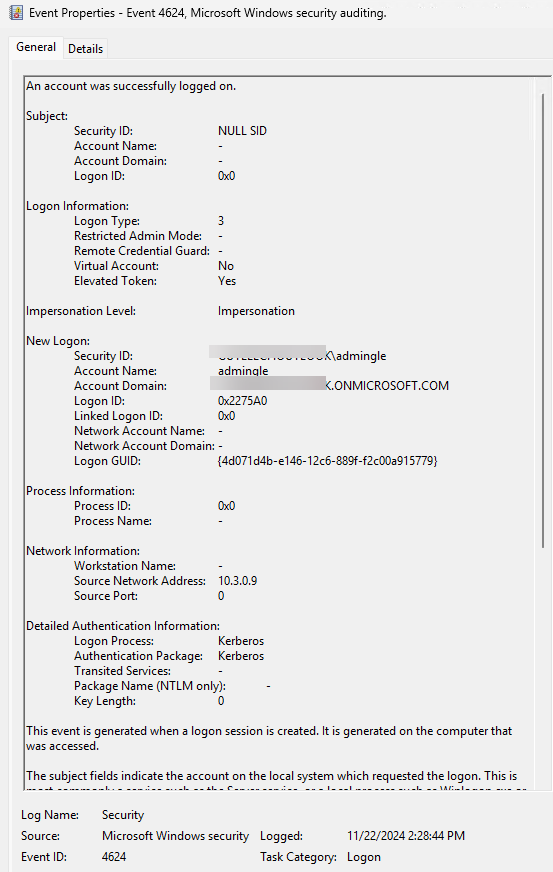
If you have logon success/failure auditing enabled, this #PowerShell will show you events $good=4624;get-winevent -FilterHashtable @{ LogName = 'Security' ; Id = 4624,4625 ; StartTime = '14:20' }|select TimeCreated,@{n='Success';e={$_.Id -eq…

Resource is the 6th box I've had released on @hackthebox_eu! There's some PHP webshell using PHAR filter to read in a Zip, finding credentials in a har file, bash glob brute force, and a lot of SSH certificates! 0xdf.gitlab.io/2024/11/23/htb…
As promised here is part 1 of removing malware signatures in C part 2 will cover more advanced topics like polymorphic code and PIC youtube.com/watch?v=45-VII…
Create your own C2 using Python series - Part 1 ! g3tsyst3m.github.io/c2/python/Crea…
Happy to share #Splunk Threat Research Team #STRT, blog that delve into Braodo Stealer, a Python-based malware designed to steal sensitive info. and leverage popular developer platform to distribute its payload . 😊 splunk.com/en_us/blog/sec…
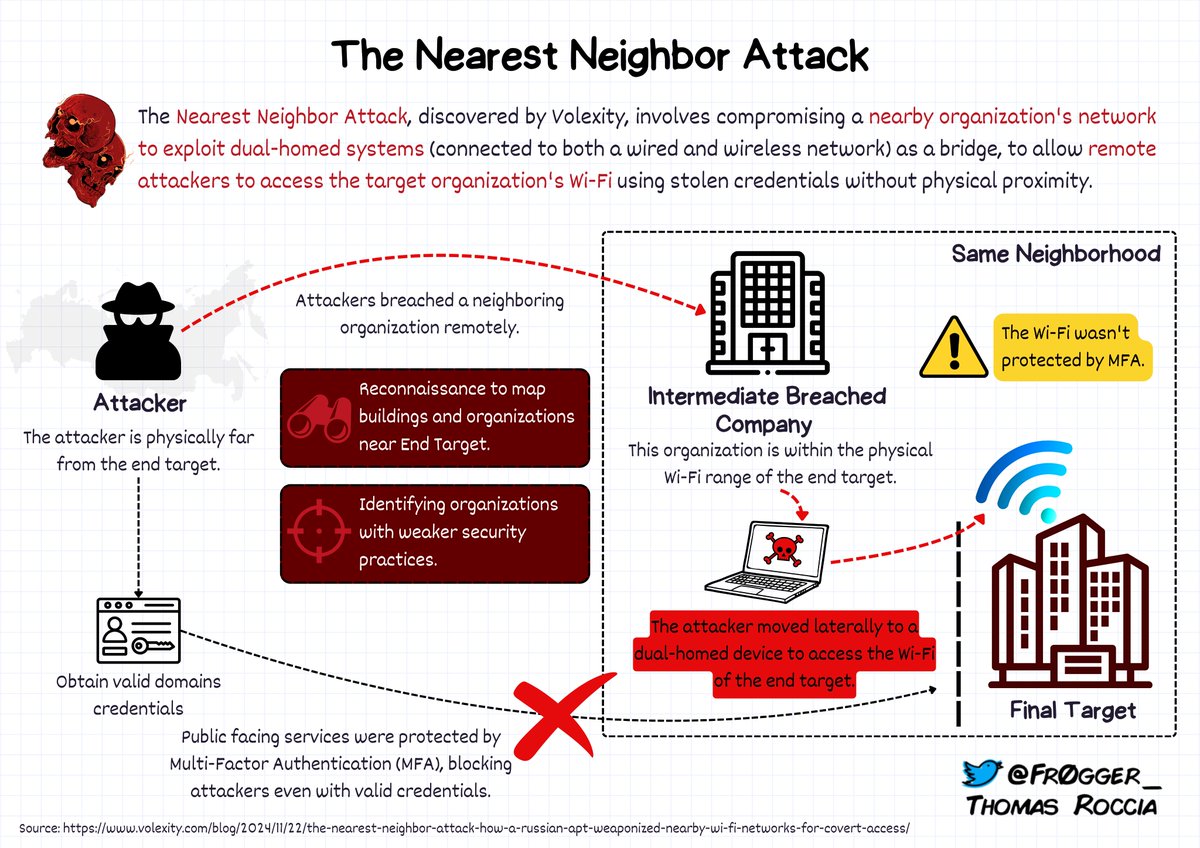
🤓 I was reading the fascinating report from @Volexity about the Nearest Neighbor Attack presented at @CyberWarCon To keep it documented, I created a quick overview to explain how works the attack to complement their blog post 👇 #threatintel #infosec
Releasing full 2+hr video of my browser exploitation workshop from VXCON 2024: youtube.com/live/b9OhamkAY… In which I show what goes inside the mind of a skilled hacker while exploiting a highly non-trivial vulnerability in v8, from zero to exploit concept. Especially this workflow…
Had a great convo with David Monnier @teamcymru on the Future of Threat Intelligence podcast. We discussed the evolution of ransomware tactics along with the rise of multi-extortion strategies bit.ly/4fJPOqg #futureofthreatintelligence #cybersecurity #threatintelligence

A new blog drop like promised! 🔥 We are actively monitoring and tracking #SMOKEDHAM at @TRACLabs_ Okay, now I am hungry. trac-labs.com/who-ordered-th…
Initial Access Brokers & Brute Force Attacks 💰


💲 Initial access sale leads to LockBit ransomware. Initial access brokers get valid credentials through brute force attacks on #RDWeb (Remote Desktop Web) services 📈, widely seen lately. An IAB opsec error revealed the name of the affected company.



Check out my good friend @slothintel's latest insights on Palo Alto exploitation (CVE-2024-0012 & CVE-2024-9474) at @AWNetworks 🐺. Yes, POCs are out there 👀
Arctic Wolf has observed multiple intrusions across a variety of industries involving Palo Alto Network firewall devices. On our blog, Arctic Wolf Labs provides a deep dive into what it has observed in these intrusions. #EndCyberRisk arcticwolf.com/resources/blog…
ADCS Attack Techniques Cheatsheet for all of you lazy folks who prefer colored tables over reading a bunch of articles just to find some specific information: bit.ly/adcs-cheatsheet
[1/2] Latest Phishing Campaign by #SideCopy #APT Targeting Indian Govt. File: MoM held by Defence Secretary Dated 18 November.pdf MD5: e6a41f0d41cc5324303b0d0034a7de41 --> email.gov.in.indiagov.ws/service/home/?… Sample: file.io/lwfCLy69Lzmi


📈 We've seen a spike in LummaC2 stealer activity over the last two months. Get detection guidance and more in this month's edition of Intelligence Insights. redcanary.com/blog/threat-in…

🔥 New open-source #Suricata rules 🔥 rules.ptsecurity.com For over a year now I’ve been sharing interesting #malware findings in network traffic here! Today I want to share our project PT Rules🎉 (there are many rules written for the threats I indicated in my tweets below⬇️)

Wanna become malware developer and understand how malware works ?! Read these 7 books: * Windows Internals Part 1/2 * Practical Malware Analysis * Malware Development for Ethical Hackers * Malware Data Science * Attacking Network Protocols * C++ All-in-One For Dummies 4th…




Vietnamese threat actors 🇻🇳 are highly interested in Facebook business accounts. Why? Because they can run fraudulent advertisement campaigns and earn thousands of dollars per day. A great research by @GroupIB group-ib.com/blog/tracing-t…
Unusual mid-week C2 update for SocGholish... *.cases.pcohenlaw.com/merchantServices

Innovation occurs as a response to action–something that #ElasticSecurityLabs saw firsthand with GRIMRESOURCE. Check out how attackers utilized specially crafted MSC files for full code execution: go.es.io/4fPcR2A
Dive into how DarkPeony's consistent use of certificates reveals ongoing infrastructure activity, indicating consistent operations across different regions. 🌐 Read the details in our latest blog post! hunt.io/blog/darkpeony…
United States Trends
- 1. Ohio State 25,4 B posts
- 2. Indiana 36,2 B posts
- 3. $AROK 6.452 posts
- 4. Wayne 126 B posts
- 5. Howard 22,9 B posts
- 6. #daddychill 2.405 posts
- 7. Ryan Day 3.772 posts
- 8. Gus Johnson 1.017 posts
- 9. Buckeyes 7.197 posts
- 10. Hoosiers 7.537 posts
- 11. #iufb 4.392 posts
- 12. $MOOCAT 7.764 posts
- 13. Tottenham 45,3 B posts
- 14. UMass 3.130 posts
- 15. DJ Lagway 1.798 posts
- 16. Man City 41,4 B posts
- 17. Surgeon General 115 B posts
- 18. Chip Kelly N/A
- 19. Carnell Tate N/A
- 20. Cody Simon N/A
Who to follow
-
 Hack3r Runway is off to bluer skies
Hack3r Runway is off to bluer skies
@Hack3rRunway -
 Splintersfury
Splintersfury
@Splintersfury -
 BreakEven 🫥
BreakEven 🫥
@BreakEvenCrypto -
 Eric Berry
Eric Berry
@evdaycomputer -
 Wathsala Vishwajith
Wathsala Vishwajith
@wakesupat10am -
 theShyHat
theShyHat
@theshyhat -
 Bernard SB
Bernard SB
@0x90b -
 AcidRaZor
AcidRaZor
@AcidRaZor -
 Martin Holzman
Martin Holzman
@martin_holzman -
 SimpScientist V2.024
SimpScientist V2.024
@SimpScientist23 -
 0xTpSec
0xTpSec
@TropicalSec -
 Suresh
Suresh
@Suresh_3_6 -
 Andrés.
Andrés.
@0x04E1 -
 /dev/matt
/dev/matt
@mattyakel -
 Mr Alwadi
Mr Alwadi
@mr_alwadi
Something went wrong.
Something went wrong.